As attacks become more fileless and malware gets more obfuscated, it is getting more difficult to determine whether there is a malicious intent from a file by itself. For this reason, malware detection methods that utilize sandboxes and AI, as well as technologies that detect suspicious behavior after malware infection, such as EDR, have now become common. Even so, malware that antivirus software cannot detect is often found during actual...
List of “Tool”
-
-
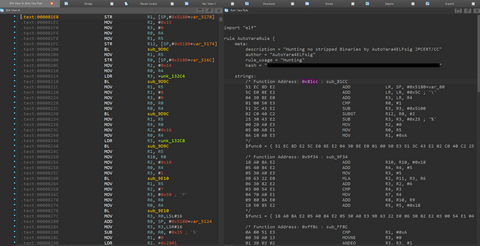
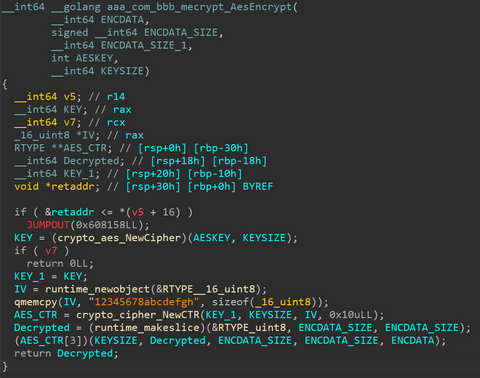
It has been observed that ELF malware removes symbol information during its build. This creates extra work in malware analysis to identify each function name because you do not know them. In addition, in IDA, an analysis tool, existing F.L.I.R.T signatures [1] (hereafter abbreviated as FLIRT signatures in this article) are often not applicable to ELF malware functions, making analysis difficult when right signatures are not found. This blog article...
-
JPCERT/CC has confirmed attacks that infected routers in Japan with malware around February 2023. This blog article explains the details of the attack confirmed by JPCERT/CC and GobRAT malware, which was used in the attack. Attack flow up to malware execution Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT. Figure 1 shows the flow...
-
JPCERT/CC has released LogonTracer v1.5, the latest version of the event log analysis tool. While this tool was initially focused on post-incident investigation, we have received many requests for updates for the purpose of real-time log analysis. This time, we made some updates to enable such functions. This article will introduce the details of the update. Further information can be found at the following page: https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.5.0 Support for Elasticsearch LogonTracer...
-
The Volatility Foundation released Volatility 3 Public Beta, a new version of Volatility Framework in October 2019. The version not only offers compatibility with Python 3 but also has a lot of functional updates from Volatility 2. (Please see Volatility 3's official page for more details.) Particularly, creating plugins is much easier with Volatility 3 compared to the previous version. Volatility 3’s official release is planned for August 2020, and...
-
SysmonSearch is a tool developed by JPCERT/CC to analyse event logs generated on Sysmon (a Microsoft tool). https://github.com/JPCERTCC/SysmonSearch SysmonSearch is now compatible with Elastic Stack 7.x. Please note that the new version no longer supports Elastic Stack 6.x versions. This article introduces the new version of SysmonSearch, changes from the previous versions and new functions. Elastic Stack updates Kibana There was a change in Kibana plug-in due to the updates...
-
JPCERT/CC released a new version of LogonTracer, a tool to support event log analysis. https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.4.0 This article introduces some of the new features of the tool. Dark mode Dark mode has been added to LogonTracer in this update, which appears on the menu bar. Figure 1 shows the LogonTracer screen when the dark mode is on. Figure 1: LogonTracer (dark mode) Please note that each colour represents the following item...
-
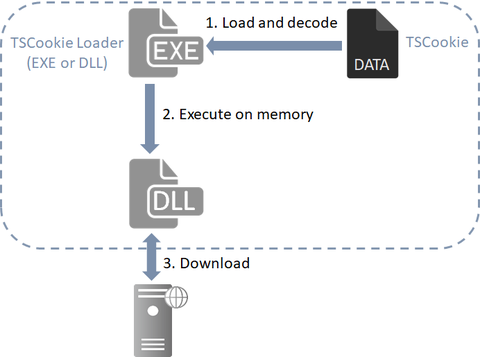
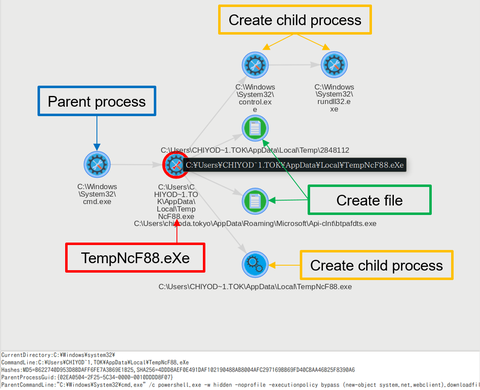
Previously, we explained about malware "TSCookie" and "PLEAD" which are used by an attack group BlackTech. Their activities have been continuously observed in Japan as of now. We have been seeing that a new malware variant is being used after they successfully intruded into a target network. This article explains the details of the variant. TSCookie used after intrusion The malware consists of 2 files (TSCookie Loader and TSCookie) as...
-
Every day, new types of malware are discovered. However, many of them are actually variants of existing malware - they share most part of the code and there is a slight difference in configuration such as CC servers. This indicates that malware analysis is almost complete as long as the configuration is extracted from malware. In this article, we would like to introduce details of “MalConfScan”, a tool to extract...
-
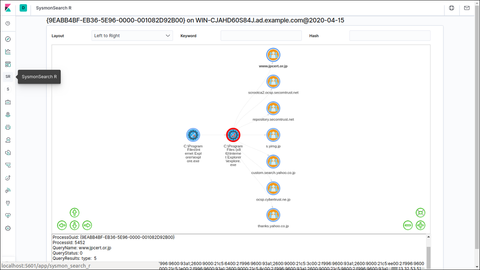
In a past article in September 2018, we introduced a Sysmon log analysis tool "SysmonSearch" and its functions. Today, we will demonstrate how this tool can be used for incident investigation by showing some examples. To install SysmonSearch, please see the following page: JPCERTCC GitHub · SysmonSearch Wiki https://github.com/JPCERTCC/SysmonSearch/wiki The case study was conducted in the following environment: Sysmon 7.0.1 ElasticSearch 6.2.2 Kibana 6.2.2 Winlogbeat 6.2.2 Browser: Firefox Example of...