Visualise Sysmon Logs and Detect Suspicious Device Behaviour -SysmonSearch-
In recent sophisticated cyber attacks, it is common to observe lateral movement, where a malware- infected device is used as a stepping stone and further compromise other devices in the network. In order to investigate the compromised devices, it is necessary to retain detailed logs of the applications that run on the device on a daily basis. One of the well-known tools for this purpose is Sysmon [1] from Microsoft, which records various operations on the Windows OS (e.g. applications, registry entries, communication) in the event logs. Most commonly, analysts convert the logs into text format to search for specific items in the logs. However, it is a hectic and not-so-organised task when it comes to investigation over multiple devices.
JPCERT/CC has developed and released a system “SysmonSearch” which consolidates Sysmon logs to perform faster and more accurate log analysis. We are happy to introduce the details in this article.
SysmonSearch system overview
SysmonSearch is a system based on Elastic Stack [2]. Sysmon log analysis function (search, statistical analysis and visualisation) is implemented by Kibana Plugin. Figure 1 describes the system overview.
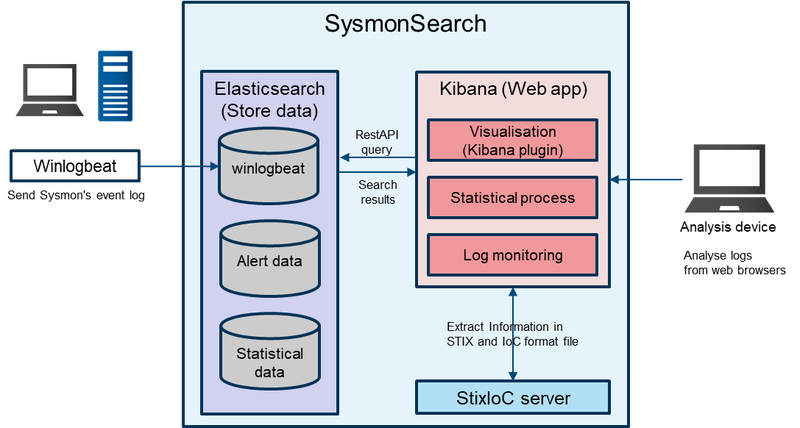 |
Sysmon log visualisation
In SysmonSearch, each record in Sysmon log (process, file, registry etc.) is defined as a node, which are correlated with each other upon visualisation. This makes it easy to grasp how each node is related with others. For example, you can see a file created from a certain process and network communication occurring from another process. Figure 2 shows an example of visualised Sysmon logs. Each node is described with an icon. Icons are prepared for each event ID so that it is visually comprehensible. Please refer to Appendix for the list of Sysmon event IDs and corresponding icons.
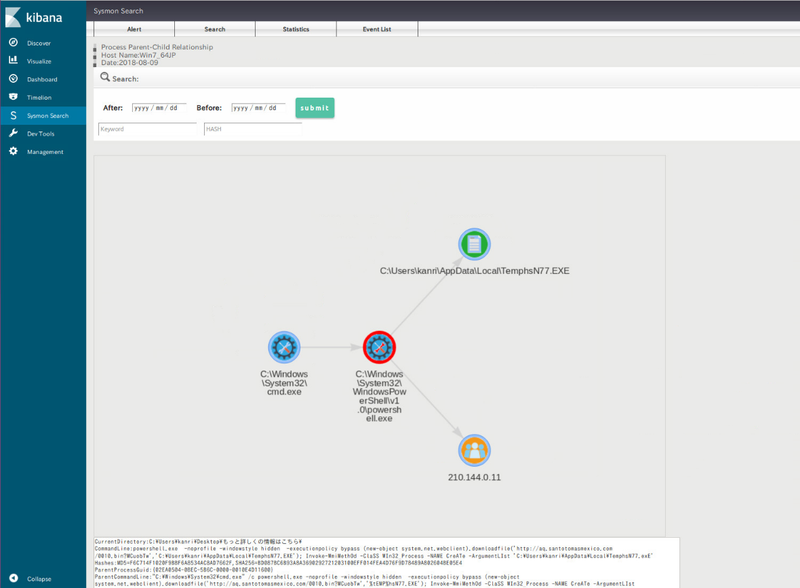 |
Sysmon log search
SysmonSearch can search Sysmon logs with the following conditions:
- Date
- IP address
- Port number
- Host name
- Process name
- File name
- Registry key
- Registry value
- Hash value
If malware hash value or a C&C server is identified through the search, it is possible to check if any other device in the network is also affected by the same malware. You can also search for specific items from imported IoC and STIX data.
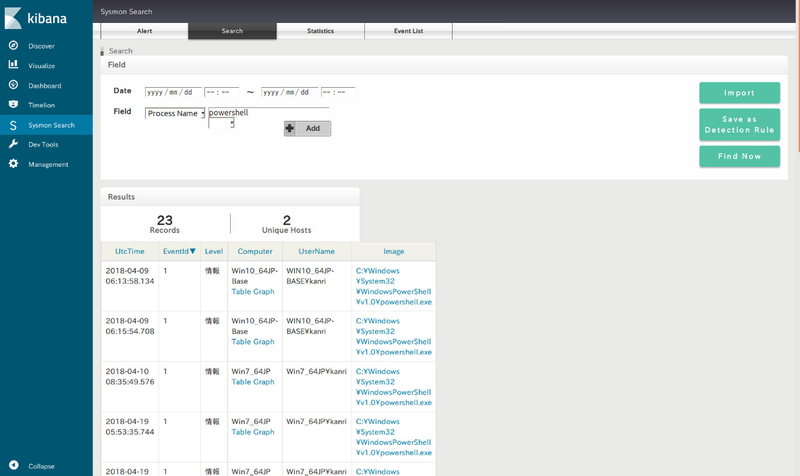 |
Sysmon log monitoring
This tool also performs near real-time search on Sysmon logs based on a certain rule and displays matched logs. Checking for logs that matches certain anomaly conditions may help detecting signs of an incident at an early stage. Monitoring rules can be configured on the search function.
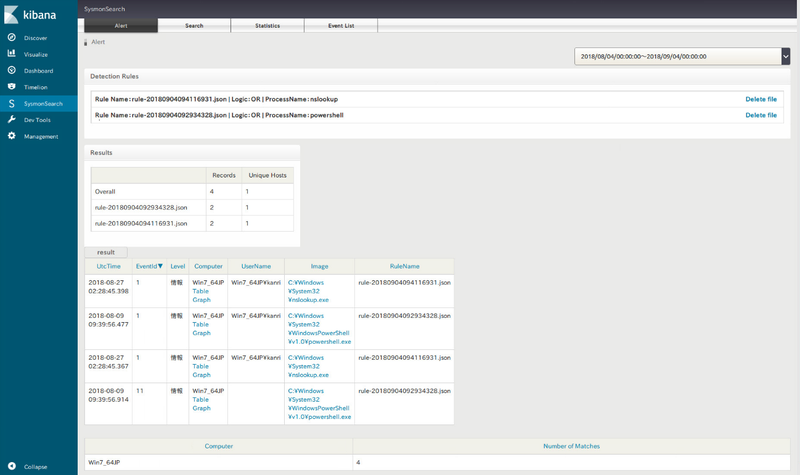 |
Sysmon log statistical analysis
This function provides statistical data on events related to network communication, process and registry per device. It may be useful in identifying suspicious events which cannot be found with the monitoring function.
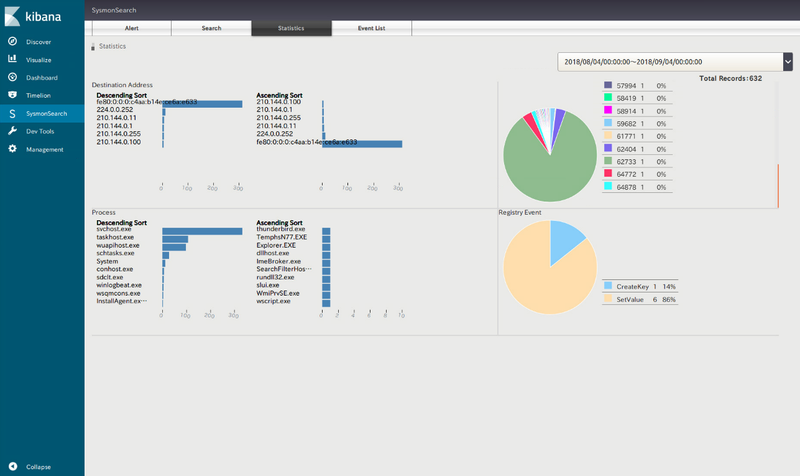 |
 |
How to install
SysmonSearch is available on GitHub from the following URL. DockerFile is also available.
JPCERTCC GitHub - SysmonSearch
https://github.com/JPCERTCC/SysmonSearch
JPCERTCC GitHub – SysmonSearch Wiki
https://github.com/JPCERTCC/SysmonSearch/wiki
In closing
SysmonSearch enables faster and more accurate log analysis, and the monitoring function serves for early detection of incidents. We hope that the tool is helpful in incident analysis.
- Wataru Takahashi
(Translated by Yukako Uchida)
Reference
[1] Sysmon - Windows Sysinternals | Microsoft Docs
https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
[2] Powering Data Search, Log Analysis, Analytics | Elastic
https://www.elastic.co/products
Appendix
|
Event ID |
Event | Icon |
|---|---|---|
| 1 | Process Create | |
| 2 | File creation time changed | |
| 3 | Network Connection Detected | |
| 7 | Image loaded | |
| 8 | CreateRemoteThread | |
| 11 | FileCreate | |
|
12 |
Registry Event (CreateKey) |
|
|
12 13 14 |
Registry Event | |
|
19 20 21 |
WmiEvent |

