Evolution of Malware LODEINFO
We introduced malware LODEINFO in a past blog entry. Attacks using the malware have been continuously seen, in particular with malicious file names including those related to COVID-19. It is also confirmed that LODEINFO has been updated frequently, and several functions have been added or changed in the latest version.
This article will introduce trends seen in the series of attacks and updates to the malware.
LODEINFO distribution
Cases that we have observed are all originated in targeted emails with a malicious file attachment, either a Word or Excel file. It contains a macro which creates and executes LODEINFO on the host if enabled. Contents of the email and the attachment file include the following topics:
- COVID-19
- Russia-Japan or Korea-Japan relations
- Resumes and job applications
Targeted sectors include media and public organisations. Many of these emails are sent from free email addresses including Gmail.
LODEINFO version
While we previously described the details of LODEINFO v0.1.2, the latest version confirmed at the time of this publication is v0.3.6. JPCERT/CC has confirmed the following versions of LODEINFO in the wild.
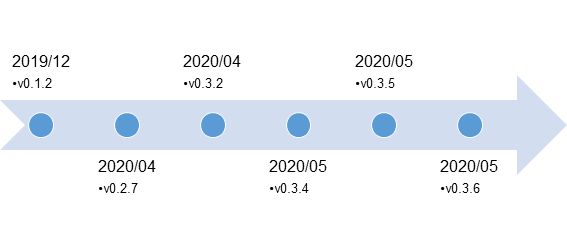
Major functions that are added in the respective version are as follows:
Version |
Added function |
|---|---|
| v0.2.7 | Partial change to data exchange format |
| Additional command (ver) | |
| Mutex creation | |
| v0.3.2 | New command (print) |
| Submit auto-run key into registry for persistence | |
| v0.3.5 | New commands (rm, ransom, keylog) |
New commands
The latest version as of now (v0.3.6) has additional commands compared to v0.1.2.
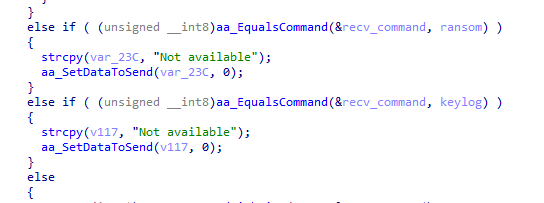
- rm
- ransom
- keylog
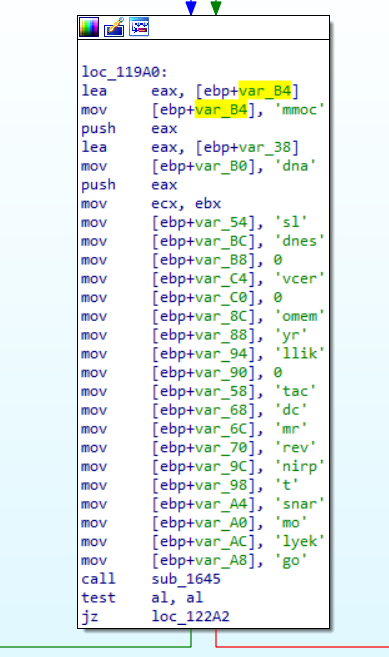
print command obtains a screen capture of the infected host, and rm command deletes a specified file. If rm command is executed, a file is deleted, and the following results are sent to a C&C server.
1590318292|932|080027D50FB0|DESKTOP-J783225C:\Users\Public\Pictures\Sample Pictures\Chrysanthemum.jpg: OK. C:\Users\Public\Pictures\Sample Pictures\Desert.jpg: OK. C:\Users\Public\Pictures\Sample Pictures\desktop.ini: OK. C:\Users\Public\Pictures\Sample Pictures\Hydrangeas.jpg: OK. C:\Users\Public\Pictures\Sample Pictures\Jellyfish.jpg: OK. C:\Users\Public\Pictures\Sample Pictures\Koala.jpg: OK. C:\Users\Public\Pictures\Sample Pictures\Lighthouse.jpg: OK. C:\Users\Public\Pictures\Sample Pictures\Penguins.jpg: OK. C:\Users\Public\Pictures\Sample Pictures\Tulips.jpg: OK.
ransom, keylog commands are not yet implemented in the latest version, which returns the following results to a C&C server.
1590318292|932|080027D50FB0|DESKTOP-J783225Not available
Assuming from the command name, the file encryption and key logging functions may be equipped in the future.
Partial change to data exchange format
LODEINFO encrypts data by combining AES and BASE64. The size of AES-encrypted data is specified at the offset 0x45 in the BASE64-decoded string.
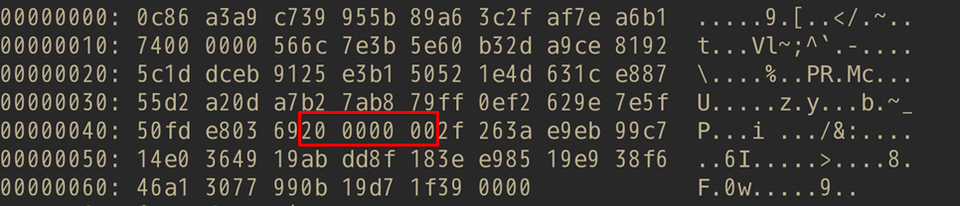
In the v0.1.2, the data size was specified as is. However, v0.2.7 and later versions encode the size of AES-encrypted data with 1-byte XOR key. The XOR key is specified at the offset 0x49.
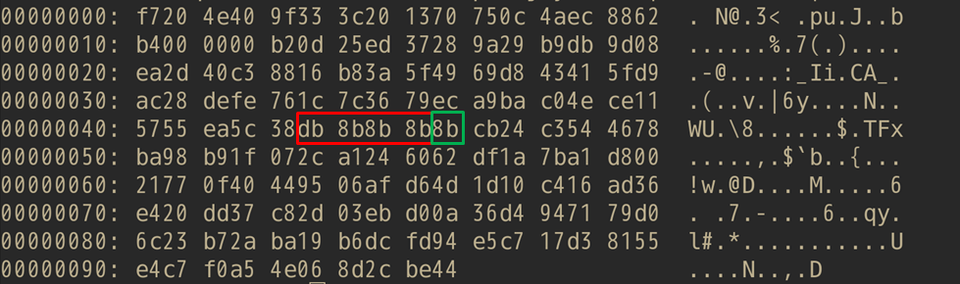
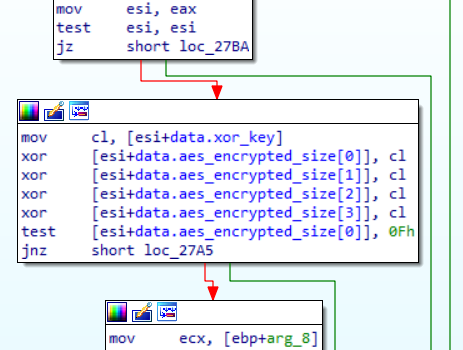
LODEINFO communicates with specific hosts and operates according to the commands received from there. With this change, the Python script to decode a HTTP POST request as shown in the past blog entry no longer works. Here is the code that works with the new versions:
from Crypto.Cipher import AES
from base64 import urlsafe_b64decode
from binascii import a2b_hex
def decypt_lodeinfo_data(enc_data: str, key: bytes, iv: bytes) -> bytes:
header_b64 = enc_data[:0x1C]
header = urlsafe_b64decode(header_b64.replace(".", "="))
## decode with base64
postdata_size = int.from_bytes(header[0x10:0x14], byteorder="little")
postdata_b64 = enc_data[0x1C:0x1C+postdata_size]
postdata = urlsafe_b64decode(postdata_b64.replace(".", "="))
## decrypt with AES
cipher = AES.new(key, AES.MODE_CBC, iv)
xor_key = postdata[0x34]
decrypt_size = int.from_bytes([b ^ xor_key for b in postdata[0x30:0x34]],byteorder="little")
dec_data = cipher.decrypt(postdata[0x35:0x35+decrypt_size])
## remove junk bytes
junk_size = dec_data[-1]
dec_data = dec_data[:decrypt_size-junk_size]
return dec_data
encrypted_data = "njgGCEgbkXQIgexSrDm3O7QAAADuSiTM6xoP8ResYAybhHoRx9W-Ulw_ealn9gIEjvsZzqQXG8vn3QYoIfmNmO4viy0rFkZGRkaN6IX4HXa-cdyoRLWkIYxVPI9Ciu8sDP1PK0x6gDH556OYX8GMdejk40daIbiwY3ERd0qL8jRawpwBHht7Sps_hwoZfeks-ly5sw2Y9RqtUQ.."
KEY = a2b_hex("7306ED96A7D75BAB94C4F15AAF0A9E61690F0E300FEA9135764C206580DF2970")
IV = a2b_hex("D5C5376805264812B3ED88BE4A614A1A")
decrypted_data = decypt_lodeinfo_data(encrypted_data, KEY ,IV)
print("Decrypted Data: ", bytes.hex(decrypted_data))
Changes in Defense Evasion
In the previous versions, the decoy document created a DLL containing LODEINFO when the macro was enabled, and the DLL was executed by rundll32.exe. However, v.0.3.2 and later versions started to implement DLL sideloading. The decoy document creates and executes a legitimate Windows PE file and modifies the DLL containing LODEINFO when the macro is enabled. The LODEINFO payload will be loaded by the legitimate Windows PE using DLL sideloading.
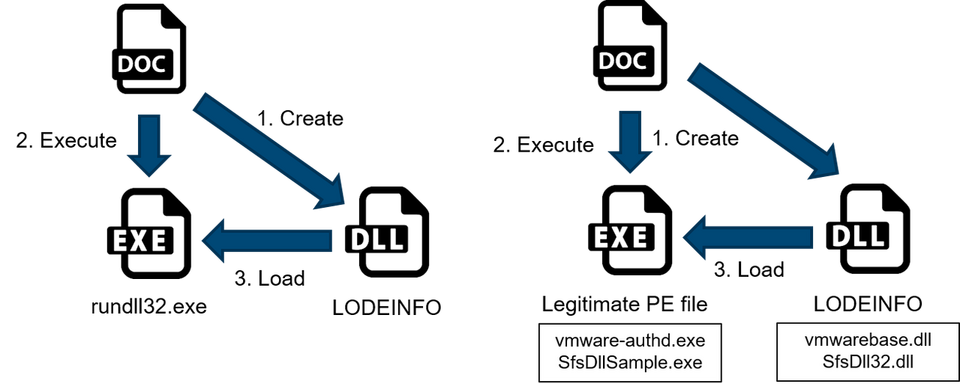
LODEINFO’s Communication
User-Agent is hardcoded in LODEINFO, and the following is used in up to v0.2.7:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
and in v0.3.2 and later:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36 Edge/18.18363
ISPs in various countries are used for C&C server infrastructure.
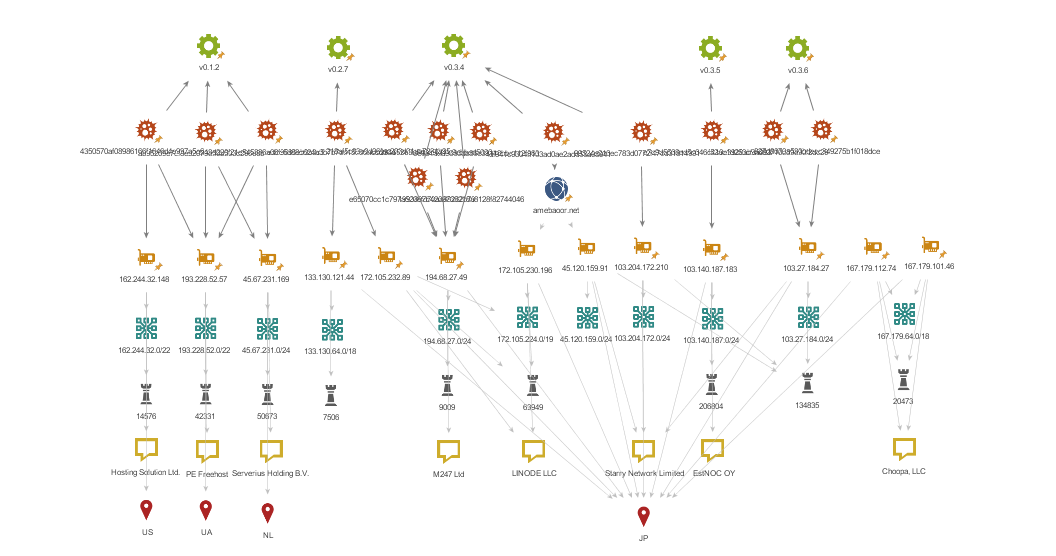
In closing
LODEINFO has been constantly updated, and attacks using the malware are observed continuously. It is recommended to keep an eye on these attack activities as they are still likely to persist.
We have a list of sample hash values in Appendix A and newly confirmed C&C servers in Appendix B. Please make sure that none of your devices is communicating with such hosts.
- Kota Kino and Ken Sajo
(Translated by Yukako Uchida)
Appendix A: SHA-256 Hash Value of Samples
- 65433fd59c87acb8d55ea4f90a47e07fea86222795d015fe03fba18717700849 (v0.3.6)
- 8c062fef5a04f34f4553b5db57cd1a56df8a667260d6ff741f67583aed0d4701 (v0.3.5)
- 1cc809788663e6491fce42c758ca3e52e35177b83c6f3d1b3ab0d319a350d77d (v0.3.2)
Appendix B: C&C servers
- 103.27.184.27
- 103.140.187.183
- 103.204.172.210
- 133.130.121.44
- 167.179.101.46
- 167.179.112.74
- 172.105.232.89
- 194.68.27.49
- www.amebaoor.net

