Enhanced Protected Mode in Internet Explorer
Hi, it’s Shusei Tomonaga again from the Analysis Center. My previous post discussed the mitigation effects against damages caused by malware infection by enabling Internet Explorer’s (hereafter “IE”’s) Protected Mode. In this article, I’d like to introduce an even stronger security function called “Enhanced Protected Mode”, which is a feature of IE 10 and 11 - its overview and preventive effects against damages caused by malware infection.
OVERVIEW OF ENHANCED PROTECTED MODE
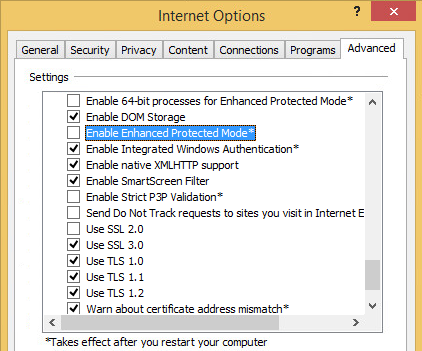
Unlike Protected Mode, Enhanced Protected Mode is turned off by default. To enable it, you must tick the “Enable Enhanced Protected Mode” option in the Security section of IE’s Tools > Internet Options > Advanced tab, and then restart IE.
 |
This feature is available in the following OS:
- Windows 10 (32-bit/64-bit)
- Windows 8.1 (32-bit/64-bit)
- Windows 8 (32-bit/64-bit)
- Windows 7 (64-bit) *Not available on 32-bit OS
When Enhanced Protected Mode is enabled, IE will run in the following mode:
- 64-bit mode (only in a 64-bit mode Windows)
- A sandbox environment called AppContainer (only on Windows 8, 8.1 and 10)
Even on a 64-bit Windows, IE will run in 32-bit mode if the Enhanced Protected Mode is turned off. On a 64-bit Windows, IE will run in 64-bit mode by enabling the Enhanced Protected Mode, plus in case of IE 11 for Windows 8 and later, by checking the “Enable 64-bit processes for Enhanced Protected Mode” in “Internet options”. Furthermore, IE that is launched from Window Store applications in Windows 8, etc., will run in 64-bit mode. Also, Microsoft “Edge”, the all new web browser introduced with Windows 10, will run in 64-bit mode by default.
AppContainer is a sandbox environment introduced in Windows 8, which limits process operations more strictly than does the Integrity Level (in Protected Mode). In a widely known case, the Windows Store applications runs in an AppContainer environment, and an Enhanced Protected Mode designated IE also runs in an AppContainer environment.
 |
IE WITH ENHANCED PROTECTED MODE
In order to validate how Enhanced Protected Mode is effective in reducing damage by malware infection through IE, we analysed using an exploit code that leverages CVE-2014-6332 (vulnerability in IE)which runs PowerShell to attempt to execute an unauthorized code. The verification was conducted on IE 11 for Windows 8.1.
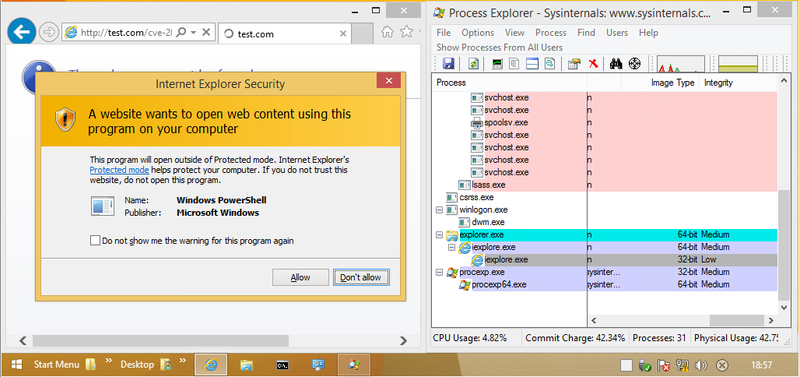
As shown in Figure 3, the attack was successfully conducted in IE running in 32-bit with the Enhanced Protected Mode turned off; the PowerShell is running.
 |
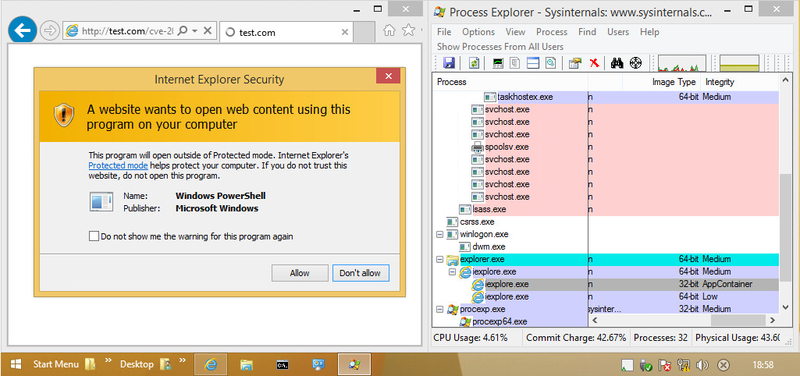
Furthermore, Figure 4 shows the verification of IE running in 32-bit with the Enhanced Protected Mode enabled. It shows that the attack was successfully conducted under this condition as well, and the PowerShell is running.
 |
On the other hand, in IE running in 64-bit with the Enhanced Protected Mode enabled, the Powershell fails to run, and IE shut down unexpectedly, as shown in the following figure.
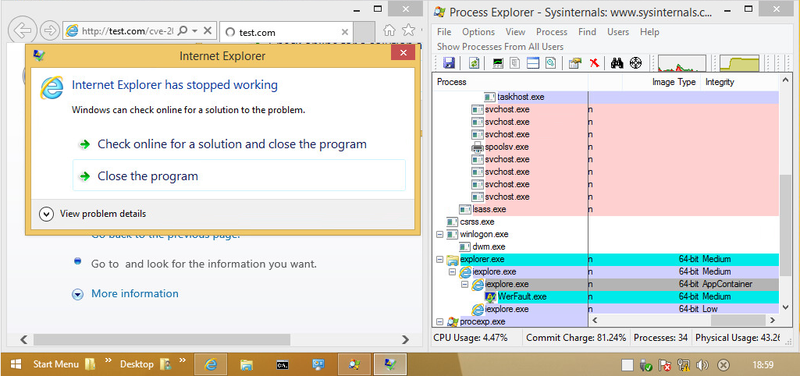 |
The reason for IE’s unexpected shutdown in 64-bit mode is that the exploit code executed in the IE process was created exclusively for a 32-bit environment. All the exploit codes leveraging vulnerability in IE that JPCERT/CC has analyzed so far were created exclusively for 32-bit OS. Therefore, if IE is running in 64-bit mode, these exploit codes fail to execute as intended by the attacker.
Note that AppContainer is not supported in Windows 7; therefore IE just runs in 64-bit mode when Enhanced Protected Mode is enabled. In this case, the attack also fails, similarly to the test results in Windows 8, etc.
IN SUMMARY
Running IE in 64-bit mode with Enhanced Protected Mode enabled is a strongly effective countermeasure against attacks targeting IE, until an exploit code for 64-bit emerges. Furthermore, I did not touch on the functions of AppContainer in this verification, but when AppContainer is enabled, it basically only allows access to limited resources such as files created in IE, favorites folders (%UserProfile%Favorites), etc. Therefore, even if malware infection occurs, we can expect a higher mitigation effect than that of the Protected Mode which I touched upon in the previous post.
Last but not least, please note that when you enable Enhanced Protected Mode, not only the malware but also incompatible browser extensions such as add-ons, ActiveX controls, etc., may not work correctly. So I would recommend users to check the compatibility before actually enabling the Enhanced Protected Mode.
Thank you for reading and see you again.
- Shusei Tomonaga
REFERENCE
[1] Understanding Enhanced Protected Mode

