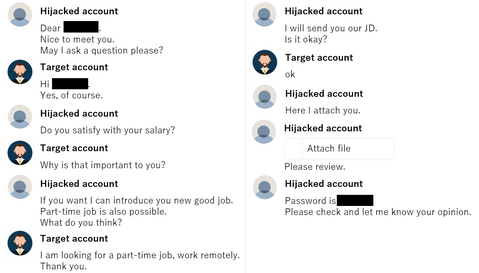
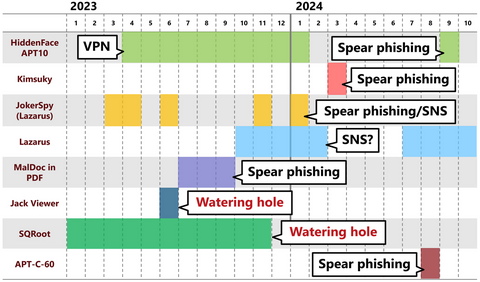
There have recently been reports of unauthorized access in Japan, usin...
List of “朝長 秀誠 (Shusei Tomonaga)”
-
-
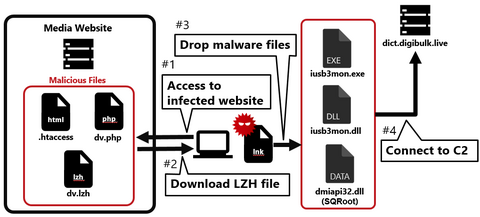
Continuing from the previous article, Part 2 covers another case of a watering hole attack. This time, we will look at the case of a media-related website exploited in 2023. Flow of the attack Figure 1 shows the flow of the watering hole attack. When someone accesses the tampered website, an LZH file is downloaded, and when they execute the LNK file in the LZH file, their PC becomes infected...
-
Nowadays, many people probably recognize exploit of vulnerabilities in publicly exposed assets such as VPN and firewalls as the attack vector. In fact, many security incidents reported to JPCERT/CC also involve such devices. This is because vulnerabilities in VPN devices are exploited not only by APT groups but also by many other groups such as ransomware actors and cyber crime actors, and the number of incidents is high accordingly. As...
-
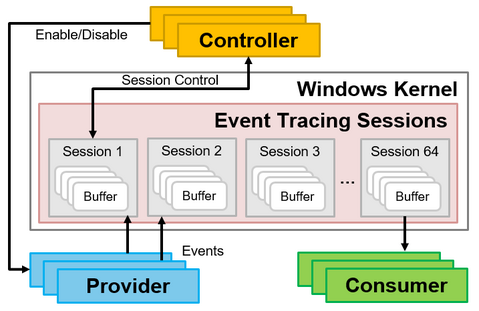
Many people may think of EventLogs when one mentions Windows OS logs. When investigating incidents such as malware infections, it is common to analyze the Windows OS EventLogs to find traces that may help uncover the incident. However, since the EventLog is not designed to detect suspicious behavior on Windows OS, you may not always find the information you are looking for when investigating an incident. Therefore, it is necessary...
-
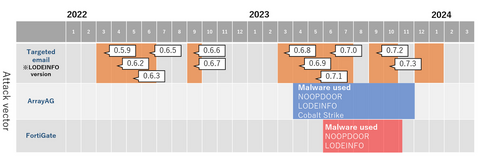
JPCERT/CC has been observing attack activities by MirrorFace LODEINFO ...
-
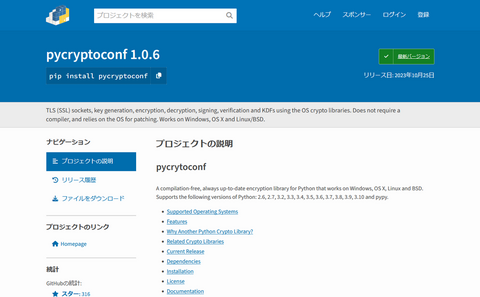
JPCERT/CC has confirmed that Lazarus has released malicious Python packages to PyPI, the official Python package repository (Figure 1). The Python packages confirmed this time are as follows: pycryptoenv pycryptoconf quasarlib swapmempool The package names pycryptoenv and pycryptoconf are similar to pycrypto, which is a Python package used for encryption algorithms in Python. Therefore, the attacker probably prepared the malware-containing malicious packages to target users' typos in installing Python packages....
-
As attacks become more fileless and malware gets more obfuscated, it is getting more difficult to determine whether there is a malicious intent from a file by itself. For this reason, malware detection methods that utilize sandboxes and AI, as well as technologies that detect suspicious behavior after malware infection, such as EDR, have now become common. Even so, malware that antivirus software cannot detect is often found during actual...
-
JPCERT/CC has observed attacks on cryptocurrency exchanges believed to be related to DangerousPassword attack campaign (also known as CryptoMimic or SnatchCrypto) continuously since June 2019. For many years, attackers have been using an attack technique of infecting targets with malware by sending shortcut files to them via email. However, it is known that they also use various other patterns of attacks to infect the targets with malware. This article will...
-
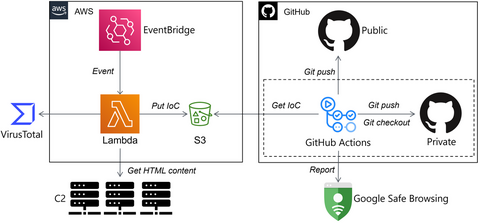
I believe that automating analysis is a challenge that all malware analysts are working on for more efficient daily incident investigations. Cloud-based technologies (CI/CD, serverless, IaC, etc.) are great solutions that can automate MAOps efficiently. In this article, I introduce how JPCERT/CC automates malware analysis on the cloud, based on the following case studies. Malware C2 Monitoring Malware Hunting using Cloud YARA CI/CD system Surface Analysis System on Cloud Memory...
-
JPCERT/CC released the latest version (v1.6) of LogonTracer, a tool to support event log analysis. Previously, LogonTracer could not investigate multiple incidents simultaneously, but this update adds support for managing multiple logs. In addition, Sigma can now be used to investigate the presence of suspicious logs in the event log. This article introduces these updates. For other updated items, please refer to the following release: https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.6.0 Log Management Feature When...