Hello, this is Shusei Tomonaga again from the Analysis Center. JPCERT/CC has been observing cases where vulnerability in Internet Explorer (“IE” hereafter) is leveraged in targeted attacks, etc., resulting in system takeover or configuration change by a third party. In fact, IE has several functions to prevent such exploits. In this article, I will introduce one of the functions called “Protected Mode” – its overview and effects. OVERVIEW OF PROTECTED...
List of “2015”
-
-
Hola! This is Shoko from Incident Response Team. Last month I attended the APWG eCrime 2015, held from May 26-29 in Barcelona – the cosmopolitan capital of Spain’s Catalonia region, defined by quirky art and architecture, imaginative cuisine and siesta. Today, I’d like to share an overview of the APWG eCrime 2015 and my presentation there on “Phishing Trends in Japan.” About APWG and APWG eCrime 2015 You may well...
-
NOTE: This article, originally published on May 28, 2015, was updated as of June 8, 2015 (See below). Just 2 days ago, we published an advisory (in Japanese) on an open proxy issue of a widely used, open source, web browser game utility app called KanColleViewer. The game, Kantai Collection, has explosive popularity. Its official Twitter account has over 1 million followers, and according to its Tweet, the game has...
-
G’day all – It’s Yuka again here from Global Coordination Division. I would like to quickly update about my recent trip to Canberra, Australia, where I attended the inaugural conference of Australian Cyber Security Centre (ACSC). The event attracted more than 800 people mainly from the Australian Government and IT related businesses but also some delegates from neighbouring countries. ACSC consists of the following cyber security related entities in Australia:...
-
Hello, I am Moto Kawasaki and I would like to write about my trip to Yangon, Myanmar from March 8th through 13th, 2015. Koichiro "Sparky" Komiyama and I went there to conduct Apache Log Analysis training and “CSIRT in a Box” training for mmCERT/CC, Myanmar Computer Emergency Response Team / Coordination Center. It is the 5th time starting in 2011 that JPCERT/CC visits mmCERT/CC for technical training. We had a...
-
Hello all, this is Yohei Tanaka from Analysis Center. In this article, I will introduce how recent malware tries to trick users with fake thumbnail previews – I hope this information prevents you from encountering troubles. The majority of malware distributed via email nowadays are executable files (.exe) or compressed executable files, rather than document files that attempt to leverage software vulnerabilities. We at JPCERT/CC have seen cases where users...
-
JPCERT/CC has successfully hosted the seventh Control System Security Conference on February 12, 2015 at Kokuyo Hall in Tokyo. The event brought together more than 250 attendees, including a cross-section of engineers/managers of ICS vendors and asset owners. The conference has been held annually since 2009 in order to raise awareness on ICS security issues and share the insights and ideas on ICS security. The program for this year has...
-
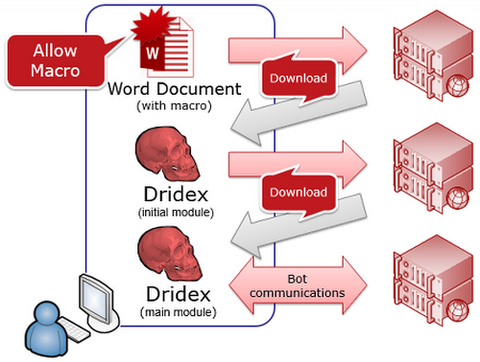
NOTE: This article, originally published on 13 February, 2015, was updated as of 12 May, 2015 (See below). Hello all, this is You Nakatsuru (“TSURU”) from Analysis Center again. Today, I would like to describe a new UAC bypass method that has been used by the Dridex malware since December, 2014. Introduction Dridex is a banking trojan, which is a bot that communicates with a CC server through HTTP. Most...
-
This is Shusei Tomonaga at Analysis Center. PlugX, a Remote Access Tool (RAT) often seen in many APT cases, has been in the wild for some years. Various sectors in Japan have been suffering from this type of attack from 2012, and Analysis Center has been working to catch up on the evolution of the PlugX family since then. In this blog post, I will write about a recent PlugX...
-
Happy New Year 2015 to everyone! I am Toru Yamauchi, Research Director of JPCERT/CC. JPCERT/CC has been contributing to the CSIRT community in Africa in order to enhance the global cybersecurity activity. In the rapid ICT development in Africa, it is getting more important for them to accelerate human development in cybersecurity area and to establish regional cooperation especially among National CSIRTs. I would like to introduce our recent on-site...

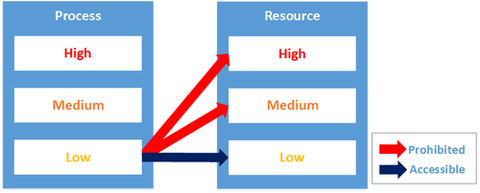


.png)