Credential Theft and Domain Name Hijacking through Phishing Sites
In early July 2023, JPCERT/CC confirmed a case of domain hijacking in which a domain used in Japan was unauthorizedly transferred to another registrar. This blog post describes the attack case.
Attack overview
Figure 1 shows the attack flow. The attacker first prepared a phishing site, which pretended to be a registrar on search site advertisements.
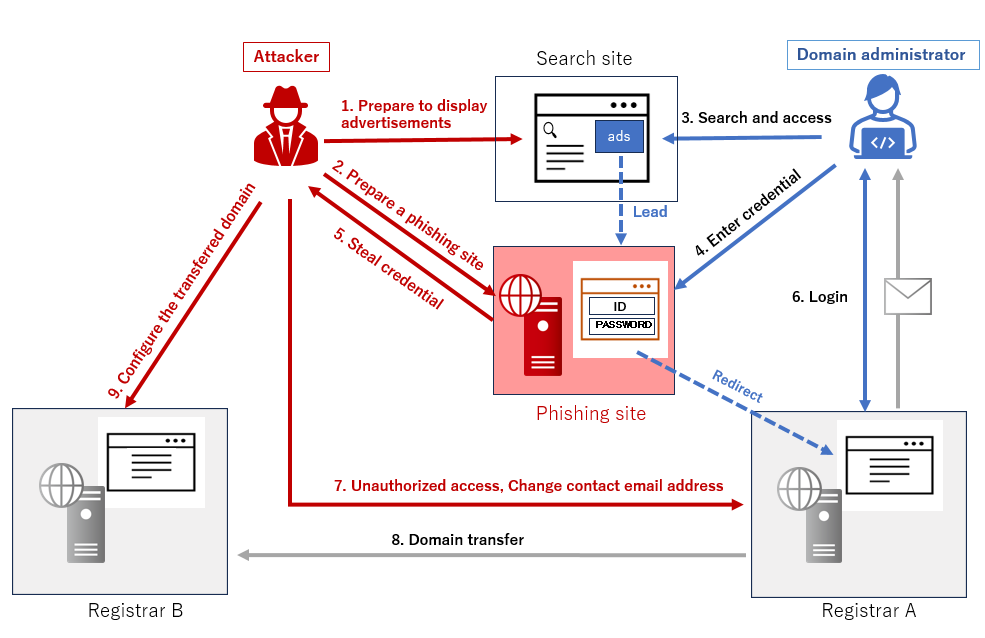
Figure 1: the attack flow
An attacker can steal account information and password (hereafter referred to as "credential") when a domain administrator accesses a phishing site and enters the credential. After the victim enters their credential on this phishing site, they are redirected to the legitimate site logged in. Therefore, it is difficult for them to recognize the phishing.
The attacker then used the stolen credential to log into the registrar’s legitimate site and proceeded to transfer the domain to another registrar. Although the domain administrator had used the domain transfer lock feature for the targeted domain, the attacker unlocked it. In the process of unlocking, this registrar sends an email to user's contact email address for confirmation and approval. However, the attacker also changed the contact email address.
Measures that can be taken in advance
The following actions are recommended to prevent the attacks described above:
- Do not assume that the link displayed on the search site is correct. Instead, access the site from a confirmed official application or a URL that you have bookmarked in your web browser
- Use the security features provided by the site (e.g., two-factor authentication)
- Avoid simple passwords or using the same password repeatedly
References
[1] Council of Anti-Phishing Japan: What is Phishing?
https://www.antiphishing.jp/consumer/abt_phishing.html (Japanese)
[2] Council of Anti-Phishing Japan: Anti-phishing Fraud Guidelines for Users (PDF)
https://www.antiphishing.jp/report/consumer_antiphishing_guideline_2023.pdf (Japanese)
[3] JPCERT/CC: STOP! Reusing Password!
https://www.jpcert.or.jp/pr/stop-password.html (Japanese)
It is also recommended to regularly check the information by the service provider you are using, as they may offer new security features on their site responding to the changes of attackers’ TTP.
Measures that can be taken after domain name hijacking is done
When you become a victim of domain name hijacking and notice that your domain is transferred without your authorization, contact the registrar you use to manage the domain.
References
[1] ICANN: Registrar Transfer Dispute Resolution Policy
https://www.icann.org/resources/pages/tdrp-2016-06-01-en
[2] JPCERT/CC: Publishing a technical document summarizing DNS abuse techniques
https://blogs.jpcert.or.jp/ja/2023/07/DNS-Abuse-Techniques-Matrix.html (Japanese)
In Closing
Unauthorized transfer of a domain has a significant impact on the site operating under the domain as well as the users browsing the site. In addition, depending on the situation, it may take some time to get the domain name back, and in the worst case, it may never be returned. Therefore, for the services you are currently using, please check the security measures of your account to prevent such attack in advance.
Tetsuya Mizuno
(Translated by Takumi Nakano)

