PoisonIvy adapts to communicate through Authentication Proxies
Hi, it’s Shusei Tomonaga again from the Analysis Center.
PoisonIvy, a Remote Access Tool/Trojan (RAT) often used in targeted attacks, had been widely seen until around 2013. Since then, the number of cases using PoisonIvy in such attacks decreased, and there was no special variant with expanded features seen in the wild. However, recently, we have observed cases where PoisonIvy with expanded features in its communication function were used for attacks.
In this blog post, I will discuss PoisonIvy’s expanded features.
PoisonIvy’s Traditional Communication Function
Traditionally, PoisonIvy had used a proprietary protocol to communicate with C&C servers. Within organizations using proxies, PoisonIvy attempted to send data to C&C servers via proxies by using CONNECT method or SOCKS (version 4). This was achieved by pre-setting the proxy server information in PoisonIvy itself, or by enabling the configuration to obtain the proxy information from Internet Explorer. Figure 1 shows an example of PoisonIvy’s communication using CONNECT method.
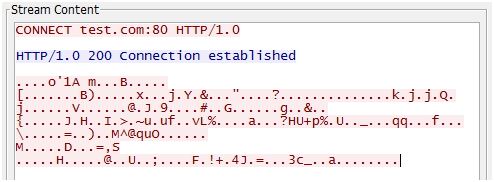 |
In the past, PoisonIvy was not able to communicate with external C&C servers when authentication was necessary for a proxy connection.
Transition to HTTP Communication
Recently, we found that PoisonIvy’s settings changed from its traditional proprietary protocol to HTTP for connecting to C&C servers. This means that, as shown in Figure 2, the new variant now sends POST requests that include the data to send to C&C servers in the body field.
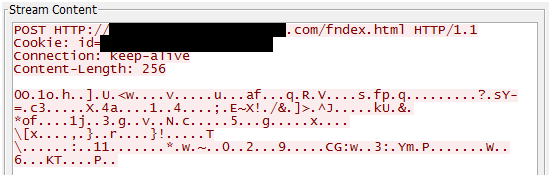 |
Our analysis revealed that this new PoisonIvy variant has significant changes in its communication function compared to the traditional one (as shown in Figure 3). The code used for its traditional proprietary communication was replaced with code for HTTP communication.
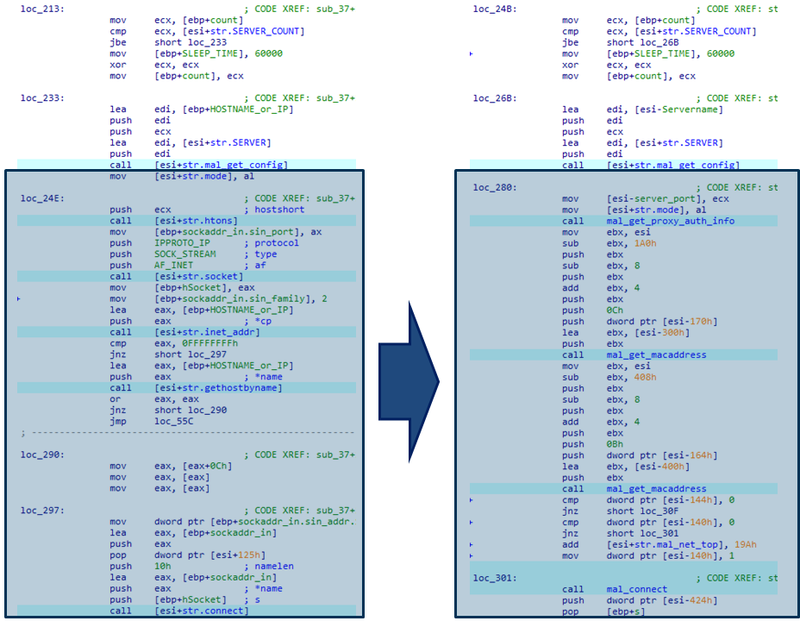 |
Adaptability to Authentication Proxies
Furthermore, this PoisonIvy variant has adapted to communicate through authentication proxies. When it attempts to connect to C&C servers via proxies, and an error is returned from the authentication proxy (HTTP status code 407), it sniffs the communication in promiscuous mode. If this communication includes the string “Proxy-Authentication: Basic”, it writes this string to the following registry entry.
●HKEY_LOCAL_MACHINE\SOFTWARE\Classes\BJ\STATIC\MessageFile
Figure 4 shows an example of sniffed information that we actually observed in the registry.
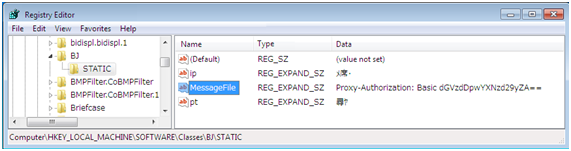 |
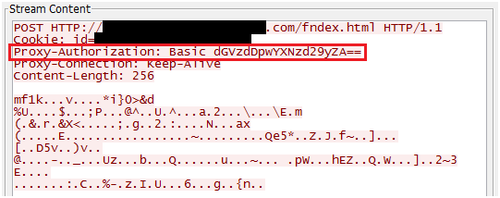
Later when connecting to C&C servers via proxies, PoisonIvy adds the string written in the registry entry to the HTTP header, and attempts to pass through the authentication proxy (as shown in Figure 5). Note that PoisonIvy requires administrative privileges for the proxy authentication communications. This is because, without administrative privileges, it cannot create the above registry entry, thus it fails to communicate the authentication information.
 |
In Summary
Attacks using PoisonIvy has hit a lull lately, but with the new variant introduced here, we never know it may be used actively again, so caution needs to be taken.
Furthermore, PoisonIvy is not the only case - there are many different types of malware that have adapted to communicate through authentication proxies. PlugX, covered in an earlier blog entry , is no exception, and we believe that still more types of malware will adapt to communicate through authentication proxies in the future.
Thank you for reading and see you again soon.
- Shusei Tomonaga
Appendix
SHA-256 hash value of the PoisonIvy variant
●d1aa00b6b11fbefd2dda3b458d9fb5e975865b564bf1c289a6f464b14ad748cc

