Extract Malware Configuration with MalConfScan
Every day, new types of malware are discovered. However, many of them are actually variants of existing malware - they share most part of the code and there is a slight difference in configuration such as C&C servers. This indicates that malware analysis is almost complete as long as the configuration is extracted from malware.
In this article, we would like to introduce details of “MalConfScan”, a tool to extract malware configuration, developed by JPCERT/CC. This tool is available on GitHub. Feel free to download from the webpage below:
JPCERTCC/MalConfScan - GitHub
https://github.com/JPCERTCC/MalConfScan
Read the Wiki to learn how to install the tool:
MalConfScan wiki - GitHub
https://github.com/JPCERTCC/MalConfScan/wiki
About MalConfScan
MalConfScan is a plugin for The Volatility Framework (hereafter “Volatility”), a memory forensic tool. In most cases, malware analysis begins with unpacking the malware to extract configuration. MalConfScan extracts configuration from unpacked executable files loaded on the memory.
MalConfScan can perform the following functions:
- malconfscan: Extract configuration of known malware from a memory image
- malstrscan: Detect suspicious processes from a memory image and list the string that it refers to
malconfscan
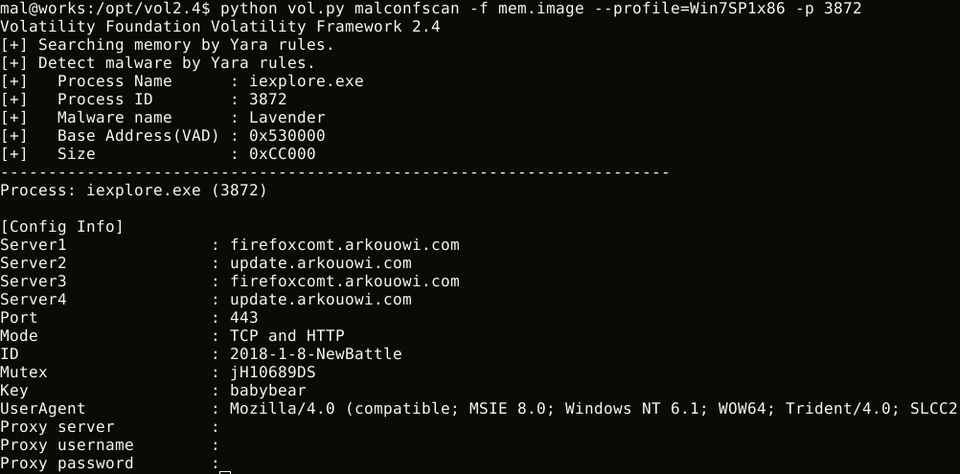
Figure 1 is an example of malconfscan execution. First, a malware-injected process name (Name), the process ID (PID) and the name of the detected malware (Malware Name) are displayed. Malware configuration (Config info) is also displayed.
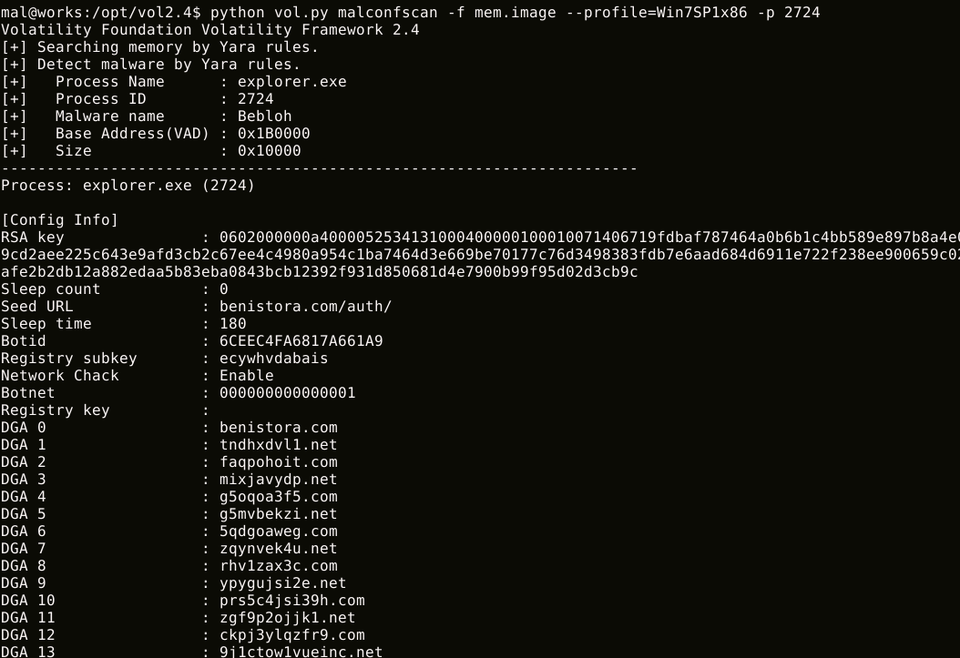
malconfscan also decodes encoded strings and displays DGA domains. Figure 2 is the result where malconfscan detected Bebloh. DGA domains are listed following the configuration.
As of 30 July 2019, malconfscan is compatible with 25 types of malware. See Appendix for supported malware.
malstrscan
malstrscan detects Process Hollowing on the memory and lists the strings that the process refers to. Although malware configuration is usually encoded, malware decodes it when referring to the information, and this is sometimes left on the memory. This function can pick up such remaining configuration. Figure 3 is an example of malstrscan execution.
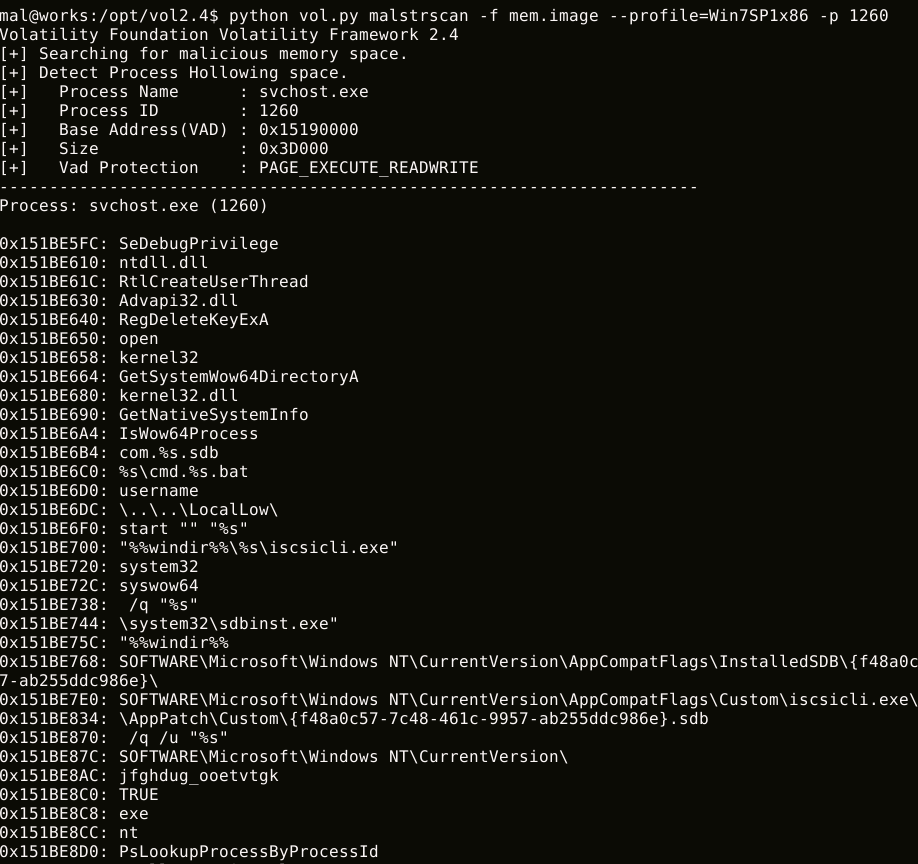
malstrscan lists strings only from the memory space where the PE file is loaded. With ‘-a’ option, it can also list strings in heap and parent memory space.
In closing
malconfscan can be used for malware analysis and memory forensics. We hope that this tool helps incident investigation. We plan to update this tool in the future to make it compatible with many other types of malware.
In the next article, we will install this tool in Cuckoo Sandbox to automatically extract malware configuration.
Shusei Tomonaga
(Translated by Yukako Uchida)
Appendix A Malware Compatible with MalConfScan
| Malware | |
| Ursnif | HawkEye Keylogger |
| Emotet | Lokibot |
| Smoke Loader | Bebloh |
| Poison Ivy | AZORult |
| CobaltStrike | NanoCore RAT |
| NetWire | AgentTesla |
| PlugX | FormBook |
| RedLeaves | NodeRAT |
| TSCookie | njRAT |
| TSC_Loader | TrickBot |
| xxmm | Remcos |
| Datper | QuasarRAT |
| Ramnit | |

