VPN Servers Altered by Attacker Leading to Scanbox, a Reconnaissance Framework
Hi, it’s Shusei Tomonaga again from the Analysis Center. JPCERT/CC has confirmed several attack cases around May 2015, which attempt to steal information of computers leveraging specific network devices featuring VPN server functions. The target of the reconnaissance varies from installed software to keylogs, and it is presumed that the attacker has aimed to steal such information from computers which attempt to login to VPN servers through altered login pages. In this post, I’d like to introduce the details of the attack and effective countermeasures you may take.
OVERVIEW OF ATTACK
Through our analysis, we were able to reveal the mechanism of how VPN account information could be stolen, using a framework called Scanbox. The Scanbox consists of (1) JavaScript code to be sent to the browser, (2) the server to receive the collected information and (3) tools to analyze information collected in the server. The overall flow of attack is shown in Figure 1.
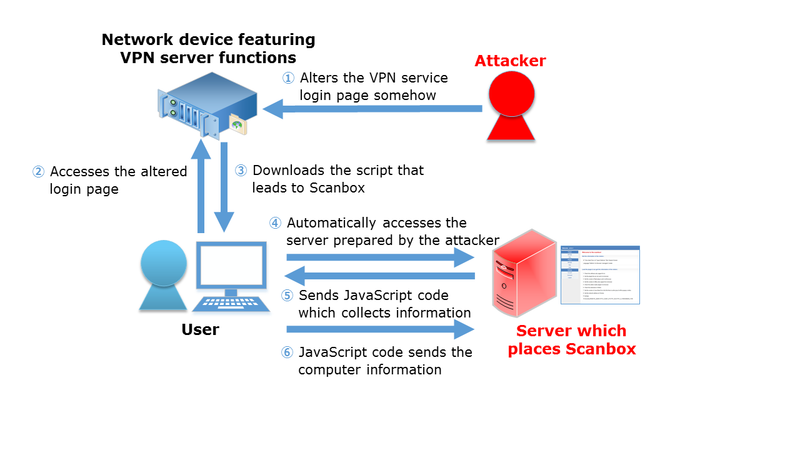 |
In this attack, the attacker somehow alters VPN service login pages of such network devices and embeds scripts, which leads the user to access a different server in addition to its originally intended behaviour. The JavaScript code of Scanbox, which collects information of users’ computers, is placed in the accessed server, and computers accessing the altered login page are led to download and execute it. This JavaScript code steals information such as the computer’s IP address, installed software and information entered by the user in the VPN session, and keeps sending the information to the Scanbox information collection server until the browser is closed.
ALTERED VPN SERVER LOGIN PAGES
Through our analysis, we confirmed that login pages of specific network devices with VPN server functions were altered in several cases. As of now, we have not been able to specify the method of alteration, but there is possibility that a network device vulnerability was leveraged.
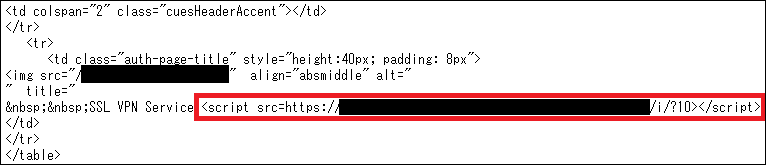
The altered login page was embedded with a script tag as shown in Figure 2. When the user accesses the Web SSL VPN login page via the browser, the user is unknowingly entrapped into the Scanbox due to this script.
 |
SCANBOX
The Scanbox, set up at the redirected site, is a framework to steal information, often used in targeted attacks. Attacks by Scanbox start by downloading and executing a JavaScript code. This JavaScript code collects the computer information such as installed applications and IP address, etc., and sends them to the Scanbox information collection server. (Note that the Scanbox JavaScript code can not only collect computer information, but can also add functions to infect the computer with malware by leveraging a vulnerability.)
Table 1 lists Scanbox’s information collection function which we confirmed in this attack.
| Item | Function | Collected Information |
|---|---|---|
| 1 | Software Scan | Information of installed software (anti-virus software, Windows patch, etc.) |
| 2 | Flash Scan | Adobe Flash Player versions |
| 3 | Office Scan | Microsoft Office versions |
| 4 | Adobe reader scan | Adobe Reader installation status |
| 5 | FireFox Extentions scan | Firefox and plugin installation status |
| 6 | Java scan | Java versions |
| 7 | IP scan | IP address information (function for Chrome) |
| 8 | Keylogs | Keystrokes within the browser (sent every 5 seconds) |
| 9 | Ip list | IP address information HTTP_X_FORWARDED_FOR |
| 10 | Drives scan | Drive information |
As shown in Item 8 in the above table, Scanbox can also collect such information as entered in Web forms. As such, information entered in the login site may possibly leak. For keystrokes within the browser, the Scanbox JavaScript code sends the collected information to the server every 5 seconds until the browser (tab) reading the JavaScript code is closed. Other information in Table 1 is sent to the Scanbox information collection server upon respective functions’ startup. (For further information on Scanbox, please visit the AlienVault Blog (Reference [1]) for detailed explanation.)
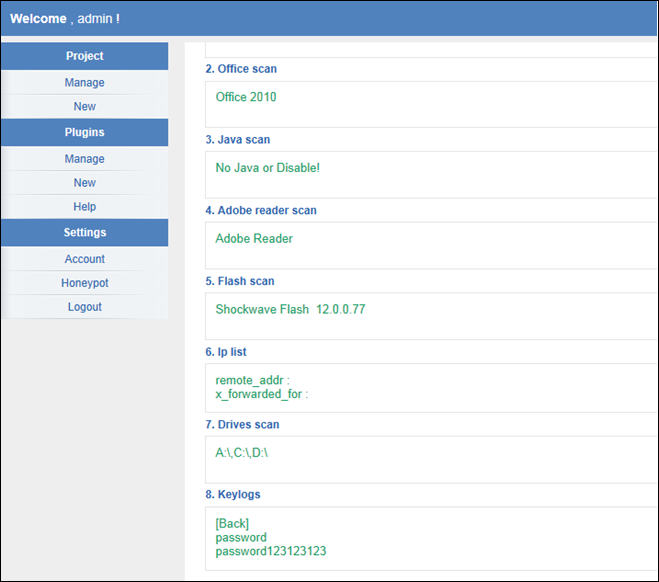
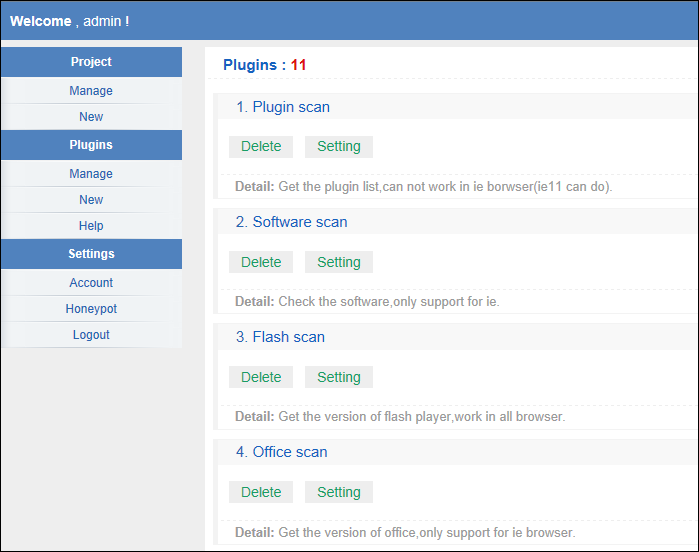
Furthermore, Scanbox has a Web interface for the attacker to analyze the collected information. As shown in Figure 3, the collected information can be browsed on the Website. Information collected by Scanbox can also be customized from the Website as shown in Figure 4.
 |
 |
IN SUMMARY
As of now, the method of the VPN server login page alteration is unknown. However, we presume that there is high possibility that a known vulnerability was leveraged, so we recommend users to apply patches and update firmware. We also recommend users to check if there are any scripts that are unintentionally embedded in the login pages.
Although attacks using Scanbox do not involve malware infection, it needs caution as it steals computer information and information entered in the browser. There is possibility that the attacker is planning for the next phase of attack based on the collected information, therefore, it is necessary to endeavor to detect the attack in an early stage, as well as to keep a close watch over the attacker’s next move and to strengthen protection against it.
Last but not least, an effective countermeasure against Scanbox is to avoid executing JavaScript in your browser downloaded from a Website which is not trusted on your browser.
Thank you for reading and see you again.
- Shusei Tomonaga
REFERENCE
[1] AlienVault - Scanbox: A Reconnaissance Framework Used with Watering Hole Attacks

