Malware with a Fake Thumbnail Preview
Hello all, this is Yohei Tanaka from Analysis Center.
In this article, I will introduce how recent malware tries to trick users with fake thumbnail previews – I hope this information prevents you from encountering troubles.
The majority of malware distributed via email nowadays are executable files (.exe) or compressed executable files, rather than document files that attempt to leverage software vulnerabilities. We at JPCERT/CC have seen cases where users themselves opened and executed .exe files and unfortunately got infected by the malware.
Thanks to awareness raising efforts, many of you now recognise that those suspicious executable attachments should not be opened. In order to get users infected with malware, attackers now have started to “camouflage” the malicious attachments to look harmless, so they get opened and executed without any doubt of it being malicious. Until recently, malware was disguised by assigning an icon of a well-known application, but it seems that even this method no longer works against security-conscious users.
This article describes a little more sophisticated camouflage technique abusing thumbnail preview, which is a relatively new function in Windows.
Thumbnail Preview
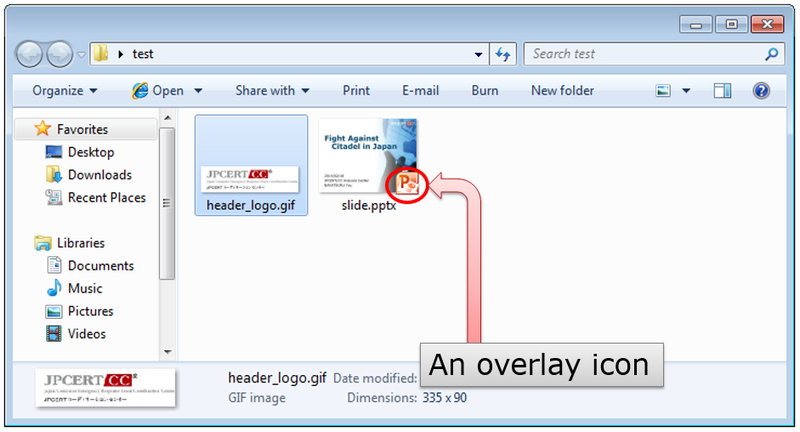
Since Windows Vista, if you select icons larger than “Small Icons”, a thumbnail preview of the image file (.jpg, .bmp, etc.), instead of an application icon will be shown (as in “header_logo.gif” in Figure 2). Also, some files other than images can be previewed as an icon. For example, in an environment with Microsoft Power Point, a thumbnail preview will be displayed (as in slide.pptx in Figure 2). When “Medium Icons” or larger is selected, an overlay icon showing the assigned application can be seen in thumbnail preview. For more information on this configuration, please see Appendix A.
This feature allows you to easily grasp an overview of the files in Explorer and choose what they are looking for.
Malware with “fake” thumbnail preview
JPCERT/CC has observed malware which use "fake" icons that can be seen as invoice or receipt files as shown in Figure 3. This way, file recipients may tend to focus on the “content” itself rather than the file type – which may give them the idea that the files are safe to open.
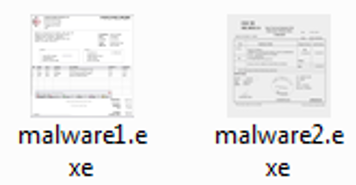 |
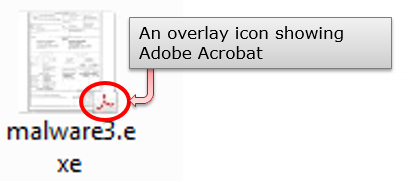
We have also seen malware with a fake overlay icon as in Figure 4. It is difficult for you to tell if it is fake or not, just by looking at application icons.
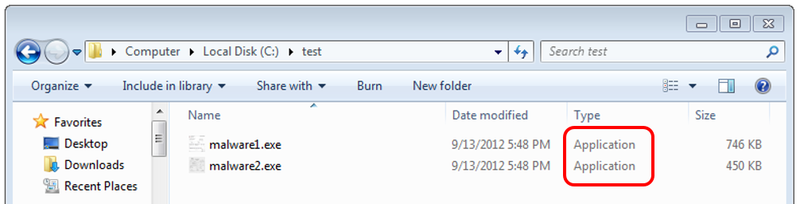
How are they displayed when choosing “Extra Large Icons”? In Figure 5, I tried displaying the same malware in the Figure 3 with Extra Large Icons. “malware1.exe” does not have any Extra Large Icon, and it just shows the medium-sized icon in a large-sized frame. From this, you may actually detect that it is a malicious file. However, “malware2.exe” does also have a large-sized icon, and you cannot verify just by looking at this.
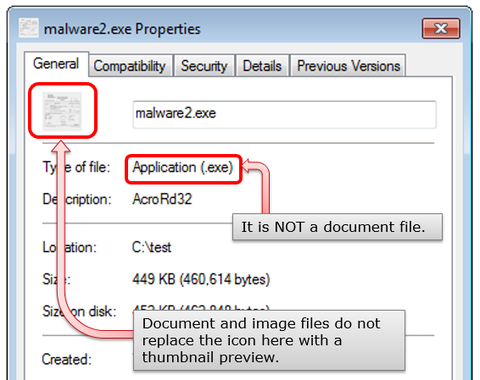
However, even for malware with a fake icon as in the second example above, there are ways for you to verify if it is malware or not. You can do so by either checking the “type of file” in Properties as in Figure 6 or in Explorer by expanding to view the details as in Figure 7.
Summary
Attackers create icons with fake thumbnail previews in alignment with e-mail addressees and/or the contents that they are attached to, so that the recipients feel urged to open the attachment. Malware which looks like invoice or receipt files, as introduced here, is commonly used. Particularly in cases of targeted attack, recipients are deceived by a fake document that reasonably could have been created by the target or someone within the target's organization.
We believe it is important to raise awareness of the general public about these risks so that they have more discretion when it comes to email attachments – not be deceived by the icon “look” but to stop for a second and check before opening.
Thank you for reading.
- Yohei Tanaka
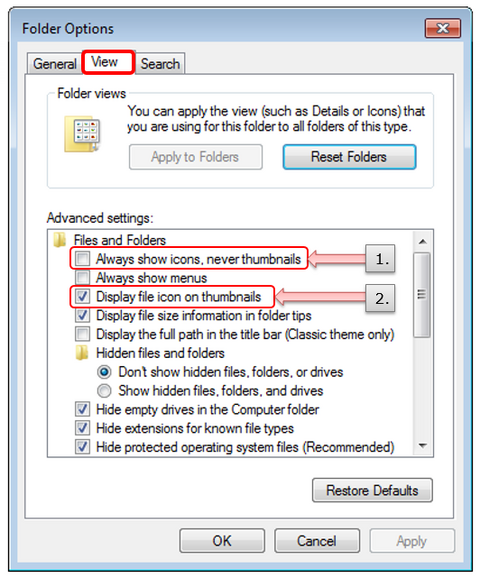
Appendix A: Options on Folders related to Thumbnail Preview
1. “Always show icons, never thumbnails”
- Checked: Not show thumbnail previews as icons
- Unchecked: Show thumbnail previews as icons (Default setting)
2. “Display file icon on thumbnails”
- Checked: Show an overlay icon in addition to the thumbnail (Default setting)
- Unchecked: Not show an overlay icon
Appendix B: Sample’s SHA-256 Hash Value
- malware1: 43cec9a519610592f58c216c7bd1d8a6859f0df506675e32e4834ad021604588
- malware2: 13b02346c79f79d85eb4c8a0ac4b455bb5e69ae25fae3001bdd2040ffb28eedf
- malware3: 8605cb1ef0a1cdd89f38fac4e1964cf3f65c5f159edd3d2c5f8b64e93f1aeaee