Protected Mode in Internet Explorer
Hello, this is Shusei Tomonaga again from the Analysis Center.
JPCERT/CC has been observing cases where vulnerability in Internet Explorer (“IE” hereafter) is leveraged in targeted attacks, etc., resulting in system takeover or configuration change by a third party. In fact, IE has several functions to prevent such exploits. In this article, I will introduce one of the functions called “Protected Mode” – its overview and effects.
OVERVIEW OF PROTECTED MODE
“Protected Mode” is a new feature of IE 7 and later, which is enabled by default. This function runs by using an access control mechanism called “Integrity Level” which has been introduced with Windows Vista. Resources (such as files and registry entries) and processes have their own integrity levels (currently High, Medium or Low, but extensible in the future). When accessing, this access control mechanism requires that the integrity level of the accessing process is the same or higher than the resource which will be accessed.
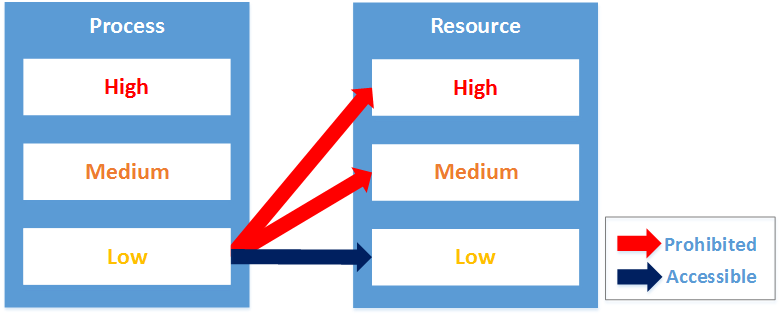 |
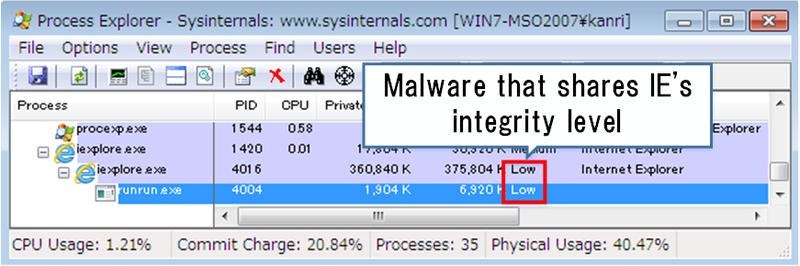
Ordinary processes started by Command Prompt has a “Medium” integrity level, while IE processes in Protected Mode has a “Low” integrity level. Child processes have the same integrity level or lower integrity levels than their parent processes. As a result, malware deriving from an IE vulnerability will be running as “Low” integrity level, whether it is running as an IE process or its child process. Consequently, malware will have limited access to resources, which is expected to limit its intended behaviour.
 |
VERIFYING MITIGATION EFFECT BY PROTECTED MODE
In order to verify how IE Protected Mode is effective in reducing damage by malware infection, we analysed how malware behaviour is limited in such environment. We took Poison Ivy as an example. Table 1 below describes the result of the analysis.
| Item | Poison Ivy's Attack Vector | Behaviour under Protected Mode |
|---|---|---|
| 1 | Send information of infected computers (host name, IP address, etc.) | Capable |
| 2 | Create/delete/download files/folders, execute programs | Limited (Only able to create/delete “Low” integrity level files/folders - e.g. “%TEMP%\Low” folder, etc.) |
| 3 | Create/modify/delete/view/search registry entries | Limited (Unable to create/modify/delete) |
| 4 | Obtain list of running processes, suspend processes | Capable |
| 5 | Obtain list of installed applications | Capable |
| 6 | Window-related commands (Obtain information/image, key input, display, hide, maximise, minimise) |
Incapable |
| 7 | Screen capture | Capable |
| 8 | Execute arbitrary shell commands | Limited (Executable on “Low” integrity level) |
As shown in Items 2 and 3 in the table, malware can neither create files in Startup folders nor create registry entries, therefore it cannot set up the necessary configuration for auto-run. Consequently, the process of malware disappears upon system shutdown, and will not persistently run on the computer. Other than that, however, other malware functions which could lead to information leakage (e.g. sending information of the infected computer, obtaining screen captures, etc.) cannot be blocked even under Protected Mode. This is because the operations restricted by integrity levels are configured for each resource as access policy, and it does not restrict all the operations (write/read/execute). Table 2 below shows items which can be configured as access policy.
| Configuration | Contents |
|---|---|
| No-Write-Up | Rejects writing from lower integrity level(s) |
| No-Read-Up | Rejects reading from lower integrity level(s) |
| No-Execute-Up | Rejects execution from lower integrity level(s) |
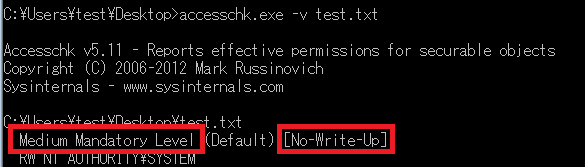
For example, a text (.txt) file created by Notepad in a document folder has a “Medium” integrity level and only a “No-Write-Up” access policy by default. Therefore, if malware running with “Low” integrity level attempts to write on this file, it fails. However, since it does not have a “No-Read-Up” policy, it can read files – hence information leakage cannot be prevented.
 |
IN SUMMARY
Protected Mode can save the risk of malware from persistently running even after reboot. However, the above analysis clearly indicates that this is not robust enough against information theft.
In fact, IE has a stronger security feature called “Enhanced Protected Mode”, which is expected to prevent further damage. In the coming entry, I will introduce this enhanced feature.
Thank you for reading and see you soon.
- Shusei Tomonaga
REFERENCE
[1] Understanding and Working in Protected Mode Internet Explorer
https://msdn.microsoft.com/en-us/library/bb250462%28v=vs.85%29.aspx

