Evidence of Attackers’ Development Environment Left in Shortcut Files
A shortcut file, also referred to as a shell link, is a system to launch applications or to allow linking among applications such as OLE. As we introduced in a previous blog post “Asruex: Malware Infecting through Shortcut Files”, shortcut flies are often used as a means to spread malware infection. Generally, shortcut files contain various types of information including the dates and environment that the shortcut file was created. This also applies to shortcut files created by attackers. By extracting and correlating information recorded in the shortcut files used in attacks, it is possible to identify the shortcut files that may have been created by the same attacker.
This blog entry explains how to classify an attack subject through information recorded in the shortcut files used in attacks. Furthermore, the article will also introduce trends in the system environments used by the latest attackers, which JPCERT/CC learned through statistical analysis of information gained from a number of shortcut files used in attacks.
Information Contained in Shortcut Files
Among the various types of information recorded in shortcut files, the following is the list of items that JPCERT/CC focused on for the purpose of this analysis (For the shortcut file format, please refer to the information released by Microsoft [1]).
- Code page number: Number describing the character encoding configured in the OS where the shortcut file was created
- Volume serial number: Volume serial number of the drive where the shortcut file was located at the time of creation
- NetBIOS name: Computer name of the machine where the shortcut file was created
- MAC address: MAC address of the machine’s network adapter where the shortcut file was created
(Part of the DroidBirth field (GUID value) may contain the MAC address [2]. If neither network nor adapter exists, this will be a random value instead of a MAC address).
JPCERT/CC has confirmed that these types of information are being left in many of the shortcut files used in actual attacks. If these are available, it is possible to presume the system environment that the attackers use.
The following section explains the results of the study and classification of 83 shortcut files that JPCERT/CC collected from actual attack cases.
Classification of Shortcut Files Used in Actual Attacks
Among the above-listed information that shortcut files contain, the following 3 are useful in terms of identifying the system environment used when the shortcut file was created.
- Volume serial number
- NetBIOS name
- MAC address
Shortcut files that have the same information in the above items are likely to be created by the same attacker. The image below illustrates the similarity of the shortcut files in terms of the 3 types of information. The nodes show either a shortcut file, MAC address, NetBIOS name or volume serial number, and represented in different colours – for example gray for shortcut file. For the above 3 types of information, the values are connected to the corresponding nodes with a line if the respective values are contained in the shortcut file.
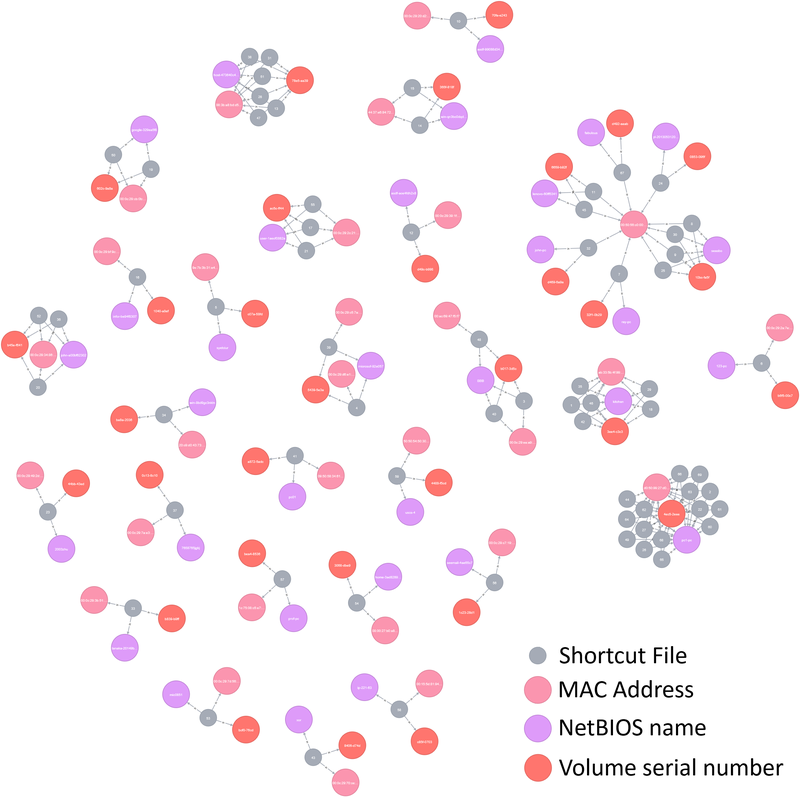 |
Shortcut files used in attacks may contain the same volume serial number, NetBIOS name and MAC address and form a cluster. For example, the shortcut files which infect Asruex (obtained by JPCERT/CC) contained the following information:
- Volume serial number: 4ec5-2eee
- NetBIOS name: pc1-pc
- MAC address: d0:50:99:27:d0:fc
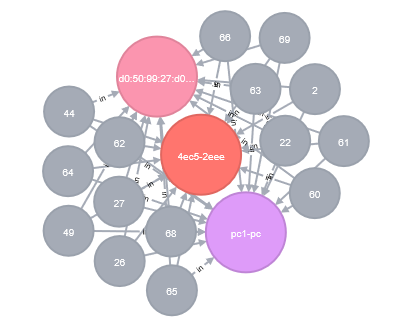 |
In this way, multiple shortcut files may be correlated by comparing volume serial number, NetBIOS name and MAC address in the shortcut file. The coming section demonstrates the environments that attackers used for creating shortcut files, which can be seen from the analysis of shortcut file information.
Attackers’ Environment Identified from Shortcut Files
The first 3 bytes of MAC address are allocated for the Organizationally Unique Identifier (OUI), which shows the vendor of the product. Vendor names that can be identified from the 3 bytes of the MAC address in the shortcut files used in attacks are listed in Table 1.
| First 3 bytes of MAC address | Vendor Name | Number |
|---|---|---|
| 00-0c-29 | VMware, Inc. | 22 |
| d0-50-99 | ASRock Incorporation | 15 |
| 00-50-56 | VMware, Inc. | 10 |
| 44-37-e6 | Hon Hai Precision Ind.Co.Ltd | 2 |
| 00-15-5d | Microsoft Corporation (Hyper-V) | 1 |
| 08-00-27 | CADMUS COMPUTER SYSTEMS (VirtualBox) | 1 |
| 1c-75-08 | COMPAL INFORMATION (KUNSHAN) CO., LTD. | 1 |
| 20-c9-d0 | Apple Inc. | 1 |
It is clear that attackers tend to use a virtual environment for creating files. Many malware analysts use a virtual environment for analysis so that the actual environment does not get infected with malware. For the same reason, malware creators seem to use a virtual environment as well.
We also searched for code page information of shortcut files used in attacks and identified that the information remained in 22 of the artifacts. All of them had the same code page 936, which indicates simplified Chinese language.
For other noteworthy results taken from information left in the shortcut files, please see Appendix A.
Summary
Information on attackers’ system environment remains in many shortcut files used in attacks. By utilising the information, classification of the attack subject can be easily conducted. When analysing shortcut files used in attacks, there may be new findings by focusing not only on malicious scripts that attackers intentionally created, but also on evidence that they left unintentionally in the shortcut files.
Thank you for reading – see you soon.
- Shusei Tomonaga
(Translated by Yukako Uchida)
References:
[1] Microsoft - [MS-SHLLINK]: Shell Link (.LNK) Binary File Format
https://msdn.microsoft.com/en-us/library/dd871305.aspx
[2] IETF - RFC 4122 - A Universally Unique IDentifier (UUID) URN Namespace
https://tools.ietf.org/html/rfc4122.html
Appendix A: List of information contained in shortcut files used in attacks
| NetBIOS name | Numbers |
|---|---|
| pc1-pc | 15 |
| host-473640c404 | 8 |
| kitchen | 8 |
| lenovo-60ff5341 | 4 |
| seasbo | 4 |
| john-a00bf62302 | 3 |
| user-1aecf0882a | 3 |
| google-329ea5f8 | 2 |
| microsof-92e057 | 2 |
| win-qn3bc0dqd7e | 2 |
| Volume serial number | Numbers |
|---|---|
| 4ec5-2eee | 15 |
| 3ee4-c3c3 | 8 |
| 78e5-aa39 | 8 |
| 602c-9a8a | 7 |
| 10bc-fa5f | 4 |
| 6659-b92f | 4 |
| b017-3d5c | 4 |
| ac5c-ff44 | 3 |
| b45e-f641 | 3 |
| 365f-818f | 2 |
| MAC address | Numbers |
|---|---|
| d0:50:99:27:d0:fc | 15 |
| 00:50:56:c0:00:08 | 11 |
| 88:3b:a8:bd:d5:37 | 8 |
| ab:33:5b:4f:99:a0 | 8 |
| 00:0c:29:2c:21:be | 3 |
| 00:0c:29:34:86:a9 | 3 |
| 00:0c:29:ea:a9:9c | 3 |
| 00:0c:29:cb:0b:aa | 2 |
| 44:37:e6:84:72:77 | 2 |
| 00:0c:29:20:d2:d9 | 1 |

