Investigate Unauthorised Logon Attempts using LogonTracer
In the recent article, we introduced the concept and the use of "LogonTracer", a tool to support Windows event log analysis. This article presents how unauthorised logon attempts can be identified using this tool.
Please refer to the Wiki for LogonTracer installation.
Points for Investigation
LogonTracer serves as a tool to support the log analysis rather than to detect unauthorised logon itself. For an effective investigation using this tool, we suggest that the following elements be examined to analyse unauthorised logon from event logs in Active Directory domain controller.
- Accounts that were used on malware-infected devices
- Use of SYSTEM privilege accounts
- RDP logon
- Frequency of authentication attempts
- Matchup of an account and a host
We will describe how to check these points using LogonTracer. The version used for this article is LogonTracer 1.0.3.
Accounts that were used by malware-infected devices
In targeted attacks, once a host is infected with malware, the infection often spreads to a number of other hosts and servers in the network. If an infected device is found in a network, there is a need to check which account was leveraged on the host and if other devices are also infected.
It is often the case that attackers log on to many different hosts using stolen credentials to spread malware infection. It is important to recognise which accounts are leveraged for such unauthorised logon. By examining which account logs on to infected hosts and if the account is normally used on the infected host itself, it is possible to identify accounts that are used for unauthorised logon attempts.
Moreover, by examining other hosts that were accessed by the leveraged accounts, possibly infected hosts can be identified.
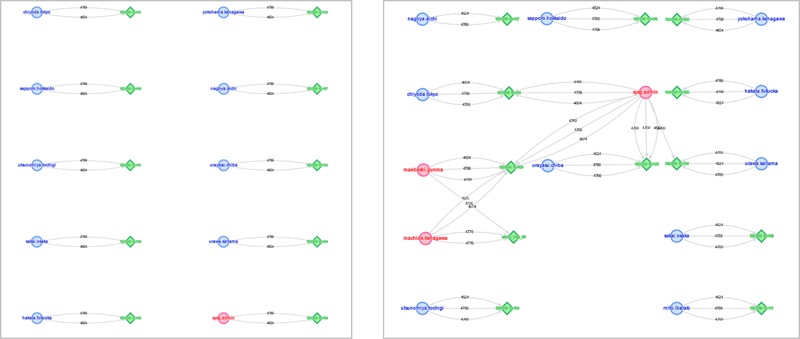
On LogonTracer, you can easily see which account is used for each logon using the search bar. In case where there are multiple infected hosts, you can specify them as in Figure 1, and this may reveal an account used for the unauthorised logon.
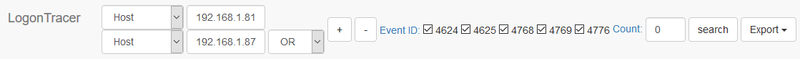 |
You can use regular expressions of account names, host names and IP addresses.
Use of SYSTEM privilege accounts
JPCERT/CC has observed many cases where admin accounts for a domain network (accounts that belong to Domain Admins group) are leveraged to spread malware infection. Since admin accounts are granted access to any hosts including the domain controller, attackers would access hosts that use admin account to harvest its credentials.
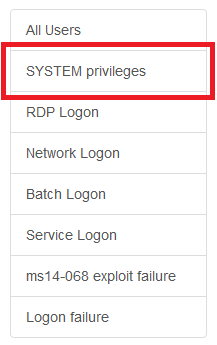
On LogonTracer, you can search for admin accounts from the sidebar (by choosing "SYSTEM privileges" in Figure 2). If an admin account is used on an unusual host, the account is likely to be compromised.
 |
RDP logon
In some cases, attackers log on to hosts by using RDP. You can search for hosts and accounts that are logged on via RDP using the sidebar (by choosing "RDP Logon" in Figure 2).
Frequency of authentication attempts
To spread infection in the network, attackers may also conduct brute force attacks using a password dictionary. In this case, there will be a lot of failed logon attempts recorded in a short period of time.
LogonTracer can display the number of event logs for each account per hour in a chronological order ("Create All Users" in Timeline). By specifying an account name in the search bar and click on "Search" in the Timeline (Figure 3), log count for each event ID will be displayed. A failed logon attempt is recorded as event ID 4625. If there is an increase in the log of this event ID, there is a possibility of unauthorised logon being conducted.
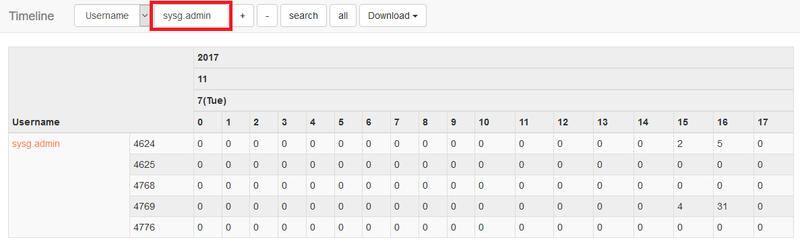 |
A sudden increase and decrease in event log count will be highlighted.
Matchup of an account and a host
This investigation is effective in an environment where each account is only permitted to log on to a single host. If such "one host per account" policy is applied, the relation of an account and a host will be described as in the left diagram in Figure 4 using the LogonTracer’s visualisation function ("All Users" in Figure 2), showing that the host and account ratio is 1:1. If unauthorised logon attempts to multiple hosts occur from an account, the log will be as in the right diagram. This way, logon attempts to a certain account from multiple hosts can be easily identified.
However, in most of the organisations that JPCERT/CC assisted with incident investigation, "one host per account" operation was not practiced, which made the investigation quite complicated. Logs in such organisations are described as in Figure 5. It is difficult to examine suspicious logon attempts in this situation.
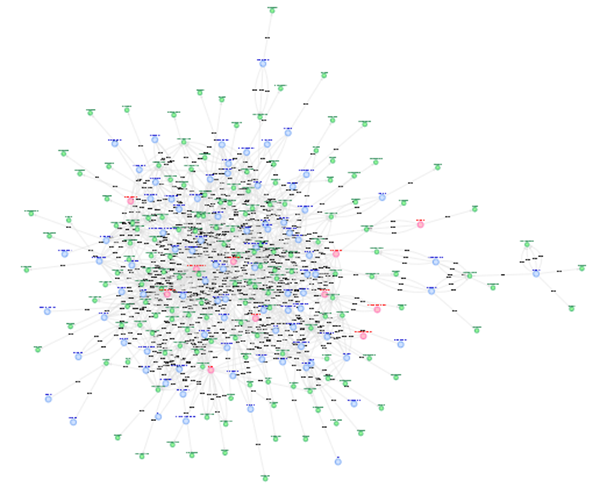 |
We recommend the "one host per account" operation for smooth incident investigation.
Conclusion
We plan to continue updating LogonTracer with enhanced functions. Currently, it only focuses on logon-related event logs, but we are considering adding other events such as policy change, create user, add group and delete event logs. If there is any request about the functions of this tool, please contact global-cc[at]jpcert.or.jp.
- Shusei Tomonaga
(Translated by Yukako Uchida)
Update (Nov 7, 2018)
Multiple vulnerabilities were found in LogonTracer prior to v1.2.1.
If you are using any of the old versions, please update to the latest version.
Multiple vulnerabilities in LogonTracer
https://jvn.jp/en/vu/JVNVU98026636/index.html
Release v1.2.1 - JPCERTCC/LogonTracer - GitHub
https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.2.1
[Acknowledgement]
We thank Shoji Baba, Kobe Digital Labo Inc for helping us to fix these issues.