JPCERT/CC has confirmed attack activities targeting Japanese organizations by an attack group called Kimsuky in March 2024. This article introduces the attack methods of the group confirmed by JPCERT/CC. Attack overview In the attack we identified, the attacker sent a targeted attack email impersonating a security and diplomatic organization. A zip file containing the following files with double file extensions was attached to the email. (File names are omitted.) (1)...
List of “喜野 孝太(Kota Kino)”
-
-
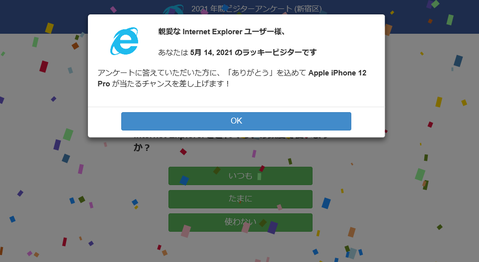
JPCERT/CC continues to observe cases of website being compromised and embedded with a malicious page. Visitors are redirected to a scam site or suspicious shopping site by malicious PHP script (hereafter, “PHP malware”). This article explains the details of PHP malware which is often found in websites in Japan. Cases observed On PHP malware-embedded websites, there are many malicious webpages that redirect visitors to a scam site or suspicious shopping...
-
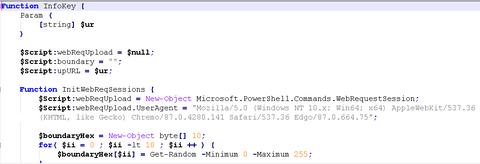
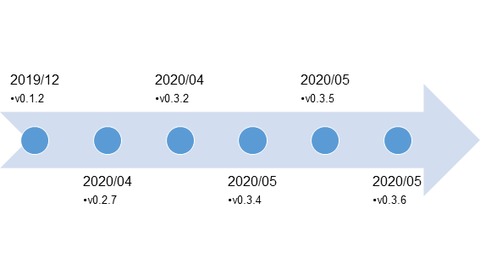
The functions and evolution of malware LODEINFO have been described in our past articles in February 2020 and June 2020. Yet in 2021, JPCERT/CC continues to observe activities related to this malware. Its functions have been expanding with some new commands implemented or actually used in attacks. This article introduces the details of the updated functions and recent attack trends. LODEINFO versions At the time of the last blog update,...
-
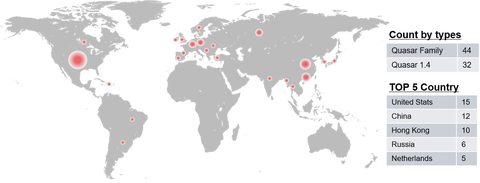
Quasar [1] is an open source RAT (Remote Administration Tool) with a variety of functions. This is easy to use and therefore exploited by several APT actors. JPCERT/CC has confirmed that a group called APT10 used this tool in some targeted attacks against Japanese organisations. As Quasar’s source code is publicly available, there are many variants of this RAT seen in the wild (referred to as “Quasar Family” hereafter). Some...
-
We introduced malware LODEINFO in a past blog entry. Attacks using the malware have been continuously seen, in particular with malicious file names including those related to COVID-19. It is also confirmed that LODEINFO has been updated frequently, and several functions have been added or changed in the latest version. This article will introduce trends seen in the series of attacks and updates to the malware. LODEINFO distribution Cases that...
-
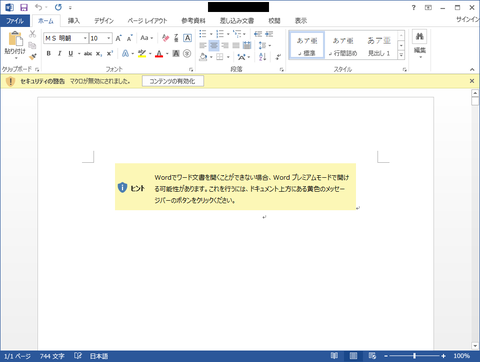
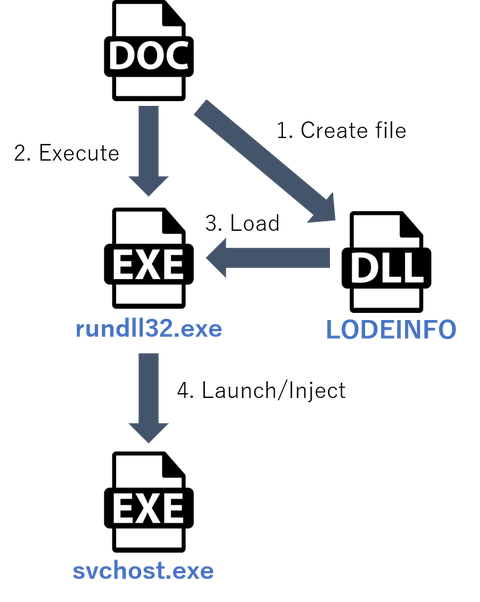
JPCERT/CC has been observing a new type of spear-phishing emails targeting Japanese organisations since December 2019. The emails have a malicious Word file attachment leading to malware “LODEINFO”, which is newly observed. This article introduces the details of this malware. How LODEINFO is launched Figure 1 describes the flow of events from executing a Word file until LODEINFO is launched. Figure 1:Flow of events until LODEINFO runs By enabling the...
-
JPCERT/CC organised Japan Security Analyst Conference 2020 (JSAC2020) on 17 January, 2020 in Ochanomizu, Tokyo. This conference targets front-line security analysts who deal with cyber incidents on a daily basis, with an aim to create a venue for sharing technical information which helps them better handle ever-evolving cyber attacks. This is the third event running annually since 2018, and 301 participants attended this year. In this event, we invited 8...