Update on Attacks by Threat Group APT-C-60
In JPCERT/CC Eyes, we previously reported on attacks conducted by Attack Exploiting Legitimate Service by APT-C-60. JPCERT/CC continues to observe similar attack activities in Japan. This report provides an update on the attacks confirmed between June and August 2025, focusing on developments since our last article. The following topics are covered:
- Attack flow
- Updates to the downloader and SpyGlace
- SpyGlace encoding functions and communication methods
- Decoy documents used in the attacks
- Analysis of the GitHub repository
Attack Flow
The attacks confirmed by JPCERT/CC were targeted spear-phishing emails sent to recruitment staff, in which the attackers impersonated job seekers. This pattern is closely similar to attacks that occurred around August 2024. Figure 1 shows the flow of the attack. In the previous attacks, victims were directed to download a VHDX file from Google Drive. However, in the latest attacks, the malicious VHDX file was directly attached to the email. When the recipient clicks the LNK file contained within the VHDX, a malicious script is executed via Git, which is a legitimate file.
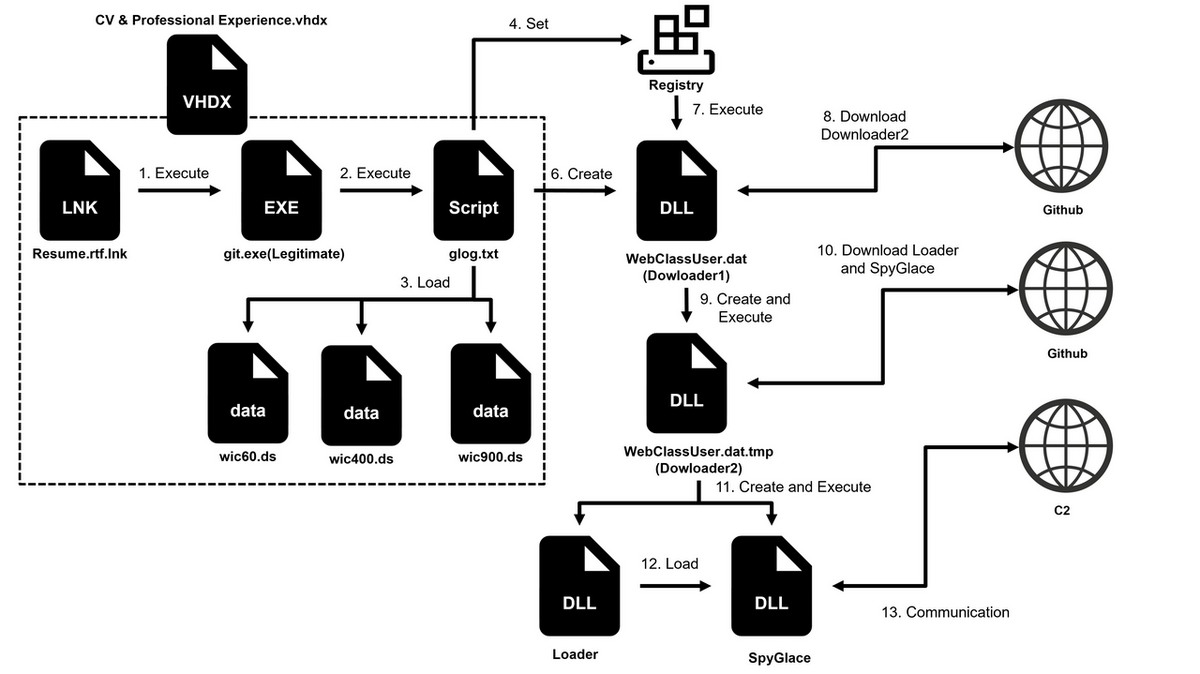
The LNK file executes gcmd.exe (a legitimate Git file), and it runs the script glog.txt stored in the VHDX file.
P:\LICENSES.LOG\mingw64\bin\gcmd.exe "cd .\LICENSES.LOG\mingw64\bin && type glog.txt | gcmd.exe" && exit
The script executed by Git is responsible for displaying a decoy document, creating files, and executing those files. The created WebClassUser.dat (hereafter referred to as “Downloader1”) is registered in the registry as shown below, and then it gets persisted and executed through COM hijacking.
HKCU\Software\Classes\CLSID\{566296fe-e0e8-475f-ba9c-a31ad31620b1}\InProcServer32
Updates to Downloader1 and Downloader2
For attackers to identify compromised devices, Downloader1 periodically communicates with a legitimate statistics service called statcounter. The request headers are created in the following format. Compared to earlier versions, the current one is different in that it identifies compromised machines by their volume serial number and computer name.
Referer: ONLINE=>[Number1],[Number2] >> [%userprofile%] / [VolumeSerialNumber + ComputerName]
Downloader1 combines a filename derived from the volume serial number and the computer name with a URL embedded in the malware sample to generate a path in the following format, and it is used for communication.
https://raw.githubusercontent.com/carolab989/class2025/refs/heads/main/[VolumeSerialNumber + ComputerName].txt
The attackers check the referrer value sent to statcounter and then upload a file named "[VolumeSerialNumber + ComputerName].txt" corresponding to the infected device to GitHub. DownLoader1 then retrieves that file from GitHub. Based on the URL in the retrieved file, DownLoader2 is downloaded and executed. In addition to specifying the download URL, the "[VolumeSerialNumber + ComputerName].txt" can execute the following commands in Table 1. For example, the command "1*" can change the interval at which a GET request is sent to statcounter.com from the default of one hour to six hours. Such capability indicates the attackers’ intent to monitor the victim environment more cautiously.
| Command | Contents |
|---|---|
| "1*" | Change the interval settings |
| "0" or "40" | Reset the interval settings |
| "http*" | Download DLL |
Like earlier versions, the retrieved files are XOR-decoded and then executed using "sgznqhtgnghvmzxponum" as the key. Downloader2 can download and execute SpyGlace and its loader. The malware’s dynamic API resolution uses an encoding scheme based on ADD and XOR. The value has changed from earlier versions, and now XOR 0x05 is performed after add 0x04. The SpyGlace loader uses the same encoding scheme. As in earlier versions, files retrieved by Downloader2 are XOR-decoded with the key "AadDDRTaSPtyAG57er#$ad!lDKTOPLTEL78pE" and then executed by COM hijacking.
Updates to SpyGlace
JPCERT/CC has observed three versions of SpyGlace: 3.1.12, 3.1.13, and 3.1.14. Compared with Version 3.1.6, which was observed by JPCERT/CC in 2024, the previously implemented commands prockill and proclist have been modified to perform no action. JPCERT/CC also confirmed a new command, uld, has been added. The command calls a specific function of a loaded module and then unloads the module two seconds after that. This is possibly intended for modules that must execute a specific function before being unloaded. Additionally, in the screenupload command, the file path and the export function name for what appears to be a screenshot-related module have been changed to those shown below. Since the Clouds.db module itself has not been observed, its functionality is unknown, but it is believed to be related to the screenshot command. For a full list of implemented commands, see Appendix D.
File path: %LocalAppData%\Microsoft\Windows\Clouds\Clouds.db Export Function: mssc1
There are slight differences among the observed versions, 3.1.12, 3.1.13, and 3.1.14. However, JPCERT/CC confirmed that the Mutex value is different between them. From version 3.1.14, the automatic execution path has also changed from %public%\AccountPictures\Default\ to %appdata%\Microsoft\SystemCertificates\My\CPLs. An article published in September 2025 [1] describes a campaign in which version 3.1.14 was used, but this is likely a separate campaign observed overseas because the GitHub repositories and other resources used in the campaign do not overlap with those observed by JPCERT/CC.
Details of SpyGlace’s Encoding Functions and Communication Methods
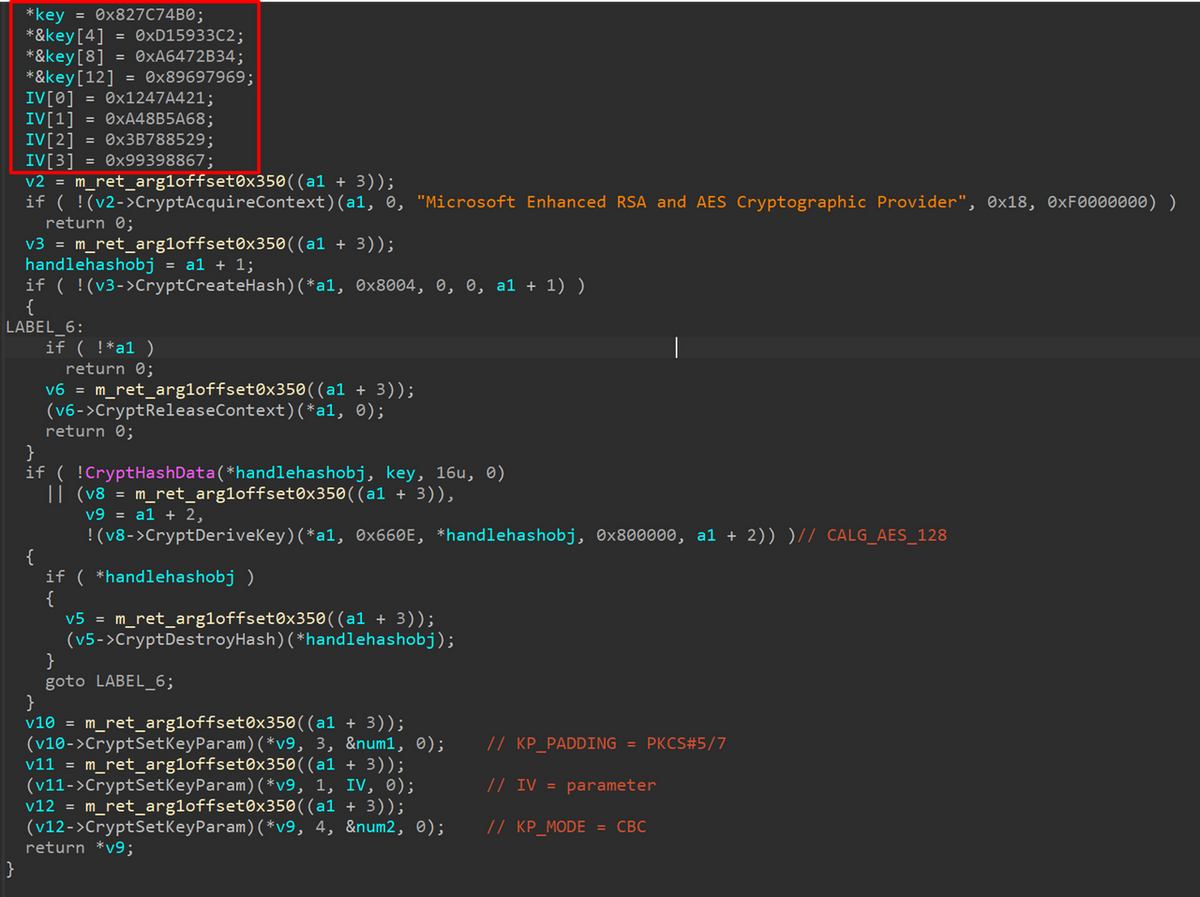
SpyGlace’s characteristic encoding scheme combines a single-byte XOR with a SUB instruction. This is heavily used for strings the malware employs and for resolving dynamic APIs. The "Download" command, one of SpyGlace’s commands, downloads an encrypted file. The file is decrypted using AES-128-CBC with the KEY and IV shown below and is created to the path %temp%\wcts66889.tmp. Figure 2 shows a part of the Download command code.
KEY: B0747C82C23359D1342B47A669796989 IV: 21A44712685A8BA42985783B67883999
SpyGlace communicates with its C2 servers using BASE64 and RC4. The format of the request headers used in the initial communication is shown below. The a001 value contains the userid value "GOLDBAR", and it is the same string reported by Positive Technologies [2] and was also used in attacks observed in Japan last year, suggesting that it may indicate the targeted region or a specific campaign. Regarding encoding scheme, SpyGlace has employed a modified RC4 since at least version 3.1.6.
a001=[md5("GOLDBAR")]&a002=[md5(systeminfo)]&a003=["uid" or "info"]&a004=[BASE64(CustomRC4([ComputerName;UserName;CpuInfo;OS Version;SpyGlace Version]))]
The modified RC4 increases the number of KSA cycles and performs additions to the value that is to be XORed. The variant can be decoded with the following Python script.
import base64
def CustomRC4(key: bytes, data: bytes) -> bytes:
# --- KSA ---
S = list(range(256))
n = 3
for round in range(n):
j = 0
keylen = len(key)
if keylen == 0:
raise ValueError("key must be non-empty")
for i in range(256):
j = (j + S[i] + key[i % keylen]) & 0xFF
S[i], S[j] = S[j], S[i]
# --- PRGA ---
i = j = 0
out = []
for b in data:
i = (i + 1) & 0xFF
j = (j + S[i]) & 0xFF
k = S[(S[i] + j) & 0xFF]
S[i], S[j] = S[j], S[i]
k2 = S[((S[((i >> 3) ^ (0x20 * j)) & 0xFF] + S[((0x20 * i) ^ (j >> 3)) & 0xFF]) ^ 0xAA) & 0xFF] + S[(S[j] + S[i]) & 0xFF]
out.append( (b ^ k ^ k2) & 0xFF )
return bytes(out)
def decode(base64in):
key = b"90b149c69b149c4b99c04d1dc9b940b9"
decoded = CustomRC4(key, base64.b64decode(base64in))
print("Result: ", decoded)
Decoy Document Used
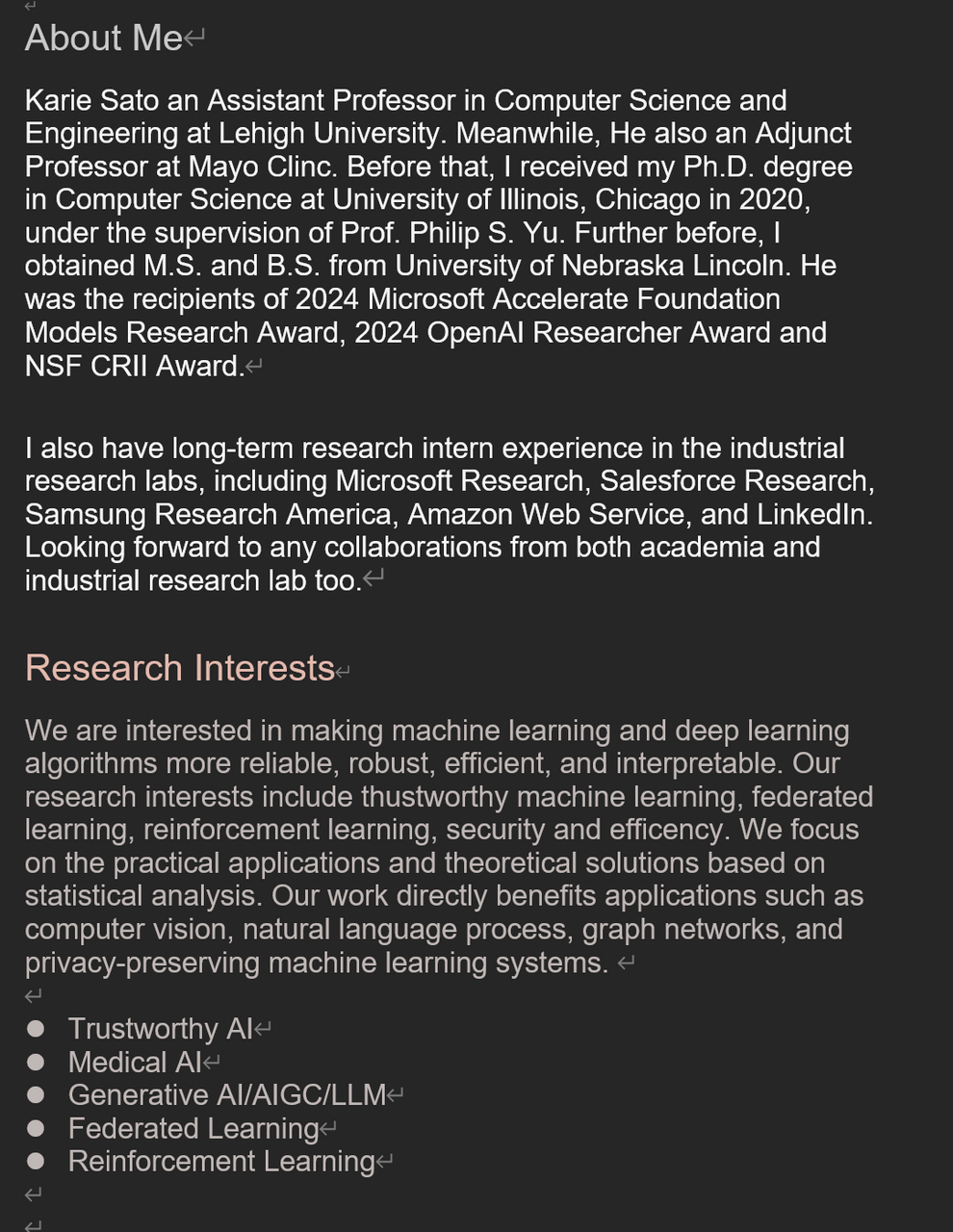
Figure 3 shows a part of the decoy document used in this campaign. Because the attackers targeted recruitment officers, the fabricated resume disguise the writer as a researcher and list multiple academic papers in the CV. However, the authors of those papers do not include the name of the email sender. The name on the resume partially matches the Gmail account name used by the sender, suggesting that the attackers may have created the account specifically for this attack.
Analysis of GitHub Repositories
Because the attackers use GitHub to distribute their payloads, all payloads distributed in the past can be retrieved unless the repository is deleted. Table 2 shows the uploaded SpyGlace versions and the periods during which they were available on GitHub.
| SpyGlace Version | Upload Date & Time |
|---|---|
| Version 3.1.12 | Fri Jun 27 14:33:28 2025 +0900 |
| Version 3.1.13 | Thu Jul 3 18:25:18 2025 +0900 |
| Version 3.1.14 | Wed Jul 16 15:03:52 2025 +0900 |
| Content | Filename | Hash(SHA256) |
|---|---|---|
| Malicious VHDX | CV & Professional Experience.vhdx | f42d0fa77e5101f0f793e055cb963b45b36536b1835b9ea8864b4283b21bb68f |
| Malicious LNK | Resume.rtf.lnk | 25f81709d914a0981716e1afba6b8b5b3163602037d466a02bc1ec97cdc2063b |
| Part of Downloader1 | wic60.ds | ea37dfa94a63689c1195566aab3d626794adaab4d040d473d4dfbd36f1e5f237 |
| Part of Downloader1 | wic400.ds | a80848cf7d42e444b7ec1161c479b1d51167893f47d202b05f590ad24bf47942 |
| Part of Downloader1 | wic900.ds | 1e931c8aa00b7f2b3adedc5260a3b69d1ac914fe1c022db072ed45d7b2dddf6c |
| Dropper Script | glog.txt | c9c6960a5e6f44afda4cc01ff192d84d59c4b31f304d2aeba0ef01ae04ca7df3 |
| Downloader1 | WebClassUser.dat | f102d490ad02b1588b9b76664cd715c315eaab33ac22b5d0812c092676242b15 |
| DownLoader2 | WebCacheR.tmp.dat | 57a77d8d21ef6a3458763293dbe3130dae2615a5de75cbbdf17bc61785ee79da |
| DownLoader2 | WebCacheR.tmp.dat | 9e30df1844300032931e569b256f1a8a906a46c6a7efa960d95142d6bea05941 |
| git.exe(Legitimate) | gcmd.exe | 96312254d33241ce276afc7d7e0c7da648ffe33f3b91b6e4a1810f0086df3dba |
| SpyGlace version 1.3.12 | datautils.txt | 669c268e4e1ced22113e5561a7d414a76fcd247189ed87a8f89fbbd61520966a |
| SpyGlace version 1.3.13 | datautils.txt | f96557e8d714aa9bac8c3f112294bac28ebc81ea52775c4b8604352bbb8986b8 |
| SpyGlace version 1.3.14 | datautils.txt | 8b51939700c65f3cb7ccdc5ef63dba6ca5953ab5d3c255ce3ceb657e7f5bfae8 |
| SpyGlace Loader | datapages.txt | d535837fe4e5302f73b781173346fc9031d60019ea65a0e1e92e20e399a2f387 |
| SpyGlace Loader | datapages.txt | 6d8a935f11665850c45f53dc1a3fc0b4ac9629211bd4281a4ec4343f8fa02004 |
| Downloader2 | coninst3110.dat | d287dc5264fd504b016ec7e424650e2b353946cbf14d3b285ca37d78a6fda6f4 |
| Loader | constart3110.dat | 10278a46b13797269fd79a5f8f0bc14ff1cc5bc0ea87cdd1bbc8670c464a3cf1 |
| Downloader1 | ingredient.txt | 156df8c8bea005bd7dc49eb7aca230ef85ada1c092e45bb3d69913d78c4fa1f9 |
| Loader Scrpt | UsrClass.sct | 7ae86f2cb0bbe344b3102d22ecfcdda889608e103e69ec92932b437674ad5d2f |
| Loader Scrpt | UsrClass.sct | e8b3b14a998ce3640a985b4559c90c31a5d7465bc5be5c6962e487172d3c9094 |
| Loader | intersection.txt | 09fcc1dfe973a4dc91582d7a23265c0fd8fc2a011adb2528887c1e1d3a89075a |
| Downloader | opinsfile.dat | 048b69386410b8b7ddb7835721de0cba5945ee026a9134d425e0ba0662d9aee4 |
| Loader | constafile.dat | f495171e7a10fb0b45d28a5260782a8c1f7080bd1173af405476e8d3b11b21b6 |
| Downloader | coninsfile.dat | 8ea32792c1624a928e60334b715d11262ed2975fe921c5de7f4fac89f8bb2de5 |
| Malicious VHDX | CV & Professional Experience.vhdx | 94ccdaf238a42fcc3af9ed1cae1358c05c04a8fa77011331d75825c8ac16ffd8 |
| Dropper Script | volumelog.txt | 299d792c8d0d38d13af68a2467186b2f47a1834c6f2041666adafc626149edaf |
| Part of Downloader1 | vol60.dot | ea37dfa94a63689c1195566aab3d626794adaab4d040d473d4dfbd36f1e5f237 |
| Part of Downloader1 | vol400.dot | 94f6406a0f40fb8d84ceafaf831f20482700ee1a92f6bca1f769dff98896245c |
| Part of Downloader1 | vol900.dot | 45c1c79064cef01b85f0a62dac368e870e8ac3023bfbb772ec6d226993dc0f87 |
| Downloader1 | UsrClassCache.dat | 50b40556aa7461566661d6a8b9486e5829680951b5df5b7584e0ab58f8a7e92f |
| Malicious LNK | Resume.rtf.lnk | 5da82fa87b0073de56f2b20169fa4d6ea610ed9c079def6990f4878d020c9d95 |
Appendix C: Other IoC
| Content | Value |
|---|---|
| Mutex | K31610KIO9834PG79A90B |
| Mutex | K31610KIO9834PG79AD7B |
| Mutex | K31610KIO9834PG79A44A |
| CLASSID | {566296fe-e0e8-475f-ba9c-a31ad31620b1} |
| CLASSID | {64B8F404-A4AE-11D1-B7B6-00C04FB926AF} |
| File path | %userprofile%\AppData\Local\Microsoft\Windows\WebClassUser.dat |
| File path | %localappdata%\Microsoft\Windows\WebCache\WebCacheR.tmp.dat |
| File path | %userprofile%ppdata\local\Microsoft\GameDVR\data\GameList.dat |
| File path | %userprofile%ppdata\local\Microsoft\GameDVR\data\DataCache.dat |
| File path | %temp%\wcts66889.tmp |
| File path | %localappdata%\Microsoft\Windows\UsrClassCache.dat |
| File path | %localappdata%\Microsoft\Windows\UsrClassLib.dat |
| File path | %userprofile%ppdata\local\Microsoft\Edge\cache\Config.dat |
| File path | %userprofile%ppdata\Local\Microsoft\Windows\UsrClassCache.dat |
| File path | %userprofile%ppdata\local\Microsoft\Edge\cache\Cache.dat |
Appendix D: Commands
| Command | Contents |
|---|---|
| turn on | Change the interval settings |
| turn off | Reset the interval settings |
| cd | Change directory |
| ddir | List of the files in the directory |
| ddel | Delete file and directory |
| ld | Load module |
| uld | unload module |
| attach | Start module |
| detach | Stop module |
| procspawn | Start process |
| prockill | None |
| proclist | None |
| diskinfo | Get disk information |
| download | Download encrypted file |
| downfree | Download file |
| cancel | Remote shell |
| screenupload | Upload screenshot |
| screenauto | Upload screenshot automatically |
| upload | Upload file |
Appendix E: Email address used for the commit
kithatart@outlook.com magnolia099@163.com carolab989@proton.me fenchiuwu@proton.me Ridgley223870@proton.me
Appendix F: Victimized devices identified from the GitHub repository
1014988494f04da28046ba 1020301627MBE4OSU 2096821130DESKTOP-BN9A2SA 2958455713DESKTOP-NKVAKV1 4205732935******(Names have been masked as they may contain personal information) 3761538073DESKTOP-PVKDUAM 3537034124JKS 3472318429******(Names have been masked as they may contain personal information) 1620260207DESKTOP-6LO36DE 1347261043DESKTOP-0V7K7HA 2352730816DESKTOP-4QC5J5Q 3362573326DESKTOP-43R2GH0

