TSUBAME Report Overflow (Apr-Jun 2023)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of April to June 2023. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here.
Difference of observed packets in Japan and overseas sent from Japan
Along with the renewal of the TSUBAME system, we have also updated our sensors. In particular, the number of overseas sensors has increased. We have installed sensors at overseas hosting companies and other locations, and as of July 2023, TSUBAME sensors are in 17 regions. This blog article focuses on how much difference exists in the observed packets among the regions. Figure 1 summarizes the number of packets sent from Japan to the regions with multiple sensors installed. The minimum (MIN), maximum (MAX), and average (AVG) values are presented, considering the differences in the number of sensors among regions and differences among sensors in each region.
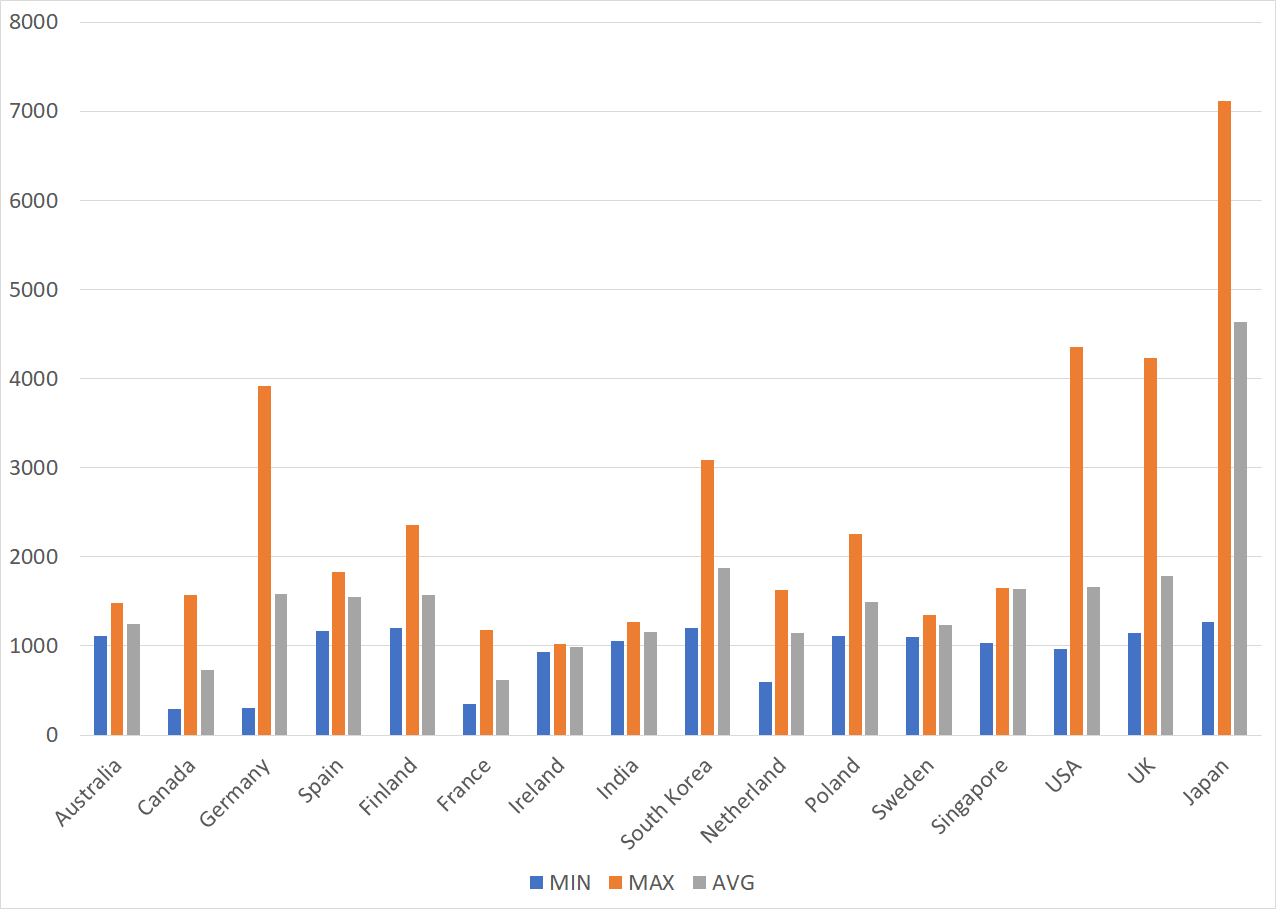 |
| Figure 1: Comparison of the number of packets sent from Japan to each region |
Comparison of the observation trends in Japan and overseas
Packets from these source IP addresses were observed by sensors located in Japan as well as some of the sensors located in South Korea. This likely resulted in larger AVG values for the sensors in Japan and MAX values for the sensors in South Korea. Scans are performed for a variety of purposes. I think it is important to know what kind of scans are usually performed. In particular, knowing the activities of the scan source can help us recognize what they are interested in, which can sometimes lead to hints for countermeasures for the network.
 |
| Figure 2: Monthly comparison of the average number of packets received in Japan and overseas |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 2 shows the top 10 ports of each sensor which received packets the most. Although the order is different in each sensor, almost all the sensors observed the packets for 23/TCP, 6379/TCP, 22/TCP, and 80/TCP. This suggests that these protocols are being scanned in a wide range of networks.
Table 1: Comparison of top 10 packets by domestic and overseas sensors
| #1 | #2 | #3 | #4 | #5 | #6 | #7 | #8 | #9 | #10 | |
| Sensor in Japan #1 | 23/TCP | ICMP | 22/TCP | 123/UDP | 6379/TCP | 8090/TCP | 80/TCP | 8088/TCP | 445/TCP | 3389/TCP |
| Sensor in Japan #2 | 23/TCP | 6379/TCP | ICMP | 22/TCP | 80/TCP | 445/TCP | 5555/TCP | 3389/TCP | 8080/TCP | 443/TCP |
| Sensor in Japan #3 | 23/TCP | 6379/TCP | 22/TCP | 80/TCP | 81/TCP | 5555/TCP | 445/TCP | 3389/TCP | 8080/TCP | 443/TCP |
| Sensor overseas #1 | 37215/TCP | 23/TCP | 22/TCP | 52869/TCP | 80/TCP | 445/TCP | 5555/TCP | 5060/UDP | 3389/TCP | ICMP |
| Sensor overseas #2 | 23/TCP | 6379/TCP | 22/TCP | 80/TCP | 5555/TCP | ICMP | 3389/TCP | 443/TCP | 1433/TCP | 8080/TCP |
| Sensor overseas #3 | 23/TCP | 445/TCP | 6379/TCP | 123/UDP | 22/TCP | 139/TCP | 80/TCP | 5555/TCP | 3389/TCP | ICMP |
In closing
Monitoring at multiple points makes it possible to see whether some trends are unique to a particular network. Although we have not published any special alerts as an extra issue or other information this quarter, it is important to pay attention to scanners. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the below comment form to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano
(Translated by Takumi Nakano)

