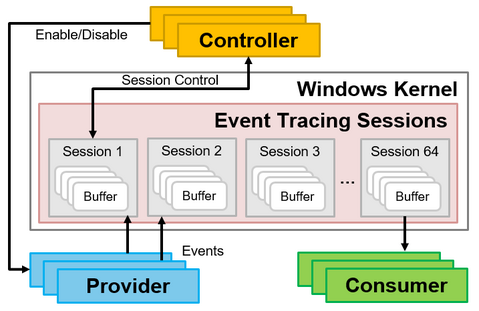
Many people may think of EventLogs when one mentions Windows OS logs. When investigating incidents such as malware infections, it is common to analyze the Windows OS EventLogs to find traces that may help uncover the incident. However, since the EventLog is not designed to detect suspicious behavior on Windows OS, you may not always find the information you are looking for when investigating an incident. Therefore, it is necessary...
List of “volatility”
-
-
Volatility 3 had long been a beta version, but finally its v.1.0.0 was released in February 2021. Since Volatility 2 is no longer supported [1], analysts who used Volatility 2 for memory image forensics should be using Volatility 3 already. In this blog post, I introduce a tip for Volatility 3: how to use Volatility 3 offline. This instruction focuses on analyzing Windows OS memory image. What is the problem...
-
The Volatility Foundation released Volatility 3 Public Beta, a new version of Volatility Framework in October 2019. The version not only offers compatibility with Python 3 but also has a lot of functional updates from Volatility 2. (Please see Volatility 3's official page for more details.) Particularly, creating plugins is much easier with Volatility 3 compared to the previous version. Volatility 3’s official release is planned for August 2020, and...
-
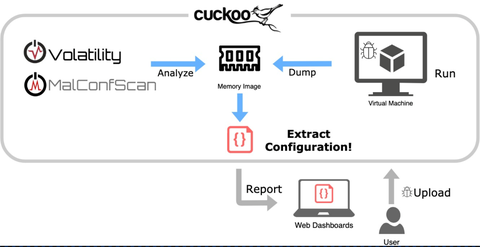
In malware analysis, extracting the configuration is an important step. Malware configuration contains various types of information which provides a lot of clues in incident handling, for example communication details with other hosts and techniques to perpetuates itself. This time, we will introduce a plugin “MalConfScan with Cuckoo” that automatically extracts malware configuration using MalConfScan (See the previous article) and Cuckoo Sandbox (hereafter “Cuckoo”). This plugin is available on GitHub....
-
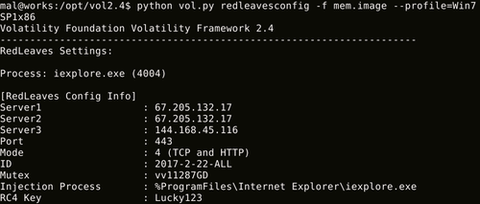
Our previous blog entry introduced details of RedLeaves, a type of malware used for targeted attacks. Since then, we’ve seen reports including those from US-CERT that Management Service Providers (MSPs) have been targeted [1] [2]. In the US-CERT report, some instances have been identified where RedLeaves malware has only been found within memory with no on-disk evidence because of the behavior of self-elimination after the infection. To verify the infection...
-
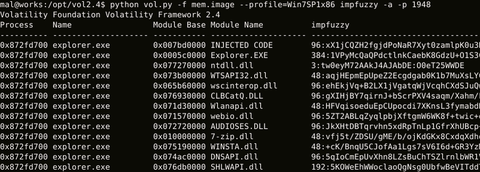
Hi again, this is Shusei Tomonaga from the Analysis Center. Today I will introduce a tool “impfuzzy for Volatility”, which JPCERT/CC has created for extracting known malware from memory images and utilises for analysis operations. Malware Detection in Memory Forensics To judge if a file type malware sample is a known kind, the easiest and fastest way is to check the hash value (e.g. MD5 or SHA 256) of the...
-
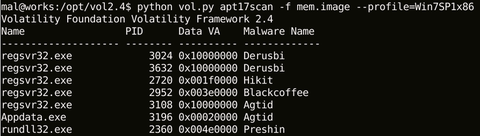
Hello again – this is Shusei Tomonaga from Analysis Center. This blog entry is to introduce “apt17scan.py” created by JPCERT/CC to detect certain malware used in targeted attacks, and to extract its configuration information. It is a plugin for the Volatility Framework (hereinafter “Volatility”), a memory forensics tool. My colleague Yuu Nakamura and I had the honour to introduce this at CODE BLUE 2015, an international conference for information security...