Continuing from the previous blog article, this entry introduces the presentations on the 2nd day of JSAC2025. Observation of phishing criminal groups related to illegal money transfers and Mizuho Bank’s countermeasures -Fighting against phishing site malware ‘KeepSpy’- Speaker: Tsukasa Takeuchi, Takuya Endo, Hiroyuki Yako (Mizuho Financial Group) Slides(English) Tsukasa, Takuya, and Hiroyuki presented Mizuho’s efforts to address phishing attacks, including the analysis of exploited malware and the criminal groups behind...
List of “JPCERT/CC”
-
-
The difficult part of the initial response to a human-operated ransomware attack is identifying the attack vector. You may already know from recent security incident trends that the vulnerabilities of VPN devices are likely to be exploited, but it often takes much time to investigate because multiple penetration routes are often considered when an incident occurs. Therefore, in order to ensure a smooth initial response, it is important to investigate...
-
JPCERT/CC held the annual ICS Security Conference 2024 on 7 February 2024. The conference aims to share the current status of threats to ICS both in Japan and overseas and the efforts of stakeholders in the field, as well as to help participants improve their ICS security measures and establish best practices. The conference started in 2009 and is now in its 16th year. This was the 4th time the...
-
We continue to introduce the talks at JSAC2024. This third issue covers workshops and lightning talks. Workshop Introduction to Investigation of Unauthorised Access to Cloud Speakers: Hayate Hazuru and Takahiro Yamamoto (ITOCHU Cyber Intelligence Inc.), Norihide Saito (Flatt Security Inc.), Daisuke Miyashita (Sterra Security Co.,Ltd.) Hayate, Takahiro, Norihide, and Daisuke explained how the cloud works and the attack methods targeting cloud in their workshop, followed by a log investigation demonstration...
-
JPCERT/CC held JSAC2024 on January 25 and 26, 2024. The purpose of this conference is to raise the knowledge and technical level of security analysts, and we aimed to bring them together in one place where they can share technical knowledge related to incident analysis and response. The conference was held for the seventh time and, unlike last year, returned to a completely offline format. 17 presentations, 3 workshops, and...
-
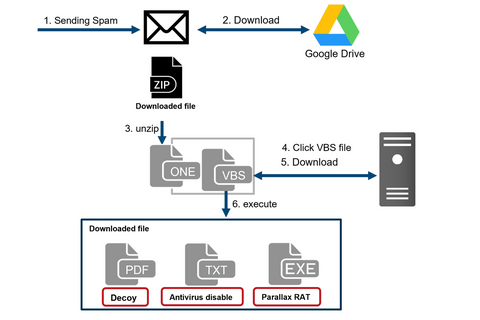
Around February 2023, JPCERT/CC identified an attack that attempted to infect a crypto asset exchanger with the Parallax RAT malware. This attack attempted to infect employees of the crypto asset exchanger with malware by sending spam emails. This article presents the details of this attack.Flow of events leading to Parallax RAT infectionFigure 1 shows the flow of this attack. The identified attack starts with a spam email, which urges the...
-
We continue to introduce the talks at JSAC2023. This third issue covers the workshops on Day 2. Surviving the hurt locker: or How I Learned to Stop Worrying and Love the Bom Speakers: Simon Vestin, Manabu Niseki (LINE) Simon and Manabu explained the SBOM (Software Bill of Materials) and gave a hands-on session on creating a program to generate one. SBOM is a list of software or system components. They...
-
This article reports on JSAC Day 2, following the previous article about Day1. How Do We Fight against Evolving Go Language Malware? Practical Techniques to Increase Analytical Skills Speakers: Tsubasa Kuwabara (FFRI Security Inc.) Slides (English) Tsubasa presented the current situation and problems of Go language malware, which has been increasing in recent years, and explained basic and advanced analysis techniques. He explained that Go malware was easy to write...
-
JPCERT/CC held JSAC2023 on January 25 and 26, 2023. The purpose of this conference is to raise the knowledge and technical level of security analysts in Japan, and we aimed to bring them together in one place where they can share technical knowledge related to incident analysis and response. This year was the sixth time the conference was held, and 12 presentations, 2 workshops, and 7 lightning talks were presented...
-
JPCERT/CC held JSAC2022 online on January 27, 2022. The purpose of this conference is to raise the knowledge and technical level of security analysts in Japan, and we aimed to bring them together in one place where they can share technical knowledge related to incident analysis and response. This year was the fifth time the conference was held. 9 presentations and 2 workshops, selected from 18 CFP and CFW submissions,...