In June 2017, JPCERT/CC released a report “Detecting Lateral Movement through Tracking Event Logs” on tools and commands that are likely used by attackers in lateral movement, and traces that are left on Windows OS as a result of such tool/command execution. After the release, we received a lot of feedback on the report, and until now we had been working on the revision based on the comments. Today, we...
List of “2017”
-
-
Hello again, this is Shusei Tomonaga from the Analysis Center. Event log analysis is a key element in security incident investigation. If a network is managed by Active Directory (hereafter, AD), can be identified by analysing AD event logs. For such investigation, it is quite difficult to conduct detailed analysis in AD event viewer; it is rather common to export the logs to text format or import them into SIEM/log...
-
The last article introduced some features of Datper malware and a Python script for detecting its distinctive communication. Based on that, we are presenting how to search proxy logs for Datper’s communication using log management tools – Splunk and Elastic Stack (Elasticsearch, Logstash and Kibana). For Splunk To extract Datper’s communication log using Splunk, the first thing you need to do is to create a custom search command as follows....
-
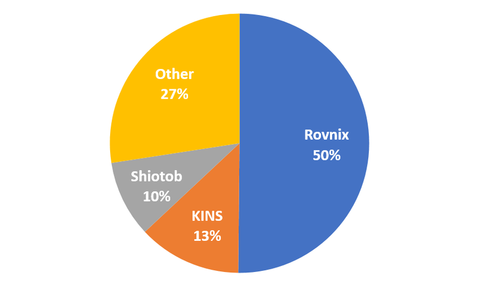
This is Yu Nakamura from Analysis Center. This entry is to explain features of Datper, malware used for targeted attacks against Japanese organisations and how to detect it from the logs. JPCERT/CC has been observing attacks using Datper since around June 2016. Research reports on the adversary are published from LAC [1], SecureWorks [2] and Palo Alto Networks [3]. The adversary had also conducted attacks using Daserf malware in the...
-
Internet banking services across the globe have been exposed to the threat by unauthorized money transfers and suffering large-scale losses. In this landscape, an operation led by international law enforcement agencies has been in effect since November 2016 to capture criminal groups conducting unauthorised online banking transfers and dismantle the attack infrastructure (the Avalanche botnet). JPCERT/CC is one of the many supporters of this operation. For more information about the...
-
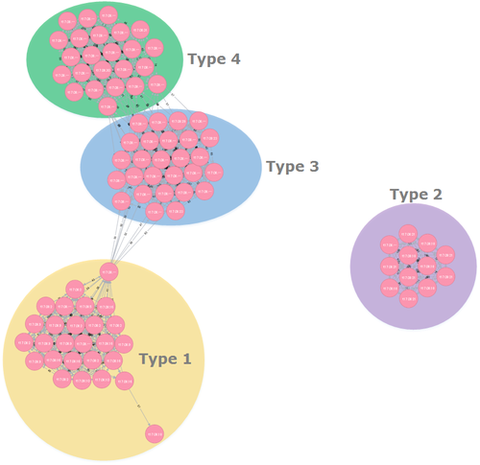
In a past article, we introduced “impfuzzy for Neo4j”, a tool to visualise results of malware clustering (developed by JPCERT/CC). In this article, we will show the result of clustering Emdivi using the tool. Emdivi had been seen until around 2015 in targeted attacks against Japanese organisations. For more information about Emdivi, please refer to JPCERT/CC’s report. Clustering Emdivi with impfuzzy for Neo4j Emdivi has two major variants - t17...
-
JPCERT/CC has been seeing a number of APT intrusions where attackers compromise a host with malware then moving laterally inside network in order to steal confidential information. For lateral movement, attackers use tools downloaded on infected hosts and Windows commands. In incident investigation, traces of tool and command executions are examined through logs. For an effective incident investigation, a reference about logs recorded upon tool and command executions would be...
-
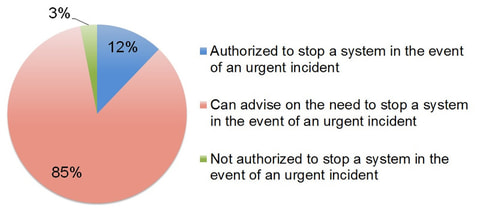
Hello, this is Misaki Kimura from Watch and Warning Group. JPCERT/CC conducted “Survey on the Establishment and Operation of CSIRTs in Japan” in the end of 2015. Following the Japanese report released in 2016, we have just released the English version of the report on JPCERT/CC website to share the outcomes with the information security community member all around the globe. Although the basis of social composition, culture, organizational constitution...
-
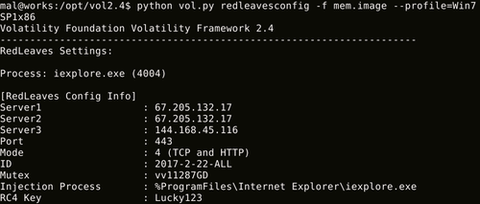
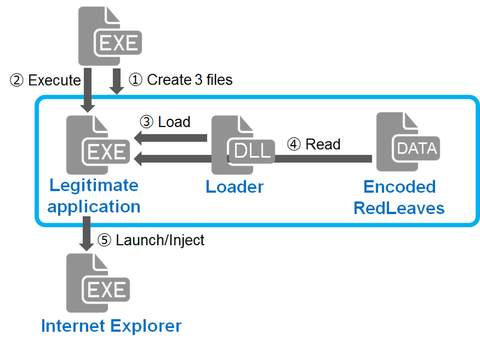
Our previous blog entry introduced details of RedLeaves, a type of malware used for targeted attacks. Since then, we’ve seen reports including those from US-CERT that Management Service Providers (MSPs) have been targeted [1] [2]. In the US-CERT report, some instances have been identified where RedLeaves malware has only been found within memory with no on-disk evidence because of the behavior of self-elimination after the infection. To verify the infection...
-
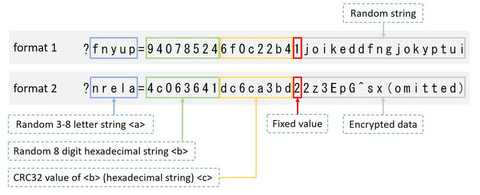
Hi again, this is Shusei Tomonaga from the Analysis Center. Since around October 2016, JPCERT/CC has been confirming information leakage and other damages caused by malware ‘RedLeaves’. It is a new type of malware which has been observed since 2016 in attachments to targeted emails. This entry introduces details of RedLeaves and results of our analysis including its relation to PlugX, and a tool which is used as the base...