Beware of Contacts through LinkedIn: They Target Your Organization’s Property, Not Yours
There have recently been reports of unauthorized access in Japan, using LinkedIn as the initial infection vector.
FBI, DC3, and NPA Identification of North Korean Cyber Actors, Tracked as TraderTraitor, Responsible for Theft of $308 Million USD from Bitcoin.DMM.com
https://www.fbi.gov/news/press-releases/fbi-dc3-and-npa-identification-of-north-korean-cyber-actors-tracked-as-tradertraitor-responsible-for-theft-of-308-million-from-bitcoindmmcom
This type of attack that exploits LinkedIn is mainly used by Lazarus attack group, and JPCERT/CC has continuously confirmed such attacks against organizations in Japan since around 2019. Past incident cases suggest that using LinkedIn on a host for business is highly dangerous and should be avoided unless there is any special reason. To avoid such risks, please consider restricting the use of SNS on work devices (e.g., prohibit installing SNS applications, configure access control, etc.) in your organization and implementing other measures. If you choose to allow your employees to use SNS on their work devices, it is recommended to create rules and discuss measures to protect employees in case they are contacted by attackers.
For the purpose of describing the danger of such attacks once again, this blog post introduces some cases of attacks by Lazarus group exploiting LinkedIn which have been reported by JPCERT/CC in the past. The below section describes 3 operations identified in Japan previously and associated with Lazarus attack group. Attackers who attempt to contact their target through LinkedIn have the following characteristics. If you are contacted by an unknown individual with any of these characteristics, you should be alerted.
- Requests you to change the communication tool from LinkedIn to something else
- Attempts to make you download and execute files
- Persistently checks whether you have executed sent (downloaded) files and about your system environment
- Attackers often use English in attacks through LinkedIn, while most targeted emails are written in Japanese (Some cases with Japanese text have been confirmed)
- Pretends to be a recruiter and post expensive fees
Operation Dream Job
This operation targets companies in defense industry in various countries, and attacks have been confirmed in Japan as well. Attackers hijack legitimate LinkedIn accounts (of HR department representatives of defense contractors) and contact employees of the target organization through LinkedIn with recruiting related topics. After that, while changing the communication tool from LinkedIn to Skype or WhatsApp, the attackers eventually make their target download and execute a malicious Word document to infect the target devices with malware. Figure 1 shows the flow of the attack.
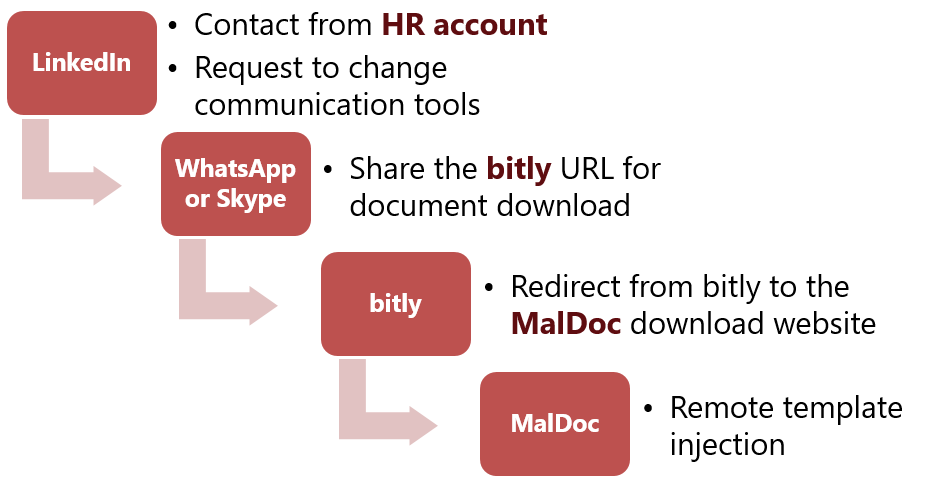
As shown in this example, LinkedIn accounts exploited for the attack may not be the attackers’ but legitimate ones hijacked, and thus it is sometimes difficult to identify anything suspicious from the accounts themselves.
Refer to the following documents for further information on this operation.
https://github.com/JPCERTCC/Lazarus-research/blob/main/slides/CODEBLUE2021_The-Lazarus-Groups-Attack-Operations-Targeting-Japan.pdf(PDF)
Operation Dangerous Password
This operation has been ongoing since 2019, targeting crypto currency exchangers. The attackers contact employees of the target organization through LinkedIn and attempt to have them download a ZIP file and execute the malicious file inside. For several years since this attack was first identified, the name of the malicious LNK file contained in the ZIP file remained the same (Password.txt.lnk), and the malware itself had not changed significantly. Later, attack methods have gradually changed, and recently it can target macOS or exploit VHDs, OneNote files, etc.
Attack Trends Related to DangerousPassword
https://blogs.jpcert.or.jp/en/2023/05/dangerouspassword.html
DangerousPassword attacks targeting developers’ Windows, macOS, and Linux environments
https://blogs.jpcert.or.jp/en/2023/07/dangerouspassword_dev.html
The attackers exploited a large number of LinkedIn accounts, and in one of the cases, the account of an employee of a crypto currency exchanger in Japan was hijacked, and the attacker contacted financial institutions and developers both in Japan and overseas through the account. Figures 2 and 3 show examples of interactions with attackers on LinkedIn.
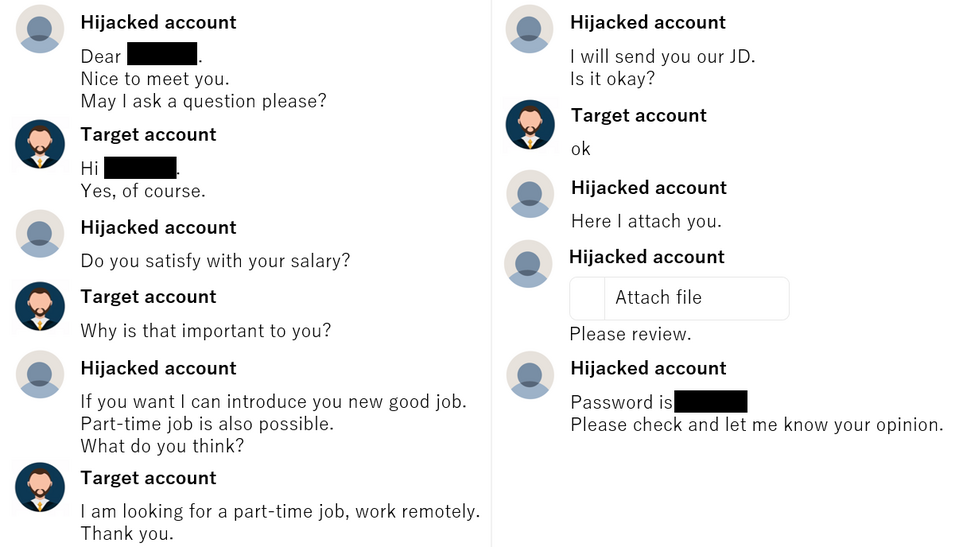
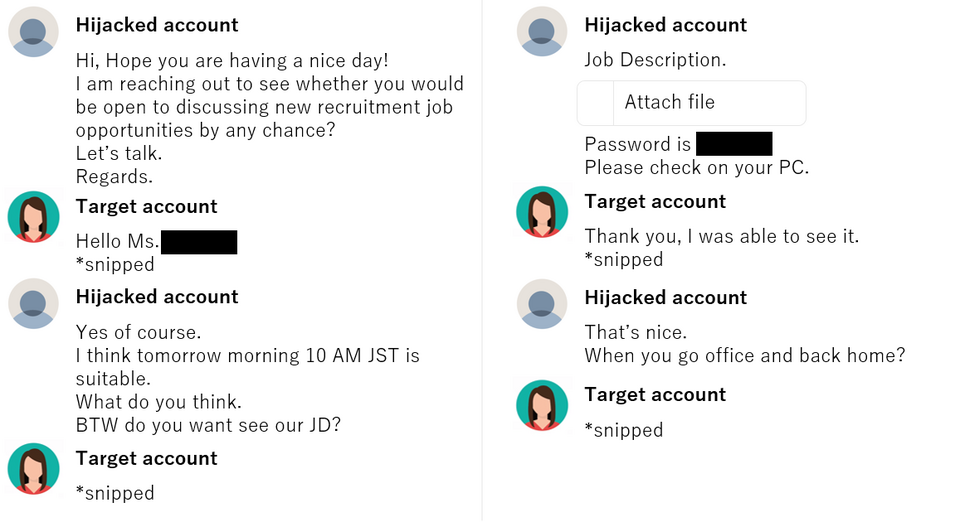
Refer to the following documents for further information on this operation.
https://www.jpcert.or.jp/english/doc/IR_Report2019Q4_en.pdf
https://www.jpcert.or.jp/english/doc/IR_Report2021Q4_en.pdf
https://www.jpcert.or.jp/english/doc/IR_Report2022Q3_en.pdf
Operation AppleJeus
This operation is an attack campaign targeting crypto currency users (organizations). Attacks have been confirmed in various countries, and investigations on C2 servers revealed that there are a number of victims. The attackers contact their target’s LinkedIn account and share a link leading to Telegram. After that, they attempt to make the target download a malicious MSI file through Telegram and execute it. The file was disguised as a crypto currency exchange tool.
Figure 4 shows an example of messages sent by an attacker through LinkedIn.
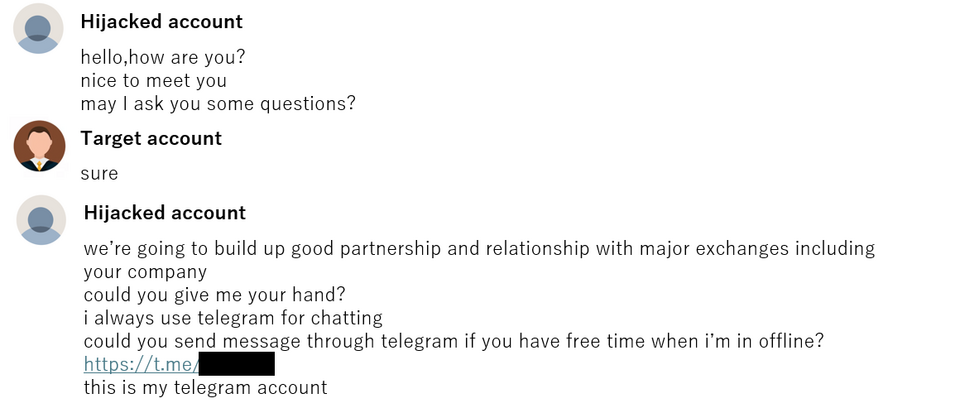
Refer to the following documents for further information on this operation.
https://www.jpcert.or.jp/english/doc/IR_Report2021Q3_en.pdf
In Closing
Besides the 3 operations covered in this article, Japanese security vendors have also released information on other recent attack cases associated with Lazarus attack group [1] [2]. This type of attacks exploiting SNS is expected to persist, and thus attention should be paid. Please review and consider how your organization lets its employees use their SNS on work devices.
Shusei Tomonaga
(Translated by Takumi Nakano)
References
[1] マクニカ セキュリティ研究センターブログ: 北からのジョブオファー: ソフトウェア開発者を狙うContagious Interview
https://security.macnica.co.jp/blog/2024/10/-contagious-interview.html
[2] OtterCookie, new malware used in Contagious Interview campaign
https://jp.security.ntt/tech_blog/en-contagious-interview-ottercookie

