A New Tool to Detect Known Malware from Memory Images – impfuzzy for Volatility –
Hi again, this is Shusei Tomonaga from the Analysis Center. Today I will introduce a tool “impfuzzy for Volatility”, which JPCERT/CC has created for extracting known malware from memory images and utilises for analysis operations.
Malware Detection in Memory Forensics
To judge if a file type malware sample is a known kind, the easiest and fastest way is to check the hash value (e.g. MD5 or SHA 256) of the entire file to see if it matches any of those in malware databases. However, this method is not applicable for memory forensics. This is because executable files loaded on the memory are partially altered by the OS or the malware itself (for example, when an executable file is loaded on the memory, IAT – import address table – is replaced with the API’s address loaded on the memory), and therefore hash values of the file before and after being loaded on the memory do not match.
In this sense, for memory forensics, signature matching using Yara scan is often used for detecting known malware. In order to use this method, however, details of the malware need to be analysed and also its signature needs to be generated beforehand.
Overview and Main Features of impfuzzy for Volatility
“impfuzzy for Volatility” is a tool that solves such issues and enables extracting known malware from memory images. This tool is implemented as a plugin for The Volatility Framework (hereafter “Volatility”), a memory forensics tool. To enable detection even after information in the malware executable file is partially altered when loaded on the memory, the tool uses “impfuzzy” method which compares the similarities of Windows executable files based on hash values generated from Import API. impfuzzy was introduced in a past article on this blog.
impfuzzy for Volatility offers the following functions and is applicable for investigations using imphash [1] as well.
- impfuzzy – Compares and displays hash values of executable files in memory images using impfuzzy
- imphashlist – Displays the imphash value of executable files in memory images
- imphashsearch – Compares hash values of executable files in memory images using imphash
When executing the following command line, impfuzzy hash values of the executable files and DLL files loaded on the memory will be listed as in Figure 1.
$ python vol.py -f [memory.image] --profile=[profile] impfuzzy -a (-p [PID])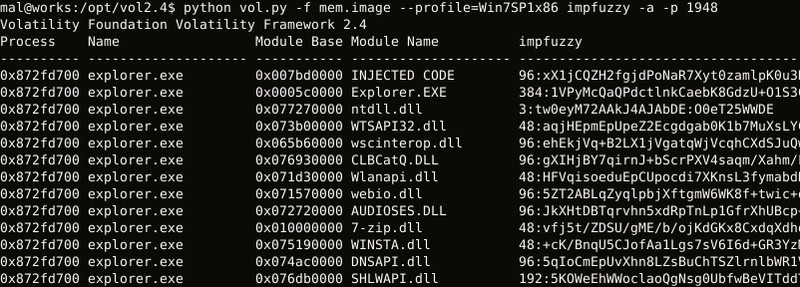 |
To search memory images for files which are similar to certain executable files, the following command line can be executed.
$ python vol.py -f [memory.image] --profile=[profile] impfuzzy -e [PE File or Folder] (-p [PID])
The executable file to compare with or the folder where it is stored can be specified as option “-e”.
By executing the above command line, similar executable files can be detected as in Figure 2 (The “Compare” field indicates the similarity by percentage).
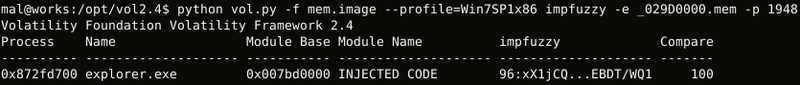 |
Figure 2 demonstrates the example where Citadel, a type of banking malware, is detected. Citadel is usually packed and starts running by injecting unpacked code into Explorer, etc. impfuzzy for Volatility compares executable files loaded on the memory, which makes it possible to calculate hash values of unpacked samples. Therefore, similarities can be judged even for packed malware.
impfuzzy for Volatility can also detect code that is injected into processes, as well as executable files and loaded DLL files. In Figure 2, “INJECTED CODE” in the “Module Name” field indicates that there is code injected into the processes.
The following shows other options that are available in impfuzzy for Volatility.
(Example 1) Compares impfuzzy hash values listed in the file with executable files in the memory, and displays the results:
$ python vol.py -f [memory.image] --profile=[profile] impfuzzy -i [Hash List File] (-p [PID])
(Example 2) Lists imphash values of executable files loaded on the memory
$ python vol.py -f [memory.image] --profile=[profile] imphashlist (-p [PID])
(Example 3) Compares imphash values listed in the file with executable files in the memory, and displays the results that match
$ python vol.py -f [memory.image] --profile=[profile] imphashsearch -i [Hash List] (-p [PID])
Advantages of Using impfuzzy in Memory Forensics
Even though executable files loaded on the memory are partially altered as previously discussed, their Import API remain the same. impfuzzy judges the similarity based on hash values derived from Import API of the executable files. This makes it possible to identify the same file even from executable files loaded on the memory.
Furthermore, since impfuzzy can generate hash values automatically, unlike Yara scan, there is no need to generate signatures manually.
Obtaining and Installing impfuzzy for Volatility
This tool is available on GitHub, a shared web service for software development projects. Feel free to download from the following website for your use:
JPCERTCC/aa-tools GitHub - impfuzzy for Volatility
https://github.com/JPCERTCC/impfuzzy/tree/master/impfuzzy_for_Volatility/
In order to use this tool, the following Python module needs to be installed.
- pyimpfuzzy
Please see the following website regarding installation of pyimpfuzzy.
When executing, impfuzzy.py needs to be installed from the aforementioned website, stored in the “contrib/plugins” folder in Volatility and then executed. (It is also possible to specify the folder where impfuzzy.py is stored using option “--plugins”.)
Summary
Memory may contain some information including malware that is not left on the hard disk, and therefore memory forensics is important in incident investigations involving malware infection. We hope that this tool is utilised as to effectively conduct investigations on memory forensics in such security incidents.
Thanks for reading.
- Shusei Tomonaga
(Translated by Yukako Uchida)
Reference:
[1] FireEye - Tracking Malware with Import Hashing
https://www.fireeye.com/blog/threat-research/2014/01/tracking-malware-import-hashing.html

