TSUBAME Report Overflow (Jul-Sep 2023)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of July to September 2023. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here .
Suspicious packets sent from routers sold by a Japanese manufacturer
Focus on routers sold by a Japanese manufacturer that I found while investigating the source IP addresses of the scans. Routers are used for a variety of purposes all over the world, not only as Wi-Fi routers at home, and a variety of devices can be found through investigating the source IP address of scans. Here, let’s take a look at routers used for industrial purposes. One day, I found in the observation data that the source IP addresses of scans were concentrated in certain domestic ISPs, and I started analyzing the data further. Eventually, I narrowed it down to two ISPs. Figure 1 shows the daily number of IP addresses that sent packets through the two ISPs.
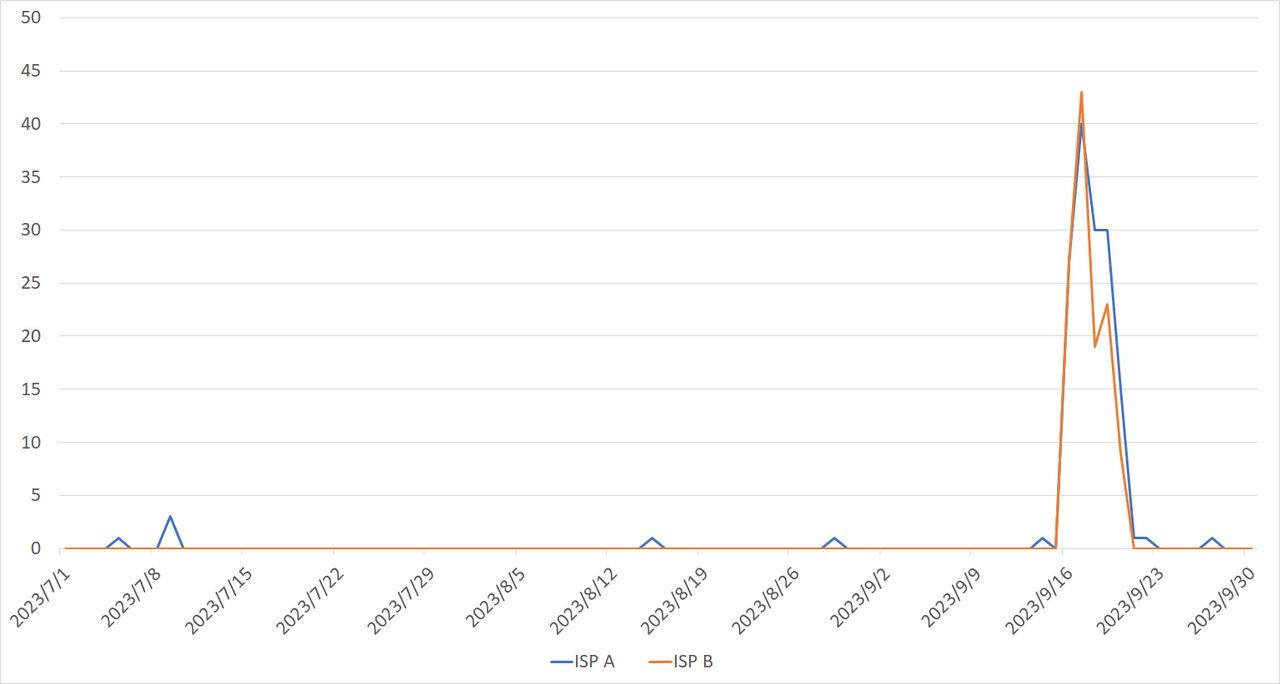
|
| Figure 1: Number of IP addresses that sent suspicious packets through the two ISPs |
The suspicious packets indicate that the devices may have been compromised by malware or that information which should not be disclosed may have been exposed due to improper settings. I shared the observation data with the ISPs and explained it through an online meeting. Understanding the situation that we JPCERT/CC explained, both ISPs cooperated with us to take necessary measures, and since then, we no longer observe such scans. I would also like to thank again everyone who have taken necessary actions responding to the ISP’s notifications. Meanwhile, it is also important to consider why such scans occurred. If the routers are used again with the underlying problem unsolved, they will be infected with malware again and cause other damages. To analyze the root cause, I first investigated what kind of devices were connected to some of the source IP addresses. As a result, I found that the routers’ management interface was exposed to the Internet, and the manufacturer and product was determined from the information such as IP addresses, SIM card phone numbers, and software versions of the routers. Currently, we are working with JPCERT/CC’s vulnerability coordination team to contact the manufacturer. Although the company responded to us once, unfortunately, the information obtained from TSUBAME data analysis has not yet been provided to them. We will keep trying to communicate with the company .
Comparison of the observation trends in Japan and overseas
Figure 2 is a monthly comparison of the average number of packets received in Japan and overseas. Overseas sensors received more packets than those in Japan.
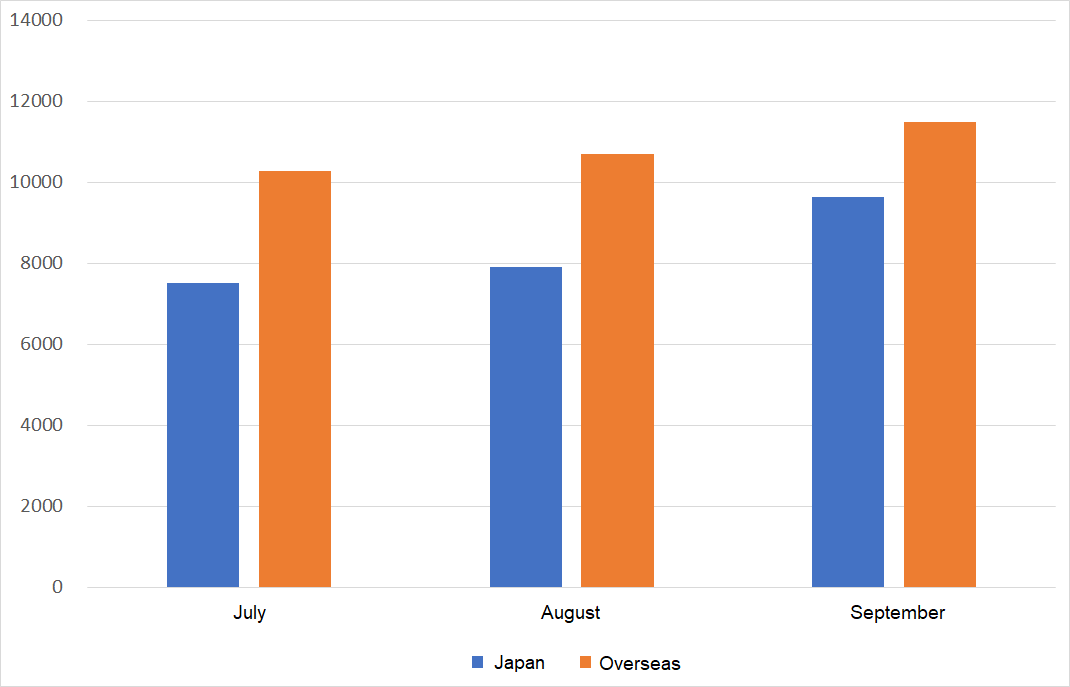
|
| Figure 2: Monthly comparison of the average number of packets received in Japan and overseas |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 1 shows the top 10 ports of each sensor which received packets the most. Although the order is different in each sensor, almost all the sensors observed the packets for 23/TCP, 6379/TCP, 22/TCP, and 80/TCP. 443/TCP, 8080/TCP, etc. are also moving up in the ranking. This suggests that these protocols are being scanned in a wide range of networks.
Table 1: Comparison of top 10 packets by domestic and overseas sensors
| #1 | #2 | #3 | #4 | #5 | #6 | #7 | #8 | #9 | #10 | |
| Sensor in Japan #1 | 23/TCP | 6379/TCP | 80/TCP | 8080/TCP | 22/TCP | ICMP | 443/TCP | 445/TCP | 3389/TCP | 1433/TCP |
| Sensor in Japan #2 | 23/TCP | 6379/TCP | 80/TCP | 22/TCP | 8080/TCP | 443/TCP | ICMP | 3389/TCP | 445/TCP | 5060/UDP |
| Sensor in Japan #3 | 23/TCP | 6379/TCP | 80/TCP | 22/TCP | 8080/TCP | 443/TCP | ICMP | 445/TCP | 3389/TCP | 5060/UDP |
| Sensor overseas #1 | 23/TCP | ICMP | 443/TCP | 80/TCP | 6379/TCP | 8080/TCP | 22/TCP | 445/TCP | 8443/TCP | 3389/TCP |
| Sensor overseas #2 | 23/TCP | ICMP | 6379/TCP | 80/TCP | 443/TCP | 22/TCP | 8080/TCP | 3389/TCP | 8443/TCP | 5060/UDP |
| Sensor overseas #3 | 23/TCP | ICMP | 445/TCP | 80/TCP | 443/TCP | 22/TCP | 3389/TCP | 8080/TCP | 5060/UDP/TCP | 1433/TCP |
In closing
Monitoring at multiple points makes it possible to see whether some trends are unique to a particular network. Although we have not published any special alerts as an extra issue or other information this quarter, it is important to pay attention to scanners. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the below comment form to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano
(Translated by Takumi Nakano)

