TSUBAME Report Overflow (Apr-Jun 2025)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports do not include. This article covers the monitoring results for the period April to June 2025.
Fluctuations in packets from Iran, potentially linked to Israel-Iran military conflict
Between June 13 and around June 25, 2025, military conflict occurred between Israel and Iran. During this period, fluctuations were observed in packets originating from Iran. This section focuses on these changes. Figure 1 shows the number of unique IP addresses per day originating from Iran and Israel during June.
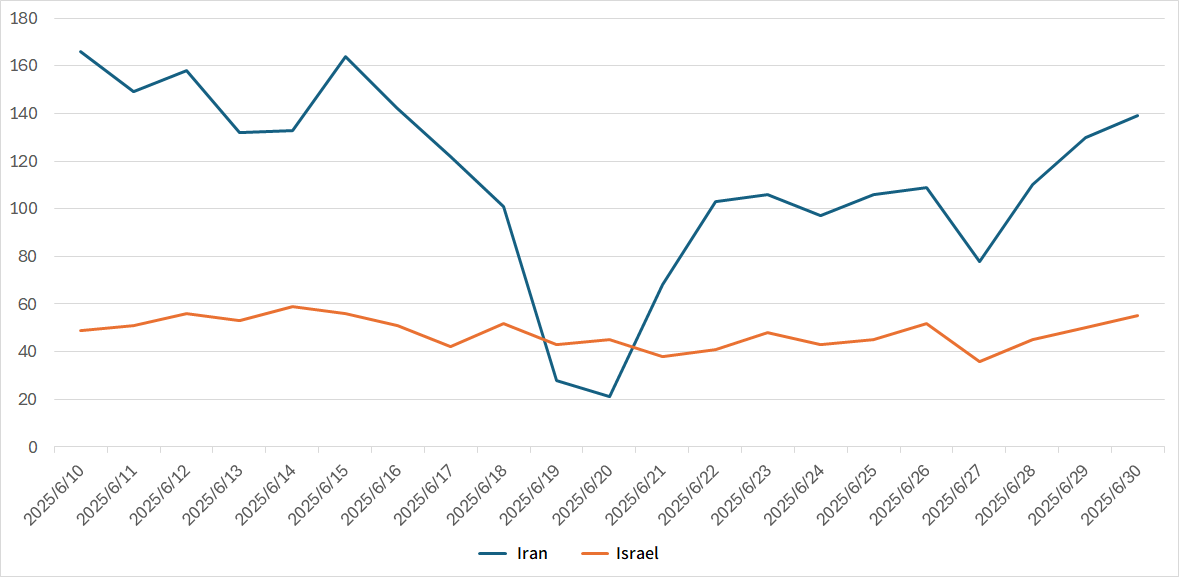
|
| Figure 1: Trends in the number of IP addresses from Israel and Iran |
The number of IP addresses associated with packets originating from Iran typically ranged between 170 and 200 every day. However, from around June 13 to June 18, this number dropped to approximately 100 to 130. A more significant decrease was observed from June 19 to June 27, when the number temporarily dropped to between 20 and 100. In contrast, the number of IP addresses originating from Israel showed no notable changes during the same period. Some media sources reported that, around June 18, cyber attacks targeted Iran’s state broadcaster, banks, and cryptocurrency exchanges. It was also reported that the Iranian government temporarily restricted Internet connectivity to mitigate the impact of these attacks, and the decline in the number of source IP addresses was likely due to this disruption.
Comparison of the observation trends in Japan and overseas
Figure 2 is a monthly comparison of the average number of packets received in Japan and overseas. While overseas sensors received more packets than those in Japan, both of them recorded the highest number in April, with a gradual decrease in the following months.
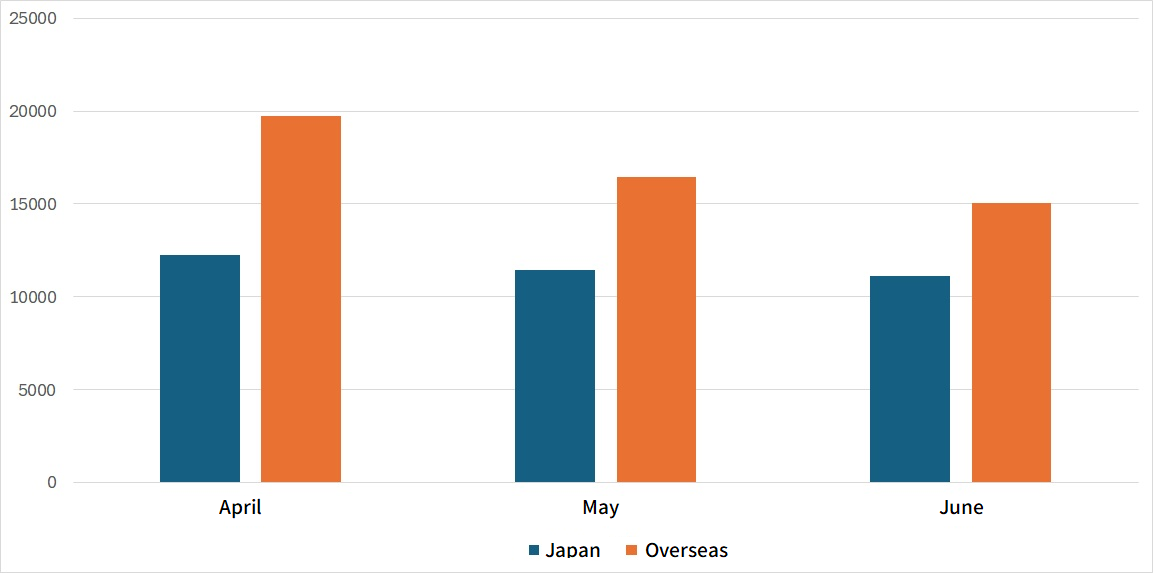
|
| Figure 2: Monthly comparison of the average number of packets received in Japan and overseas |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 1 shows the top 10 ports of each sensor which received packets the most. Although the order is different in each sensor, almost all the sensors observed the packets for 22/TCP, 23/TCP, 80/TCP, 443/TCP, and 8080/TCP. This suggests that these protocols are being scanned in a wide range of networks.
Table 1: Comparison of top 10 packets by domestic and overseas sensors
| Japan #1 | Japan #2 | North America #1 | North America #2 | Europe #1 | Europe #2 | Other regions #1 | Other regions #2 | |
|---|---|---|---|---|---|---|---|---|
| #1 | 23/TCP | 23/TCP | 80/TCP | 80/TCP | 23/TCP | 23/TCP | 23/TCP | 23/TCP |
| #2 | 443/TCP | 8728/TCP | 22/TCP | ICMP | 443/TCP | 22/TCP | 80/TCP | 80/TCP |
| #3 | 80/TCP | 80/TCP | 8728/TCP | 443/TCP | 80/TCP | 8728/TCP | 8728/TCP | 8728/TCP |
| #4 | 8443/TCP | 22/TCP | 23/TCP | 23/TCP | 22/TCP | 80/TCP | 22/TCP | 443/TCP |
| #5 | 8728/TCP | ICMP | 443/TCP | 8728/TCP | 8728/TCP | 34567/TCP | 443/TCP | 22/TCP |
| #6 | 22/TCP | 443/TCP | 8080/TCP | 22/TCP | 445/TCP | ICMP | ICMP | ICMP |
| #7 | ICMP | 81/TCP | ICMP | 8080/TCP | ICMP | 443/TCP | 8080/TCP | 8080/TCP |
| #8 | 8080/TCP | 8080/TCP | 3389/TCP | 6379/TCP | 8080/TCP | 81/TCP | 81/TCP | 81/TCP |
| #9 | 81/TCP | 5555/TCP | 445/TCP | 3389/TCP | 1433/TCP | 8080/TCP | 5555/TCP | 5555/TCP |
| #10 | 6379/TCP | 3389/TCP | 81/TCP | 81/TCP | 6379/TCP | 445/TCP | 6379/TCP | 6379/TCP |
In closing
Monitoring at multiple locations enables us to determine if certain changes are occurring only in a particular network. Although we have not published any special alerts as an extra issue or other information this quarter, it is important to pay attention to scanners. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the comment form below to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano
(Translated by Takumi Nakano)

