TSUBAME Report Overflow (Jan-Mar 2025)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports do not include. This article covers the monitoring results for the period January to March 2025.
Trends of Fiscal Year 2024 in Japan
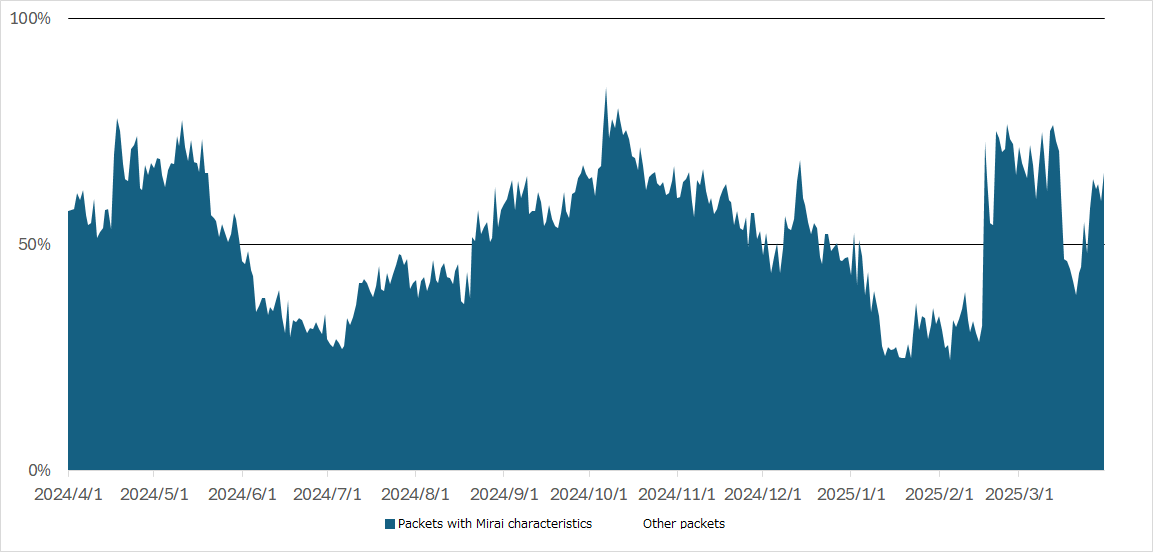
At JPCERT/CC, we analyze the data collected from TSUBAME on a daily basis. This time, we would like to focus on incident cases related to Japan based on the observation results from fiscal year 2024. We mentioned in the Internet Threat Monitoring Quarterly Reports that our sensors observed packets directed to port 23/TCP the most. Some of them have the characteristics of Mirai malware, and the trends in the number of such packets is shown in Figure 1. For example, around May 2024, from September to December 2024, and around March 2025, packets directed to port 23/TCP with Mirai characteristics accounted for more than 50% of the total, while during other periods, packets targeting a wide variety of IoT devices without Mirai characteristics were observed.
|
| Figure 1: Trends in the number of source IP addresses sending packets with Mirai characteristics from within Japan to Port 23/TCP |
In TSUBAME project, when suspicious scans are observed, we attempt to collect information and identify the devices (specifically for IP addresses in Japan) by using Web responses, SHODAN, and other tools, for the purpose of incident reporting and information sharing. During the three notable periods mentioned earlier, the following types of devices were particularly identified:
- Around May 2024: Routers from overseas vendors such as TP-Link
- Around September to December 2024: Security cameras, DVRs, and NAS devices from overseas vendors
- Around February to March 2025: Routers from overseas vendors such as ASUS
We have observed that the same IP addresses used to send packets with Mirai characteristics to port 23/TCP were also used for the attempts to communicate with other ports. It is considered that the attackers perform scans recognizing accessible ports from the Internet and vulnerability information on the target products. Additionally, reflected packets from the web servers of several companies were also observed. Since these are considered to be part of DDoS attacks targeting organizations, we provided the observation data through CSIRTs and other community paths. Based on the insights obtained from these activities, we have shared information about trends in attacks using Mirai and discussed countermeasures with domestic product developers and ISPs. To mitigate the damage from Mirai infections and DDoS attacks, it is essential to be cautious when using routers and similar devices connected to the Internet to avoid the spread of infections and prevent the expansion of botnets. Keeping in mind that attackers may also access your devices through the Internet, make sure to install the latest firmware, apply proper settings, and use the devices with cautions. After implementation, it is recommended to conduct port scans to check if unnecessary ports are made inaccessible. Using tools such as SHODAN is also recommended. Since attacks targeting specific products and suspicious packet sources will continuously appear in the future, TSUBAME project will continue to provide observation data and other information to product developers and ISPs to help them solve such issues.
Comparison of the observation trends in Japan and overseas
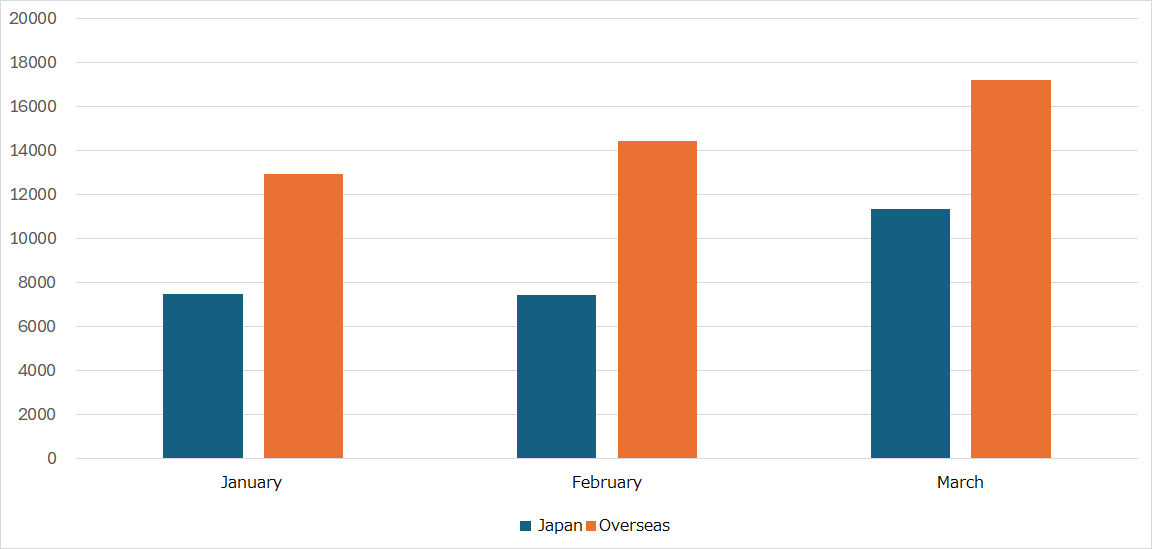
Figure 2 is a monthly comparison of the average number of packets received in Japan and overseas. Overseas sensors received more packets than those in Japan, and particularly, the number of packets increased both in Japan and overseas in March.
|
| Figure 2: Monthly comparison of the average number of packets received in Japan and overseas |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 1 shows the top 10 ports of each sensor which received packets the most. Although the order is different in each sensor, almost all the sensors observed the packets for 23/TCP, 6379/TCP, 22/TCP, 8080/TCP, 80/TCP, ICMP. This suggests that these protocols are being scanned in a wide range of networks.
Table 1: Comparison of top 10 packets by domestic and overseas sensors
| Sensor in Japan #1 | Sensor in Japan #2 | Sensor in Japan #3 | Sensor overseas #1 | Sensor overseas #2 | Sensor overseas #3 | |
|---|---|---|---|---|---|---|
| #1 | 23/TCP | 23/TCP | 23/TCP | 23/TCP | 23/TCP | ICMP |
| #2 | 8728/TCP | 8728/TCP | 8728/TCP | 8728/TCP | 8728/TCP | 23/TCP |
| #3 | 123/UDP | 80/TCP | 22/TCP | 22/TCP | 80/TCP | 8728/TCP |
| #4 | 22/TCP | 22/TCP | 80/TCP | 80/TCP | ICMP | 22/TCP |
| #5 | 80/TCP | ICMP | ICMP | ICMP | 443/TCP | 80/TCP |
| #6 | ICMP | 8080/TCP | 443/TCP | 443/TCP | 22/TCP | 443/TCP |
| #7 | 8080/TCP | 443/TCP | 8080/TCP | 8080/TCP | 8080/TCP | 8080/TCP |
| #8 | 443/TCP | 6379/TCP | 6379/TCP | 6379/TCP | 6379/TCP | 3389/TCP |
| #9 | 6379/TCP | 81/TCP | 34567/TCP | 445/TCP | 2222/TCP | 445/TCP |
| #10 | 34567/TCP | 123/UDP | 445/TCP | 2222/TCP | 3389/TCP | 34567/TCP |
In closing
Monitoring at multiple locations enables us to determine if certain changes are occurring only in a particular network. Although we have not published any special alerts as an extra issue or other information this quarter, it is important to pay attention to scanners. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the comment form below to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano
(Translated by Takumi Nakano)

