YAMAGoya: A Real-time Client Monitoring Tool Using Sigma and YARA Rules
In recent years, fileless malware and obfuscation techniques have made it increasingly difficult to detect suspicious activity by scanning files alone. To counter these threats, security researchers and malware analysts actively create and publish detection rules such as Sigma and YARA.
However, many existing endpoint security tools rely on unique detection engines, instead of directly using Sigma or YARA. To address this problem, JPCERT/CC released the open-source threat hunting tool YAMAGoya. The tool is available at the following GitHub repository, and feel free to use it.
GitHub JPCERTCC/YAMAGoya: https://github.com/JPCERTCC/YAMAGoya
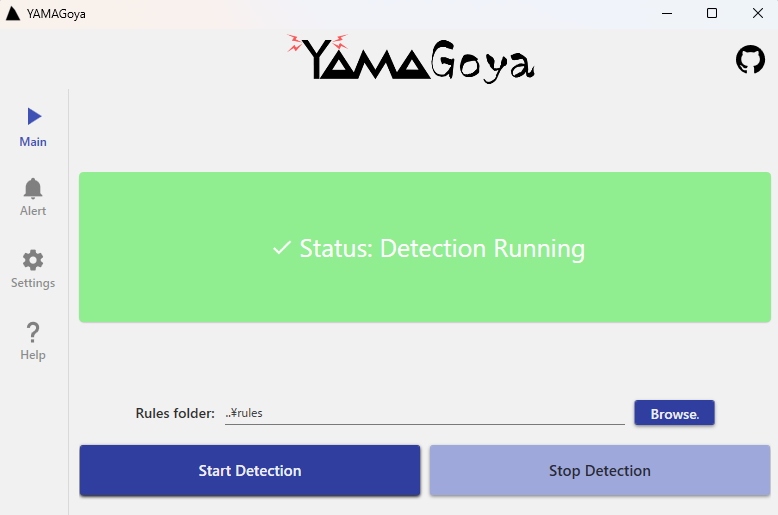
This blog article introduces YAMAGoya's concept and how to use it.
Concept of YAMAGoya
YAMAGoya is designed to detect threats by combining ETW (Event Tracing for Windows) event monitoring with memory scanning. The main features of this tool are:
- Userland-only operation: No kernel driver required, making implementation easy.
- Real-time monitoring: Monitor files, processes, registry, DNS, network, PowerShell, WMI, etc. in real time via ETW.
- Supports multiple rule formats: Supports Sigma and original YAML rules that can be used for correlation analysis.
- Memory scanning: Detect fileless or packed malware using YARA rules.
- GUI / CLI support: Can be used from the GUI or automated from the command line.
Installation
Get binaries
If you want to evaluate the tool immediately, you can download binaries from the GitHub repository's Releases page.
Build
If you want to build it from source, please refer to the README.
How to use
YAMAGoya can be used via GUI and CLI. Start from command-line without options or double-click to launch the GUI.
# Execute GUI > YAMAGoya.exe
This tool must be executed with administrative privileges (to start an ETW session). When launching the tool, choose “Run as administrator” from the right-click menu or start a command prompt with administrative privileges.
From the command line, you can run it as follows. See the helpoption for additional options.
# Monitor with Sigma rules > YAMAGoya.exe --session --sigma "C:\Rules\Sigma" --all
# Memory scan with YARA rules > YAMAGoya.exe --session --yara "C:\Rules\YARA" --all
Supported rules in YAMAGoya
Since YAMAGoya supports Sigma and YARA rules, please make use of publicly available rules. For Sigma rules, the supported categories are limited to those targeting Windows OS. For details, see README:
In addition to Sigma and YARA rules, the tool supports original YAML rules. The following section explains how to write custom YAML rules.
How to write custom YAML rules
To create a custom YAML rule, follow the schema below. Each rule file must include the following:
- rulename: A unique name for the rule - description: A description of what the rule detects - rules: A list of rule items. Each item must include: - ruletype: The type of rule (e.g., regex, binary) - target: The event category to match - rule: The pattern or value to match (For regex rules, a valid regular expression)
You can use the following event categories for target(Table 1).
| Target name | Description |
| file | File creation events |
| delfile | File deletion events |
| process | Process events |
| open | OpenProcess |
| load | DLL load events |
| registry | Registry events |
| dns | DNS events |
| ipv4 | IPv4 network events |
| ipv6 | IPv6 network events |
| shell | Shell-related events (RunKey, shortcuts) |
| powershell | PowerShell execution events |
| wmi | WMI command execution events |
By default, an alert is raised if all rules listed in a single file are observed within 10 seconds. For example, you can create a rule that detects malware when a file is created, a process is executed, a DLL is loaded, and network communication occurs. In this way, custom YAML rules are effective for detection by correlating multiple activities.
rulename: "ANEL"
description: "Detects ANEL from maldoc type"
rules:
- ruletype: "regex"
target: "file"
rule: "Tmp\\.docx$"
- ruletype: "regex"
target: "process"
rule: "ScnCfg32\\.Exe$"
- ruletype: "regex"
target: "dll"
rule: "vsodscpl\\.dll$"
- ruletype: "regex"
target: "file"
rule: "TCDolW0p\\.log$"
- ruletype: "ipv4"
target: "ipv4"
rule: "45.32.116.146"
Checking logs
When using the GUI, you can view logs in the Alert tab. From Open Log File in Alert tab, you can also check the text log (Figure 2).
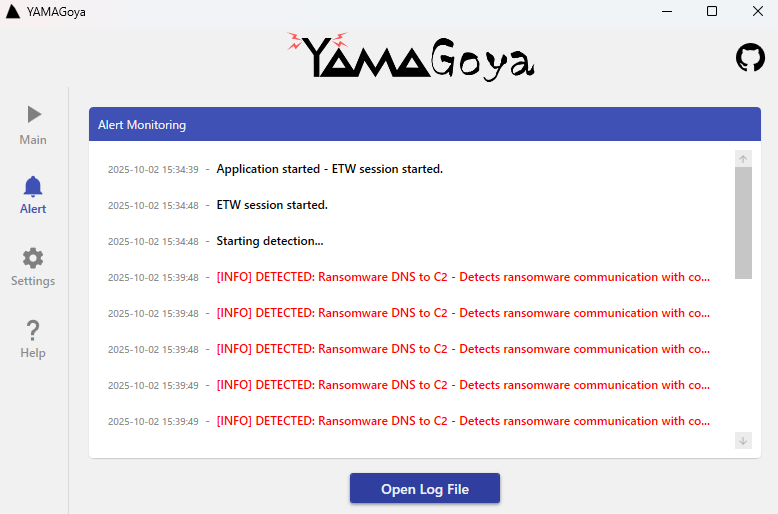
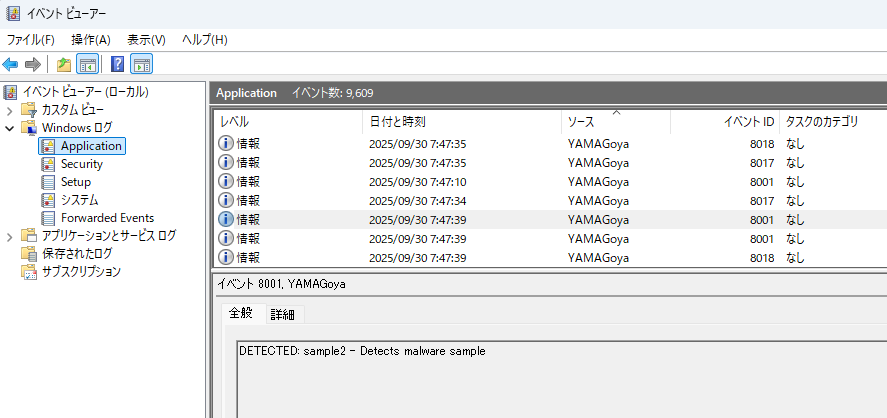
Alerts are also stored in the Event Log (Application). Table 2 lists the event IDs that YAMAGoya records.
| Event ID | Main trigger condition |
| 8001 | Detection by a custom YAML rule |
| 8002 | Partial match with a custom YAML rule (debug message) |
| 8003 | Termination of a process detected by a custom YAML rule (when Kill mode is active) |
| 8005 | WinRM outbound communication |
| 8006 | WinRM inbound communication |
| 8008 | Security Mitigations event detection |
| 8009 | Security Adminless event detection |
| 8011 | Security CVE event detection |
| 8012 | SMB server authentication detection |
| 8013 | SMB server file share detection |
| 8014 | SMB server file share addition detection |
| 8015 | SMB client connection failure |
| 8016 | SMB client file transfer |
| 8017 | ETW session start |
| 8018 | ETW session stop |
| 9001 | Detection by a Sigma rule |
| 9002 | Termination of a process detected by a Sigma rule (when Kill mode is active) |
In closing
Because YAMAGoya can use publicly available signatures such as Sigma and YARA, it enables security teams to use the community’s knowledge for security measures. Please use the tool for threat hunting and incident response. We welcome Pull Request and any other requests for features.
Shusei Tomonaga
(Translated by Takumi Nakano)
FAQ
Q1. Can YAMAGoya replace traditional antivirus software?
A. No. YAMAGoya is not a replacement for antivirus software but a complementary tool. Since the tool has no default detection rule, you first need to collect or create detection rules.
Q2. Can I run YAMAGoya in the background?
A. Yes. It can reside in the system tray and monitor in the background. When it detects something based on your configured rules, it will notify you and output logs.
Q3. Can I integrate YAMAGoya with existing SIEMs?
A. Yes. YAMAGoya outputs logs as text and to the Event Log (Application). You can import those outputs to SIEMs such as Splunk using log collection agents or forwarding functions.
Q4. Are there limitations for countermeasures against ETW bypass (evasion technique)?
A. Yes. At present, there is no dedicated measure for ETW bypass. Advanced attackers may disable or compromise ETW to evade detection. We recommend using YAMAGoya together with EDR and other monitoring tools to implement a layered defense.

