Every day, new types of malware are discovered. However, many of them are actually variants of existing malware - they share most part of the code and there is a slight difference in configuration such as CC servers. This indicates that malware analysis is almost complete as long as the configuration is extracted from malware. In this article, we would like to introduce details of “MalConfScan”, a tool to extract...
List of “Tool”
-
-
In a past article in September 2018, we introduced a Sysmon log analysis tool "SysmonSearch" and its functions. Today, we will demonstrate how this tool can be used for incident investigation by showing some examples. To install SysmonSearch, please see the following page: JPCERTCC GitHub · SysmonSearch Wiki https://github.com/JPCERTCC/SysmonSearch/wiki The case study was conducted in the following environment: Sysmon 7.0.1 ElasticSearch 6.2.2 Kibana 6.2.2 Winlogbeat 6.2.2 Browser: Firefox Example of...
-
Some malware is designed to run on multiple platforms, and most commonly they are written in Java. For example, Adwind malware (introduced in a past article) is written in Java, and it runs on Windows and other OS. Golang is another programming language, and it is used for Mirai controller, which infects Linux systems. This article introduces the behaviour of WellMess malware based on our observation. It is a type...
-
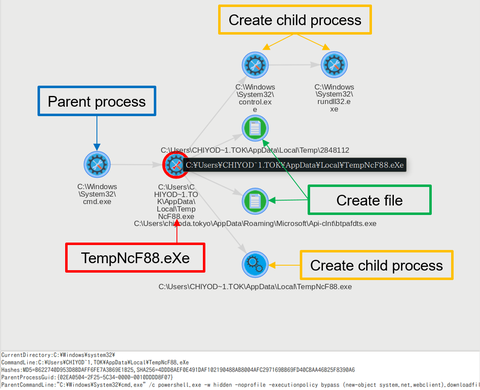
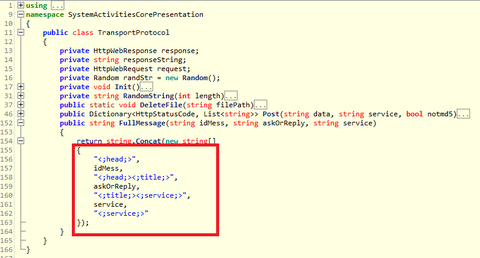
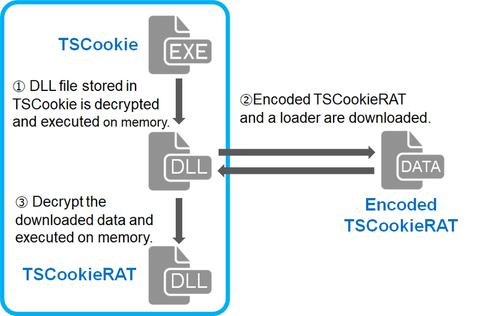
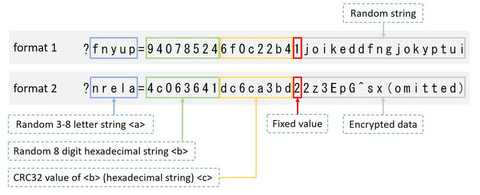
Around 17 January 2018, there were some reports on the social media about malicious emails purporting to be from Ministry of Education, Culture, Sports, Science and Technology of Japan [1]. This email contains a URL leading to a malware called “TSCookie”. (Trend Micro calls it “PLEAD” malware [2]. Since PLEAD is also referred to as an attack campaign, we call this malware TSCookie in this article.) TSCookie has been observed...
-
In the recent article, we introduced the concept and the use of "LogonTracer", a tool to support Windows event log analysis. This article presents how unauthorised logon attempts can be identified using this tool. Please refer to the Wiki for LogonTracer installation. Points for Investigation LogonTracer serves as a tool to support the log analysis rather than to detect unauthorised logon itself. For an effective investigation using this tool, we...
-
Hello again, this is Shusei Tomonaga from the Analysis Center. Event log analysis is a key element in security incident investigation. If a network is managed by Active Directory (hereafter, AD), can be identified by analysing AD event logs. For such investigation, it is quite difficult to conduct detailed analysis in AD event viewer; it is rather common to export the logs to text format or import them into SIEM/log...
-
This is Yu Nakamura from Analysis Center. This entry is to explain features of Datper, malware used for targeted attacks against Japanese organisations and how to detect it from the logs. JPCERT/CC has been observing attacks using Datper since around June 2016. Research reports on the adversary are published from LAC [1], SecureWorks [2] and Palo Alto Networks [3]. The adversary had also conducted attacks using Daserf malware in the...
-
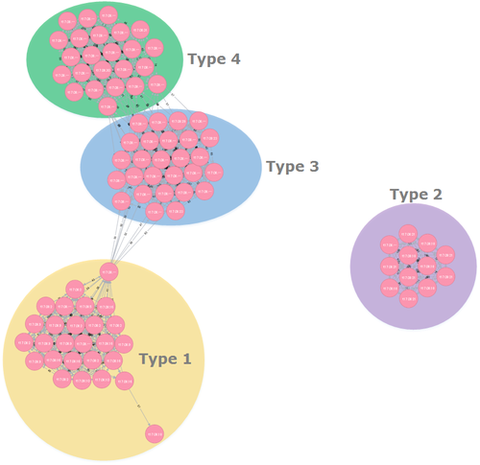
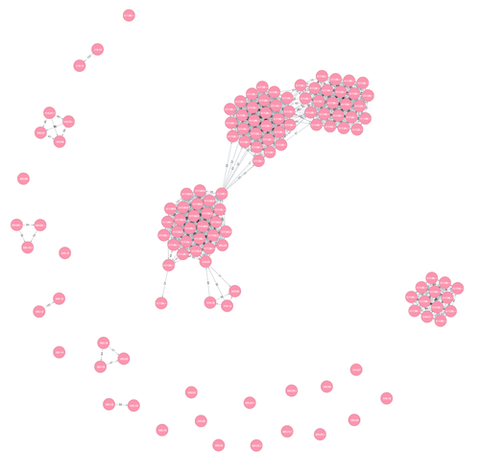
In a past article, we introduced “impfuzzy for Neo4j”, a tool to visualise results of malware clustering (developed by JPCERT/CC). In this article, we will show the result of clustering Emdivi using the tool. Emdivi had been seen until around 2015 in targeted attacks against Japanese organisations. For more information about Emdivi, please refer to JPCERT/CC’s report. Clustering Emdivi with impfuzzy for Neo4j Emdivi has two major variants - t17...
-
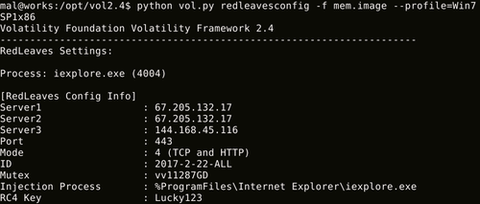
Our previous blog entry introduced details of RedLeaves, a type of malware used for targeted attacks. Since then, we’ve seen reports including those from US-CERT that Management Service Providers (MSPs) have been targeted [1] [2]. In the US-CERT report, some instances have been identified where RedLeaves malware has only been found within memory with no on-disk evidence because of the behavior of self-elimination after the infection. To verify the infection...
-
Hi again, this is Shusei Tomonaga from the Analysis Center. This entry introduces a malware clustering tool “impfuzzy for Neo4j” developed by JPCERT/CC. Overview of impfuzzy for Neo4j impfuzzy for Neo4j is a tool to visualise results of malware clustering using a graph database, Neo4j. A graph database is a database for handling data structure comprised of records (nodes) and relations among the records. Neo4j provides functions to visualise registered...