TSUBAME Report Overflow (Jul-Sep 2024)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of July to September 2024.
Packets from TP-LINK routers other than AX3000
JPCERT/CC analyzes the data collected by TSUBAME every day. In the previous article , we discussed scans from IP addresses that appear to be from TP-LINK wireless LAN routers (AX3000). By tracing the source IP addresses of the scan packets captured by TSUBAME, we found that they were from TP-LINK wireless LAN routers. Table 1 shows the models that JPCERT/CC has confirmed.
Table 1: TP-LINK wireless LAN routers sending scan packets
| Identified models |
|---|
| AX1800 Wi-Fi 6 Router |
| AX3000 Wi-Fi 6 Router |
| AX5400 Wi-Fi 6 Router |
| AX6000 Wi-Fi 6 Router |
| Wireless Router Archer AX50 |
| MR70X |
| A6 MU-MIMO Wi-Fi Router |
| AC2600 MU-MIMO Wi-Fi Router |
Among the Firmware versions we confirmed, there were some old versions provided before 2023. It is reasonable to assume that attackers infected such un-maintained wireless LAN routers with malware by exploiting vulnerabilities to send scan packets. Mirai is a typical example of malware targeting IoT devices, but affected devices do not always send scan packets. For Internet-connected devices, it is essential to use supported products, update the firmware version, and ensure that the routers are properly configured. Maintenance work on a regular basis is important. Please check the vendor’s information regularly for new firmware releases, and properly restrict access to the Internet.
Comparison of the observation trends in Japan and overseas
Figure 1 is a monthly comparison of the average number of packets received in Japan and overseas. Overseas sensors received more packets than those in Japan.
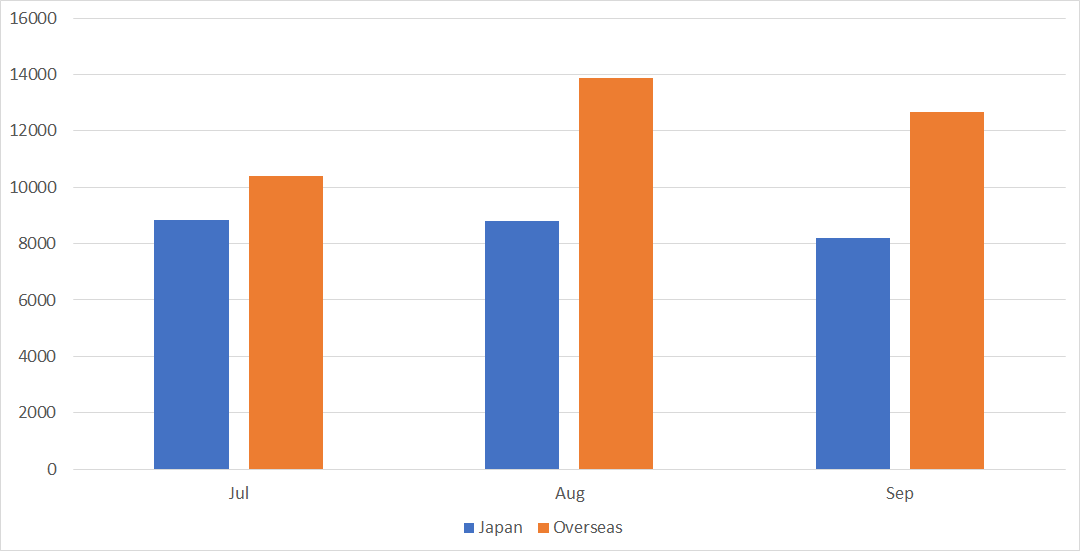
|
| Figure 1: Monthly comparison of the average number of packets received in Japan and overseas |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 2 shows the top 10 ports of each sensor which received packets the most. Although the order is different in each sensor, almost all the sensors observed the packets for 23/TCP, 8728/TCP, 22/TCP, 8080/TCP, 80/TCP, and ICMP. This suggests that these protocols are being scanned in a wide range of networks.
Table 2: Comparison of top 10 packets by domestic and overseas sensors
| Sensor in Japan #1 | Sensor in Japan #2 | Sensor in Japan #3 | Sensor overseas #1 | Sensor overseas #2 | Sensor overseas #3 | |
|---|---|---|---|---|---|---|
| #1 | 23/TCP | 23/TCP | 23/TCP | 23/TCP | 23/TCP | 23/TCP |
| #2 | 8728/TCP | 8728/TCP | 8728/TCP | 8728/TCP | 8728/TCP | ICMP |
| #3 | ICMP | 80/TCP | 6379/TCP | 6379/TCP | 80/TCP | 8728/TCP |
| #4 | 80/TCP | 22/TCP | 80/TCP | 80/TCP | 445/TCP | 80/TCP |
| #5 | 22/TCP | 22/TCP | 80/TCP | 443/TCP | 22/TCP | 6379/TCP |
| #6 | 6379/TCP | 443/TCP | ICMP | 22/TCP | 22/TCP | 22/TCP |
| #7 | 3389/TCP | 8080/TCP | 3389/TCP | 443/TCP | 3389/TCP | 3389/TCP |
| #8 | 8080/TCP | 3389/TCP | 8080/TCP | ICMP | 8080/TCP | 443/TCP |
| #9 | 8081/TCP | 2222/TCP | 8081/TCP | 8081/TCP | ICMP | 8080/TCP |
| #10 | 443/TCP | 8081/TCP | 443/TCP | 3389/TCP | 8080/TCP | 1433/TCP |
In closing
Monitoring at multiple locations enables us to determine if certain changes are occurring only in a particular network. Although we have not published any special alerts as an extra issue or other information this quarter, it is important to pay attention to scanners. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the below comment form to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano
(Translated by Takumi Nakano)

