Home Router being a Part of Botnet?
Hello this is Shikapon at the Incident Analysis Team at JPCERT/CC. I am managing a network threat monitoring system called "TSUBAME" which has been in operation since 2007.
With sensors distributed in 19 economies in the Asia Pacific Region, the system is providing a common platform for the TSUBAME Project member teams for monitoring, information sharing and analysis.
TSUBAME helps us to reveal hard to detect attacks that are on-going such as DDoS and/or signs of attack before the situation becomes critical.
Today, I would like to share with you my latest observation via TSUBAME and its analysis. It is about the sudden increase of packets to Port 23/tcp (Telnetd
What I first observed - Increase of Scans to Port 23/tcp
In early December, a sudden increase of packets to Port 23/tcp (Telnetd
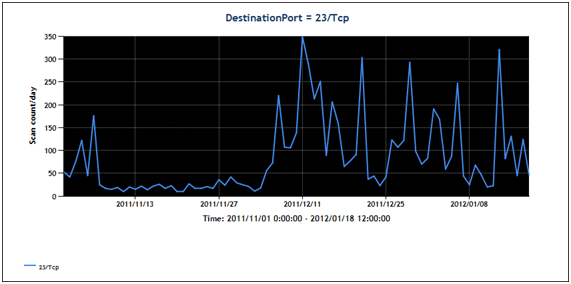
Figure 1. Volume of Port23/TCP Scanning Activity
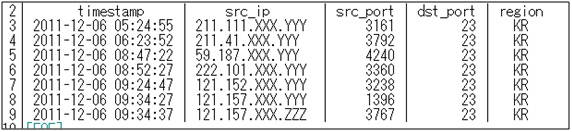
Figure 2. Excerpt of Port23/TCP Scanning Log
You can see from Figure 1 that packets to Port 23/tcp in December 2011 and January 2012 have gone up about 10 times more than that of November 2011.
Figure 2 shows that the scans occurred in 6 December 2011 were carried out by multiple IP addresses in South Korea (KR).
What interested me
Traffic surge to a specific port is not quite unusual. But for the following reasons, I thought this scanning case is very unique and something I should keep our eye on.Firstly, comparing Figure 1 (Port23/TCP Scanning Activity) and Figure 3 (Port23/TCP Scanning Activity originated in South Korea) it would be easy to tell that the large amounts of packets were originated specifically from South Korea (KR) which is not so common. About 90% of packets come from IP range assigned to South Korea (KR). Scans from other economies were being observed as well, such as United States, Mainland China and Chinese Taipei.
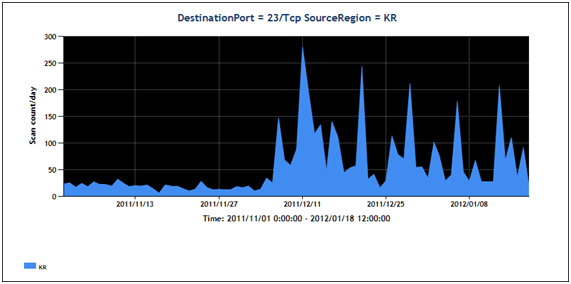
Figure 3. Volume of Port23/TCP Scanning Activity originated in South Korea
Secondly, the scanning activities are conducted in a very organized manner. I’ve checked few hundreds of scan sources but it seems these IPs work together not to scan one target by multiple IP. It seems that they are a part of botnet and conduct telnet scan by a command from their master (C&C server).
Lastly, it seems that the sources of packets were neither from PCs nor servers, but mostly from home routers. Some of the packets were from DSL modems and set-top boxes such as media servers as well. I have attempted to trace several sources and found out that most of them are listening on Port 23/tcp. I found it interesting that most of the source IPs in South Korea prompts the "evb3.voip.com" banner. I hope the readers will help me to identify the manufacturer of this product. It should be a common product in their economy.
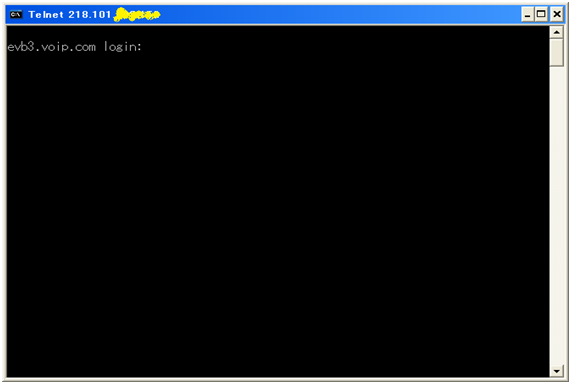
Figure 4. Telnet Login Banner (Scan Source IP)
Conclusion
Botnets are one of the most significant network security threats. Information security communities are currently working hard to eliminate infected PCs on the Internet. But we all should realize that it is not just PC - any IP reachable devices such as smartphones, tablets and even the home router could be controlled by malicious outsiders if once infected.
As I investigated further, I noticed that the free tools to turn a home router to a bot client are widely available online now. They support ARM and other architectures. I’ve actually encountered some devices that were compromised by using one of those tools. Once becoming a part of botnet, home routers starts to scan Port 23/tcp of their neighborhood.
As your home router (or DSL modem and set-top box) may be compromised without even noticing, I would like to encourage the readers to disable the telnet service on such devices.
If your find it difficult to configure so for reasons, try these:
- Filter source IP address that can connect to WAN interface of your router.
- Set a stronger password (Do not use default or easy-to-remember password like "admin", "root" and "linksys" )
- Update the firmware.
If you have any inquiries on this topic or TSUBAME, please contact me at tsubame-sec(at)jpcert.or.jp.
- Keisuke Shikano (Shikapon)

