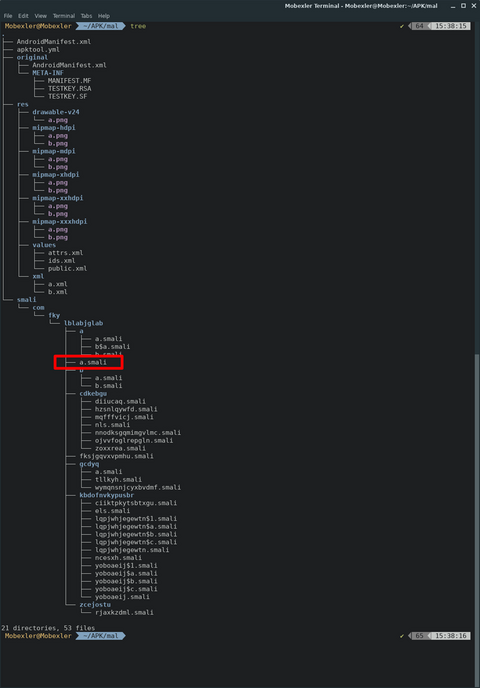
When dynamically analyzing Android malware, it is currently difficult to follow its code using debuggers unlike Windows malware. Although there is a technique [1] to hook a method dynamically by Frida [2], obtaining the in-progress state of the method is still difficult, and since Frida is not a tool dedicated to Android, only limited information can be obtained. In this article, I introduce smali gadget injection technique as a more...
List of “Security Technology”
-
-
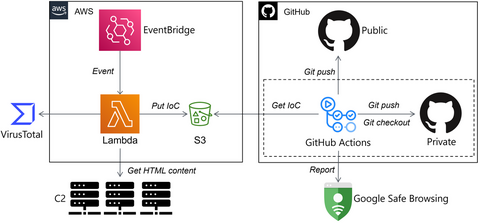
I believe that automating analysis is a challenge that all malware analysts are working on for more efficient daily incident investigations. Cloud-based technologies (CI/CD, serverless, IaC, etc.) are great solutions that can automate MAOps efficiently. In this article, I introduce how JPCERT/CC automates malware analysis on the cloud, based on the following case studies. Malware C2 Monitoring Malware Hunting using Cloud YARA CI/CD system Surface Analysis System on Cloud Memory...
-
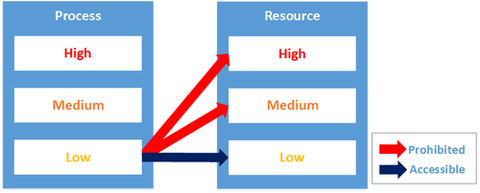
In most of the targeted attack cases, often multiple computers get infected by malware, rather than just a single computer, and attackers continue compromising other computers across the network, including important servers. For this “lateral movement” purpose, password hash is often targeted. In order to enhance protection against such information theft, LSA Protection Mode for Windows 8.1 etc. and Credential Guard for Windows 10 Enterprise have been introduced. In this...
-
Our previous article “Enhanced Protected Mode in Internet Explorer” (published in August 2015) introduced that running the browser with Enhanced Protected Mode in 64-bit mode is effective in the protection against attacks exploiting vulnerabilities. This entry will verify the effect of “AppContainer” against attacks, which is another function related to Enhanced Protected Mode for Windows 8 and later. AppContainer and Web Browser AppContainer is a sandbox which runs applications in...
-
Hi, it’s Shusei Tomonaga again from the Analysis Center. My previous post discussed the mitigation effects against damages caused by malware infection by enabling Internet Explorer’s (hereafter “IE”’s) Protected Mode. In this article, I’d like to introduce an even stronger security function called “Enhanced Protected Mode”, which is a feature of IE 10 and 11 - its overview and preventive effects against damages caused by malware infection. OVERVIEW OF ENHANCED...
-
Hello, this is Shusei Tomonaga again from the Analysis Center. JPCERT/CC has been observing cases where vulnerability in Internet Explorer (“IE” hereafter) is leveraged in targeted attacks, etc., resulting in system takeover or configuration change by a third party. In fact, IE has several functions to prevent such exploits. In this article, I will introduce one of the functions called “Protected Mode” – its overview and effects. OVERVIEW OF PROTECTED...
-
Hi! I’m Takuho Mitsunaga from Watch and Warning Group. I am pleased to announce that JPCERT/CC has just released a report "Investigation Report Regarding Security Issues of Web Applications Using HTML5 (English version)." As mentioned in the previous posts - JPCERT/CC at “CODE BLUE” and Presenting HTML5 security at OWASP AppSec APAC 2014, through publishing a report (Japanese version), we have worked to point out the issues and raise awareness...