SysmonSearch is a tool developed by JPCERT/CC to analyse event logs generated on Sysmon (a Microsoft tool). https://github.com/JPCERTCC/SysmonSearch SysmonSearch is now compatible with Elastic Stack 7.x. Please note that the new version no longer supports Elastic Stack 6.x versions. This article introduces the new version of SysmonSearch, changes from the previous versions and new functions. Elastic Stack updates Kibana There was a change in Kibana plug-in due to the updates...
List of “SysmonSearch”
-
-
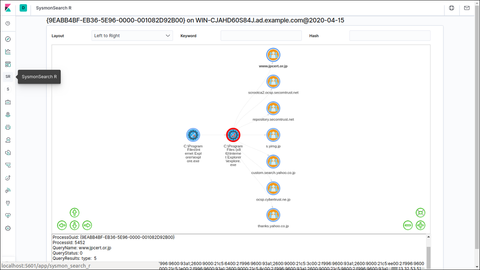
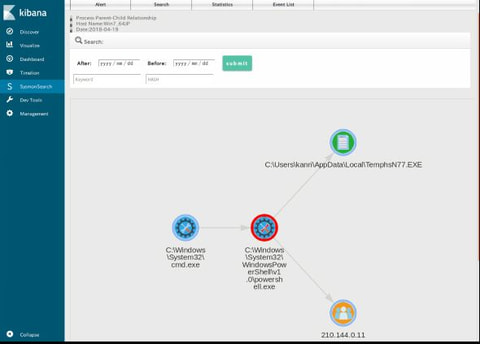
In a past article in September 2018, we introduced a Sysmon log analysis tool "SysmonSearch" and its functions. Today, we will demonstrate how this tool can be used for incident investigation by showing some examples. To install SysmonSearch, please see the following page: JPCERTCC GitHub · SysmonSearch Wiki https://github.com/JPCERTCC/SysmonSearch/wiki The case study was conducted in the following environment: Sysmon 7.0.1 ElasticSearch 6.2.2 Kibana 6.2.2 Winlogbeat 6.2.2 Browser: Firefox Example of...
-
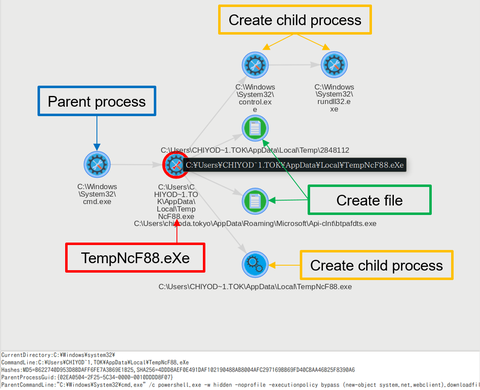
In recent sophisticated cyber attacks, it is common to observe lateral movement, where a malware- infected device is used as a stepping stone and further compromise other devices in the network. In order to investigate the compromised devices, it is necessary to retain detailed logs of the applications that run on the device on a daily basis. One of the well-known tools for this purpose is Sysmon [1] from Microsoft,...