Hi, this is You 'Tsuru' Nakatsuru again from Analysis Center. This past summer, I joined the “Security Camp 2015” in Japan as a trainer for a malware analysis training course, which was held for students aged 22 and under living in Japan, with the aim of discovering top, young talents. This blog entry is to introduce the malware analysis training materials which I used at Security Camp 2015 as below....
List of “2015”
-
-
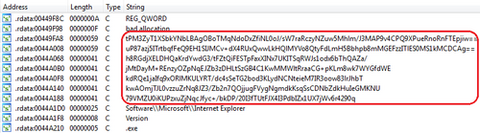
Hello, this is You ‘Tsuru’ Nakatsuru at Analysis Center. As introduced in the previous blog post, my colleagues presented on the attacks arising in Japan at CODE BLUE 2015, entitled “Revealing the Attack Operations Targeting Japan”. In this entry, I will introduce the details of an IDAPython script “emdivi_string_decryptor.py”, which JPCERT/CC developed to analyse Emdivi, a remote control malware. The script was also introduced in our presentation at CODE BLUE...
-
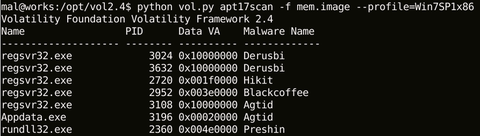
Hello again – this is Shusei Tomonaga from Analysis Center. This blog entry is to introduce “apt17scan.py” created by JPCERT/CC to detect certain malware used in targeted attacks, and to extract its configuration information. It is a plugin for the Volatility Framework (hereinafter “Volatility”), a memory forensics tool. My colleague Yuu Nakamura and I had the honour to introduce this at CODE BLUE 2015, an international conference for information security...
-
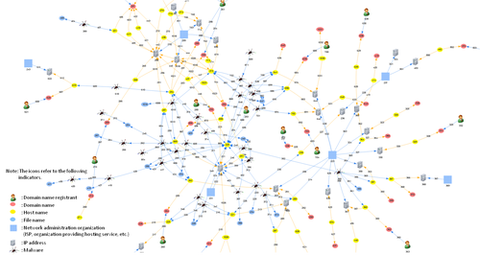
You may well have heard of the May cyber attack in Japan against the Japan Pension Service – a high-profile case seen in the first half of this year, where 1.25 million cases of personal data was exposed. According to the Japan Pension Service, the data leaked included names and ID numbers, and for some cases, dates of birth and home addresses. The official reports(1) say that the massive leak...
-
Hello again, it’s Yuka at the Global Coordination Division. Following my recent trip to Malaysia to join APCERT Annual General Meeting and Conference 2015, I had my first travel to Europe – and that was to Bucharest, Romania to attend a conference hosted by CERT-RO, the National CSIRT of Romania. They host a conference annually, and this year it was the 5th time for this event, held from 5th -...
-
Hi again, it’s Yuka from Global Coordination Division and also serving as APCERT Secretariat. It’s been a while since I wrote here last time. My entry this time is about the biggest event of APCERT which we just recently attended, the Annual General Meeting (AGM) and Conference 2015 in Kuala Lumpur, Malaysia on 6-10 September. This event, hosted by CyberSecurity Malaysia (MyCERT), marked the 12th annual conference for APCERT. What...
-
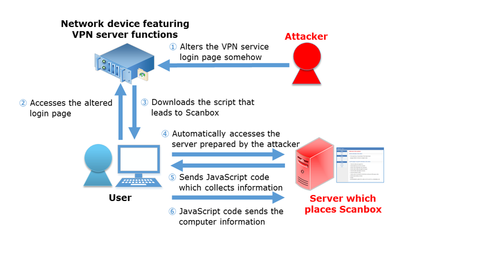
Hi, it’s Shusei Tomonaga again from the Analysis Center. JPCERT/CC has confirmed several attack cases around May 2015, which attempt to steal information of computers leveraging specific network devices featuring VPN server functions. The target of the reconnaissance varies from installed software to keylogs, and it is presumed that the attacker has aimed to steal such information from computers which attempt to login to VPN servers through altered login pages....
-
Hi, it’s Shusei Tomonaga again from the Analysis Center. My previous post discussed the mitigation effects against damages caused by malware infection by enabling Internet Explorer’s (hereafter “IE”’s) Protected Mode. In this article, I’d like to introduce an even stronger security function called “Enhanced Protected Mode”, which is a feature of IE 10 and 11 - its overview and preventive effects against damages caused by malware infection. OVERVIEW OF ENHANCED...
-
Hi, it’s Shusei Tomonaga again from the Analysis Center. PoisonIvy, a Remote Access Tool/Trojan (RAT) often used in targeted attacks, had been widely seen until around 2013. Since then, the number of cases using PoisonIvy in such attacks decreased, and there was no special variant with expanded features seen in the wild. However, recently, we have observed cases where PoisonIvy with expanded features in its communication function were used for...
-
Hello, Taki here, and its currently rainy season in Japan. Just recently, I attended the 27th FIRST Annual Conference, held on June 14-19 , 2015 in Berlin – a city that I visited for the first time. (Photo by Hiroshi Kobayashi) I would like to go over some activities that JPCERT/CC was involved in during the conference. This year I attended together with 3 colleagues, Yurie Ito, Koichiro (Sparky) Komiyama...