MalConfScan with Cuckoo: Plugin to Automatically Extract Malware Configuration
In malware analysis, extracting the configuration is an important step. Malware configuration contains various types of information which provides a lot of clues in incident handling, for example communication details with other hosts and techniques to perpetuates itself. This time, we will introduce a plugin “MalConfScan with Cuckoo” that automatically extracts malware configuration using MalConfScan (See the previous article) and Cuckoo Sandbox (hereafter “Cuckoo”).
This plugin is available on GitHub. Feel free to download from the webpage below:
JPCERTCC/MalConfScan - GitHub
https://github.com/JPCERTCC/MalConfScan-with-Cuckoo
About MalConfScan with Cuckoo
"MalConfScan with Cuckoo" is a plugin for Cuckoo, which is an open source sandbox system for dynamic malware analysis. By adding this plugin to Cuckoo, MalConfScan runs on Cuckoo, enabling automatic extraction of malware configuration . Figure 1 shows Cuckoo’s behaviour where "MalConfScan with Cuckoo" is installed.
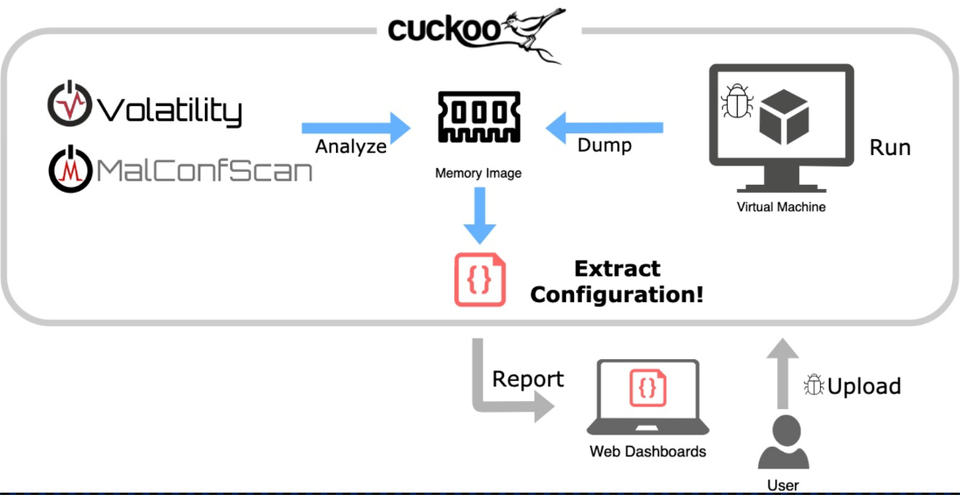
"MalConfScan with Cuckoo" runs malware on the host machine to extract configuration. When malware is registered on Cuckoo and executed on the host machine, a memory image will be dumped, from which MalConfScan extracts configuration of known malware. Extracted configuration will then be shown in a report. Please see the previous article or the following page for the list of malware that this tool supports.
JPCERTCC/MalConfScan - GitHub
https://github.com/JPCERTCC/MalConfScan/
Instruction and report example
First, upload malware on Cuckoo that has "MalConfScan with Cuckoo" installed by using Web GUI or commands. An official document from Cuckoo [1] provides details about the upload procedures. When the upload and analysis is completed, a report will be provided as in Figure 2.
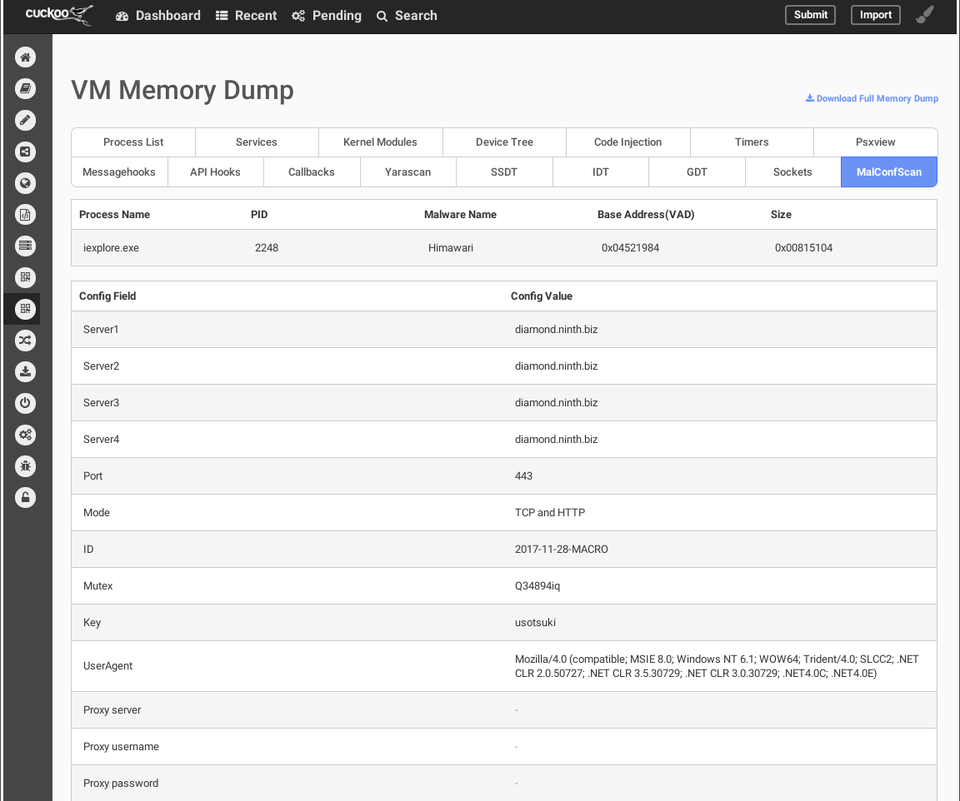
Figure 2 shows the configuration of malware Himawari, a variant of RedLeaves which is used in targeted attacks. It is a kind of bot, and the configuration contains C&C server, destination port, protocol, encryption key etc. In this way, "MalConfScan with Cuckoo" can easily extract configuration for known malware.
Additionally, the results can also be obtained in JSON format. report.json records the following data:
"malconfscan": {
"data": [
{
"malconf": [
[
{"Server1": "diamond.ninth.biz"},
{"Server2": "diamond.ninth.biz"},
{"Server3": "diamond.ninth.biz"},
{"Server4": "diamond.ninth.biz"},
{"Port": "443"},
{"Mode": "TCP and HTTP"},
{"ID": "2017-11-28-MACRO"},
{"Mutex": "Q34894iq"},
{"Key": "usotsuki"},
{"UserAgent": "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E)"},
{"Proxy server": ""},
{"Proxy username": ""},
{"Proxy password": ""}
]
],
"vad_base_addr": "0x04521984",
"process_name": "iexplore.exe",
"process_id": "2248",
"malware_name": "Himawari",
"size": "0x00815104"
}
],
},
How to install
The following steps are required before installing "MalConfScan with Cuckoo":
- Install MalConfScan
- Apply patches for Cuckoo
- Change configuration of Cuckoo
For more information about how to install the tool, please see our wiki on the GitHub:
MalConfScan-with-Cuckoo Wiki - GitHub
https://github.com/JPCERTCC/MalConfScan-with-Cuckoo/wiki
- Ubuntu 18.04
- Python 2.7.16
- Cuckoo 2.0.6
- Volatility 2.6
A blog article by @soji256 explains procedures to install "MalConfScan with Cuckoo", which can be a good reference.
Installing the MalConfScan with Cuckoo to Analyze Emotet - Medium
https://medium.com/@soji256/build-a-malconfscan-with-cuckoo-environment-to-analyze-emotet-ff0c4c589afe
In closing
This plugin enables extracting configuration of known malware from sandbox. Even in case where malware has anti-VM or anti-sandbox function, we can still extract the configuration by spoofing some environmental information.
We will present the details of “MalConfScan” and “MalConfScan with Cuckoo” at the coming Black Hat USA 2019 Arsenal [3]. Feel free to stop by if you are attending Blackhat USA 2019, and we look forward to having active discussion and feedback from analysts.
Tomoaki Tani
(Translated by Yukako Uchida)
[1] Cuckoo Docs - Submit an Analysis
https://cuckoo.sh/docs/usage/submit.html
[2] “Abnormal Encryption of Himawari” - Japan Security Analyst Conference [Japanese]
https://www.jpcert.or.jp/present/2018/JSAC2018_01_nakatsuru.pdf
[3] MalConfScan with Cuckoo: Automatic Malware Configuration Data Extraction and Memory Forensic - Black Hat USA 2019
https://www.blackhat.com/us-19/arsenal/schedule/index.html#malconfscan-with-cuckoo-automatic-malware-configuration-data-extraction-and-memory-forensic-16914

