*Please note that this article is a translation of the Japanese versio...
List of “Incident”
-
-
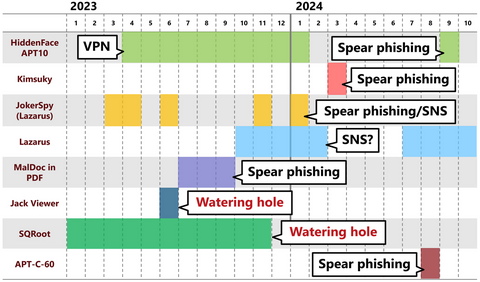
There have recently been reports of unauthorized access in Japan, usin...
-
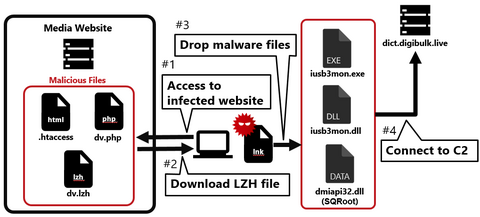
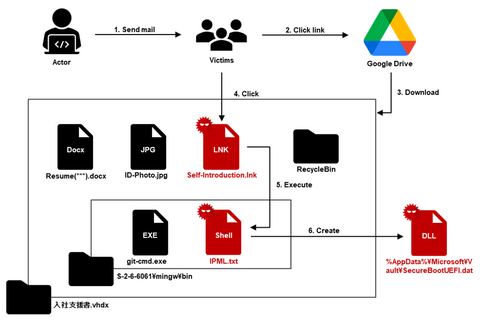
Continuing from the previous article, Part 2 covers another case of a watering hole attack. This time, we will look at the case of a media-related website exploited in 2023. Flow of the attack Figure 1 shows the flow of the watering hole attack. When someone accesses the tampered website, an LZH file is downloaded, and when they execute the LNK file in the LZH file, their PC becomes infected...
-
Nowadays, many people probably recognize exploit of vulnerabilities in publicly exposed assets such as VPN and firewalls as the attack vector. In fact, many security incidents reported to JPCERT/CC also involve such devices. This is because vulnerabilities in VPN devices are exploited not only by APT groups but also by many other groups such as ransomware actors and cyber crime actors, and the number of incidents is high accordingly. As...
-
JPCERT/CC has confirmed an attack against an organization in Japan in ...
-
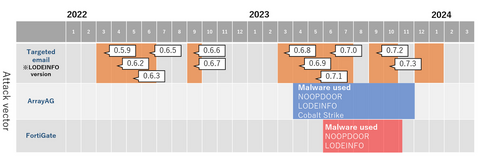
JPCERT/CC has been observing attack activities by MirrorFace LODEINFO ...
-
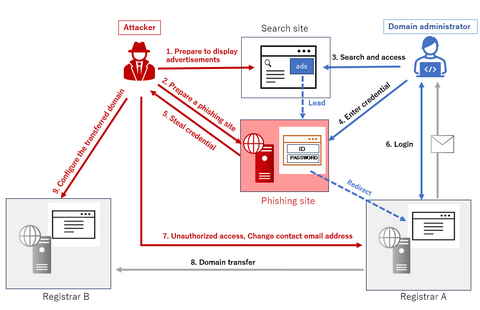
In early July 2023, JPCERT/CC confirmed a case of domain hijacking in which a domain used in Japan was unauthorizedly transferred to another registrar. This blog post describes the attack case. Attack overview Figure 1 shows the attack flow. The attacker first prepared a phishing site, which pretended to be a registrar on search site advertisements. Figure 1: the attack flow An attacker can steal account information and password (hereafter...
-
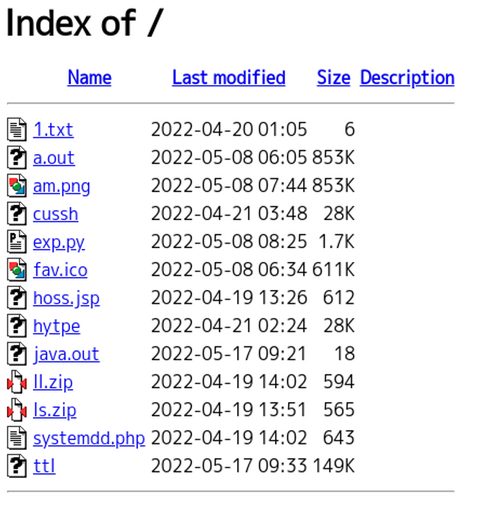
Around May 2022, JPCERT/CC confirmed an attack activity against Japanese organizations that exploited F5 BIG-IP vulnerability (CVE-2022-1388). The targeted organizations have confirmed that data in BIG-IP has been compromised. We consider that this attack is related to the activities by BlackTech attack group. This blog article describes the attack activities that exploit this BIG-IP vulnerability. Attack code that exploits the BIG-IP vulnerability Below is a part of the attack code...
-
JPCERT/CC releases a URL dataset of phishing sites confirmed from January 2019 to June 2022, as we received many requests for more specific information after publishing a blog article on trends of phishing sites and compromised domains in 2021. The list is available in the following GitHub repository. Phishing URL dataset from JPCERT/CC https://github.com/JPCERTCC/phishurl-list/ Each column contains the following: date: Date confirmed by JPCERT/CC URL: Entire URL of a phishing...
-
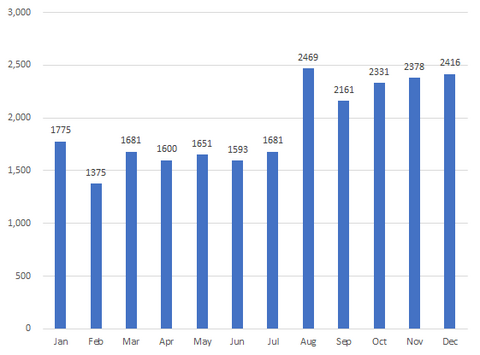
JPCERT/CC received 44,242 incident reports in 2021 and of that 23,104 ...




.png)