Increase in Possible Scan Activity from NAS Devices
Happy holidays to all, this is Tetsuya from Watch and Warning Group. Today, I would like to share a recent, remarkable trend discovered through TSUBAME sensors.
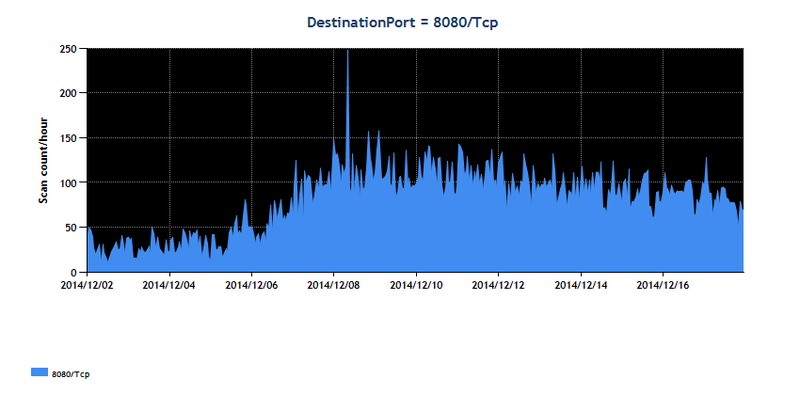
In TSUBAME, we have observed a significant increase in packets destined to 8080/TCP since December 5th, 2014. When accessing source IP addresses using a web browser, the admin login screen for NAS devices provided by QNAP was seen in many cases for IP addresses from certain regions.
[Figure 1: Scan count per hour observed at 8080/TCP from December 2nd, 2014 onwards (Source: TSUBAME)]
Below are some characteristics that we noticed from TSUBAME data:
- Increase in packets to Port 8080/TCP since December 5th, 2014
- The TTL value for most of the packets were between 30 - 59
- A scan attempt sends 1 - 2 packets (the second packet is a re-send)
- A source IP does not continuously scan a particular destination IP (The majority scans only once)
Also we were able to verify the following after checking some of the source IP addresses:
- When accessing Port 80/TCP of the source address, a redirect to Port 8080/TCP occurs and the admin login screen of QNAP NAS is shown
- The QNAP firmware looks to be version 4.1.0 or earlier (Information taken from the screen that is shown. 4.1.0 and earlier are affected by Shellshock) (*1)
Using an environment separate from TSUBAME to check the packets sent by an infected QNAP device, we saw the following request (there are several types of requests).
[Figure 2: Sample request from infected device (Source: JPCERT/CC)]
When a QNAP NAS device using a vulnerable version of firmware receives this request, the Shellshock vulnerability is leveraged to download a malicious attack program over the Internet and be infected by malware (*2, *3). Once infected, it begins to search for other vulnerable NAS devices. As a result of this activity, a large number of NAS devices were infected and we believe this is the reason for the sudden increase in packets to 8080/TCP.
The vendor has released firmware to address the Shellshock vulnerability. If you have yet to apply the update, we recommend that you first check (*2) whether you have been infected or not.
JVN#55667175 QNAP QTS vulnerable to OS command injection (*1)
https://jvn.jp/en/jp/JVN55667175/
The Shellshock Aftershock for NAS Administrators (*2)
Worm Backdoors and Secures QNAP Network Storage Devices (*3)
https://isc.sans.edu/forums/diary/Worm+Backdoors+and+Secures+QNAP+Network+Storage+Devices/19061
An Urgent Fix on the Reported Infection of a Variant of GNU Bash Environment Variable Command Injection Vulnerability (*4)
http://www.qnap.com/i/en/support/con_show.php?cid=74
Thank you for reading, and we wish you all the best for the coming year.
- Tetsuya Mizuno