LogonTracer v1.6 Released
JPCERT/CC released the latest version (v1.6) of LogonTracer, a tool to support event log analysis. Previously, LogonTracer could not investigate multiple incidents simultaneously, but this update adds support for managing multiple logs. In addition, Sigma can now be used to investigate the presence of suspicious logs in the event log. This article introduces these updates. For other updated items, please refer to the following release:
https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.6.0
Log Management Feature
When investigating multiple incidents, you may sometimes want to manage logs separately for each incident or investigate multiple incidents simultaneously. On LogonTracer, logs are managed in units of "case". This feature is available when using Neo4j Enterprise Edition as the database for LogonTracer. See Neo4j webpage for more information about Neo4j Enterprise Edition. The following describes the procedure for log management using a "case". Note that the following operations can be performed only by an administrator.
1. Create a case
First, create a new case from "Add New Case".
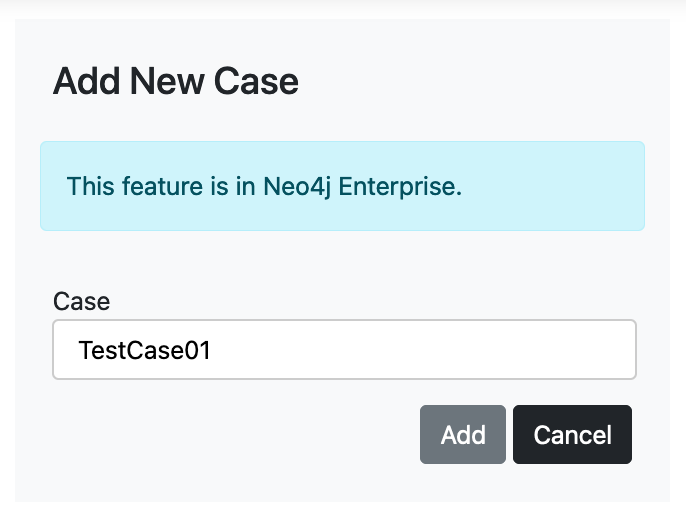
After a case is created, you will see that the case is used as shown in Figure 2. By default, the "Default" case is used, which all users can access.
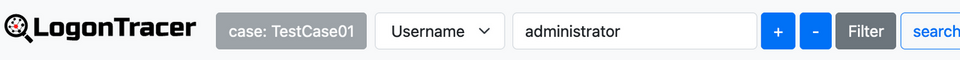
When an event log is uploaded in this state, the log is managed in the created case. If you want to use a different case, you can change case from "Change Case".
2. Limit users who can access the case
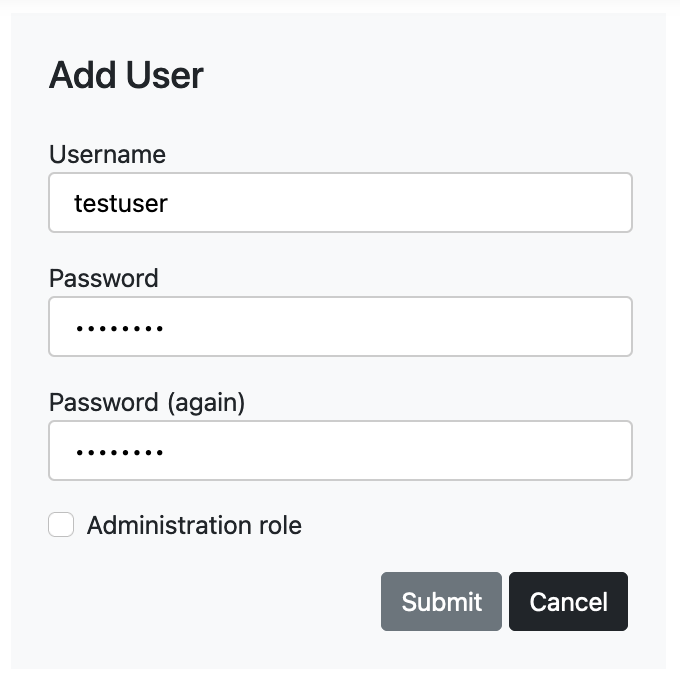
You can limit users who can access a case. Create a new user from "Add User".
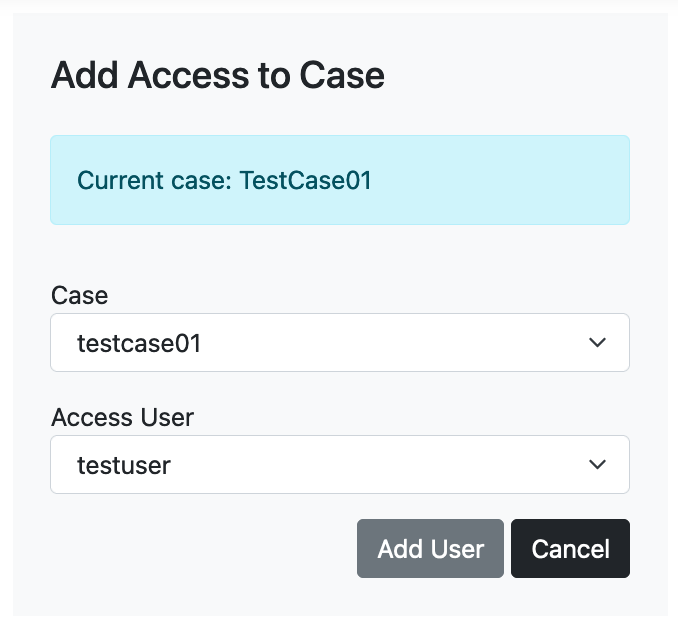
Next, from "Add Access to Case", specify which users can access the case. If you wish to change the settings, you can do so from "Delete Access to Case".
Sigma Support
Sigma is a common format for converting log detection signatures so that they can be used by SIEM and various security products. Many Sigma rules are available in the official Sigma repository and can be effectively used to investigate logs. Refer to the Sigma GitHub repository for further information:
https://github.com/SigmaHQ/sigma
A number of rules for investigating security event logs are also available, and LogonTracer now supports investigating event logs using these Sigma rules. When uploading an event log, check "Run scan using Sigma rules" and you can see the investigation results.
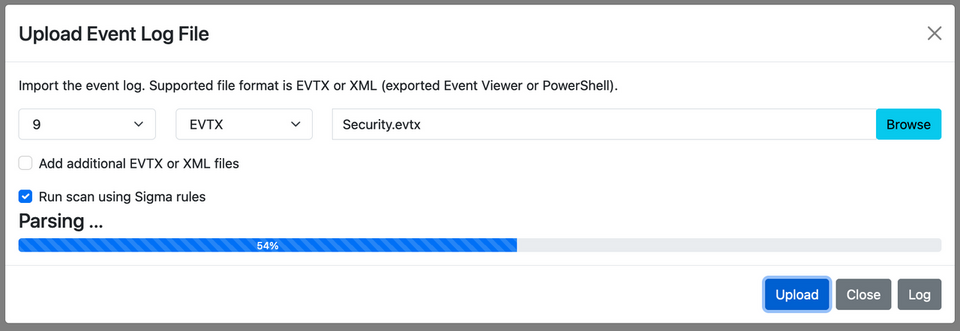
The investigation results can be downloaded as a CSV file from the sidebar. Although Sigma rules cannot detect all suspicious logons, they should still be helpful in investigating incidents.
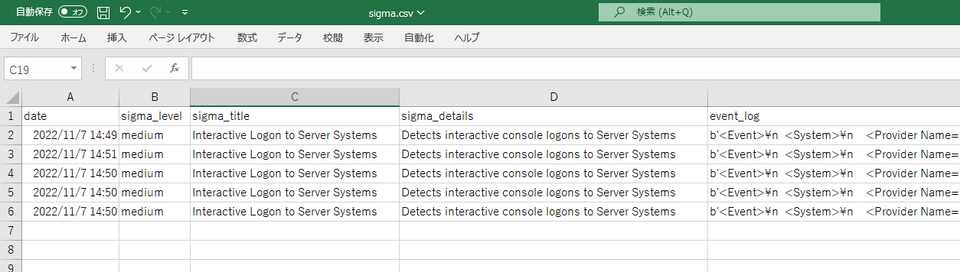
Currently, LogonTracer only supports simple detection rules and does not cover rules that span multiple logs (such as count() in the condition field) or complex condition matching. We plan to support more complex detection conditions in the future.
In Closing
The LogonTracer v1.6 update includes login screen and bug fixes in addition to the above features introduced.
Please refer to the Wiki for details on how to use the new version.
https://github.com/JPCERTCC/LogonTracer/wiki
We will keep updating LogonTracer reflecting received requests, and your Pull Requests and comments are always welcome.
Shusei Tomonaga
(Translated by Takumi Nakano)