Event Log Talks a Lot: Identifying Human-operated Ransomware through Windows Event Logs
The difficult part of the initial response to a human-operated ransomware attack is identifying the attack vector. You may already know from recent security incident trends that the vulnerabilities of VPN devices are likely to be exploited, but it often takes much time to investigate because multiple penetration routes are often considered when an incident occurs. Therefore, in order to ensure a smooth initial response, it is important to investigate the penetration route after first estimating the attack group based on the encrypted file extensions and ransom notes left on the affected device, and then identifying the entry points that the attack group has used in the past. However, in JPCERT/CC's experience to date, there have been multiple cases where it was not possible to identify the attack group based on the encrypted file extension or ransom note alone. In this article, we will share the results of an investigation into the possibility of using Windows event log information to support the identification of such attack groups. JPCERT/CC's investigation confirmed that some ransomware leaves traces in the Windows event log, and that it is sometimes possible to identify the ransomware based on these characteristics. The following four Windows event logs were used in this investigation.
- Application Log
- Security Log
- System Log
- Setup Log
The following sections introduce the logs recorded in the Windows Event Log when ransomware is executed.
Conti
Conti is ransomware first identified in 2020. In 2022, the source code related to Conti was leaked, and many variants appeared afterwards. Conti exploits Windows Restart Manager when encrypting files. It is a function that automatically closes running applications when Windows OS is restarted or shut down. Although logs may be recorded in the event log during normal operation as well, when Conti is executed, a large number of relevant logs (event IDs: 10000, 10001) are recorded in a short period of time.
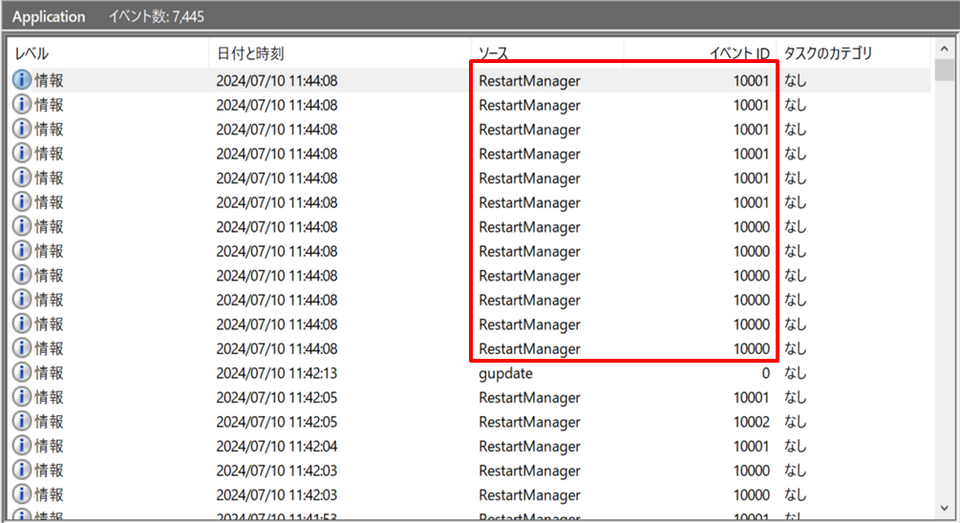
Figure 1: Event logs confirmed during Conti execution
We have also confirmed that the following ransomware also records similar event logs. Some of them are suspected to be related to Conti.
- Akira (suspected to be related to Conti based on the status of cryptocurrency transactions, etc.)
- Lockbit3.0 (uses a Conti-based encryption system)
- HelloKitty
- Abysslocker
- avaddon
- bablock
Phobos
Phobos is ransomware identified in 2019. It is said to have appeared after the source code was found to be similar to that of the Dharma ransomware, and after a decryption tool for Dharma became available, many variants were identified. Phobos can delete the volume shadow copies and system backup catalogs of infected devices, and it leaves traces when it is executed. Please note that the above-mentioned content may also occur in normal operation when the system administrator manages disk space or organizes unnecessary data.
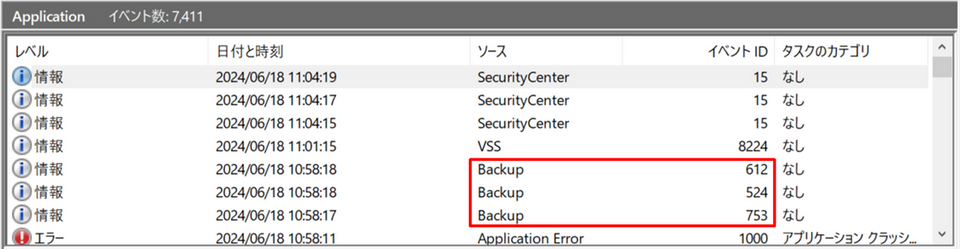
Figure 2: Event logs confirmed during Phobos execution
- Event ID 612: A backup scheduled to be performed automatically was canceled somehow
- Event ID 524: The system catalog was deleted
- Event ID 753: The backup system successfully started and is ready to operate
In addition, traces with similar characteristics have been recorded from the following ransomware, which is suspected to be related to the Phobos group.
- 8base
- Elbie
Midas
Midas is ransomware first identified in 2021. Midas is characterized in that it leaves traces in the event logs regarding changes to network settings, which are considered to be aimed to spread the infection, at the time of execution.
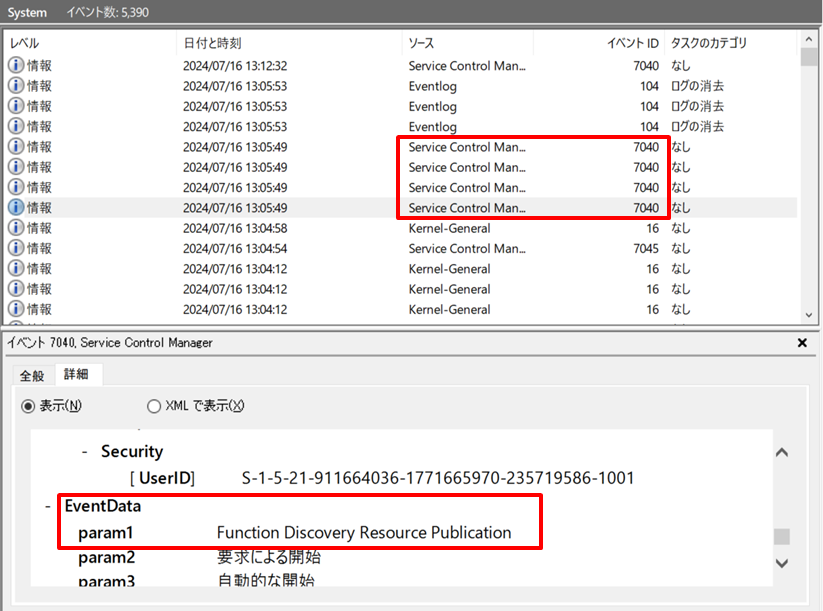
Figure 3: Event log confirmed when Midas is executed
Event ID 7040 is recorded when there is a change in the service settings. The changed service settings are recorded as EventData, and when Midas is executed, the changes in the services are recorded as shown in Table 1.
| Service | Description |
|---|---|
| Function Discovery Resource Publication | Used to publish resources on a computer to other devices on a network |
| SSDP Discovery | Used to discover devices on a network |
| Secure Socket Tunneling Protocol Service | Used to establish a VPN connection over the Internet |
| UPnP Device Host | Used to establish communication between Universal Plug and Play (UPnP) compatible devices and computers, enabling automatic configuration and service provision on the network |
Similar characteristics have also been recorded in the Axxes ransomware, which is suspected to be a variant of Midas.
BadRabbit
BadRabbit is ransomware first confirmed in 2017. It is characterized in that traces (Event ID: 7045) of installing the component cscc.dat used for encryption are recorded when it is executed.
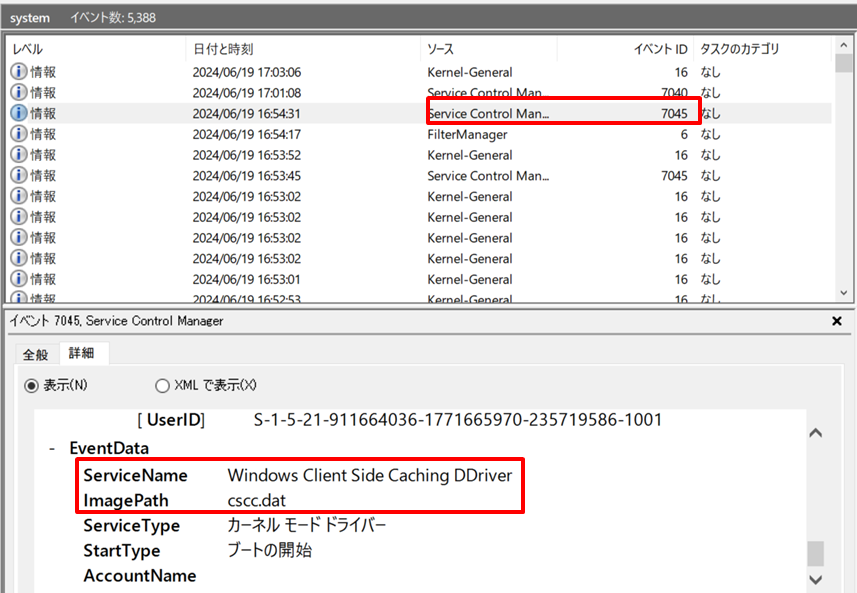
Figure 4: Event log confirmed when BadRabbit is executed
Bisamware
Bisamware is ransomware first identified in 2022. It is a ransomware targeting Windows users, and it is known to be distributed by exploiting vulnerabilities in tools provided by Microsoft. When Bisamware is executed, traces of the start (event ID: 1040) and end (event ID: 1042) of the Windows Installer transaction are recorded.
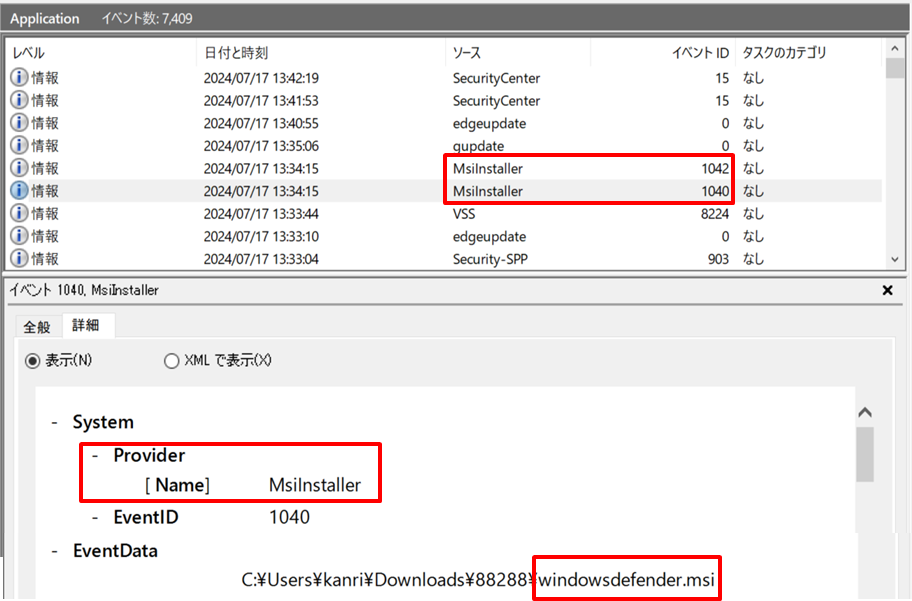
Figure 5: Event logs confirmed during Bisamware execution
Other common event logs recorded by ransomware
Although there was no apparent connection from the publicly available information, there are some types of ransomware with common characteristics in traces in event logs.
- shade
- GandCrab
- AKO
- avoslocker
- BLACKBASTA
- VICE SOCIETY
The traces (Event ID: 13, 10016) of these types of ransomware show that they did not function properly because they lacked permission to access COM server applications related to the Volume Shadow Copy Service at the time of execution.
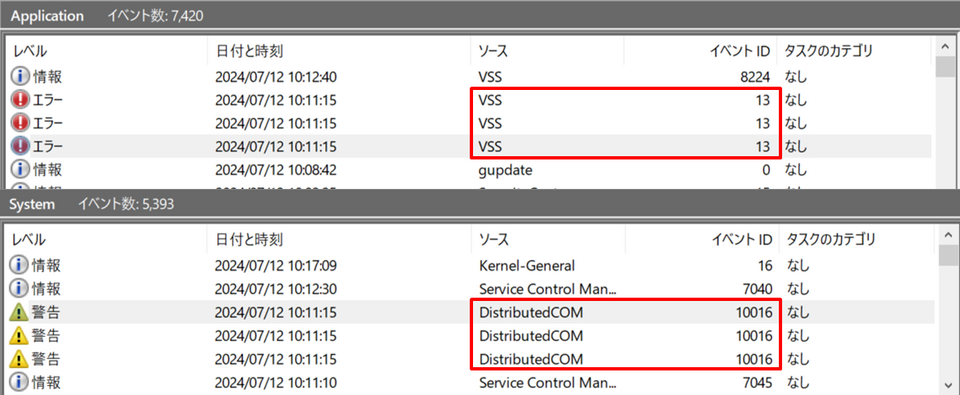
Figure 6: Event logs confirmed during execution
In Closing
Although we were unable to find any event logs that would lead to the identification of WannaCry, Petya, Ryuk, and other older types of ransomware, we identified multiple event logs that lead to the identification of the relatively new ransomware types introduced in this article. Event logs can only support damage investigations and attribution, but in situations where a lot of information is deleted or encrypted, investigating everything that could be useful may provide some good insights. Please consider investigating event logs when investigating damage from human-operated ransomware attacks.
Kyosuke Nakamura
Translated by Takumi Nakano

