Around May 2022, JPCERT/CC confirmed an attack activity against Japanese organizations that exploited F5 BIG-IP vulnerability (CVE-2022-1388). The targeted organizations have confirmed that data in BIG-IP has been compromised. We consider that this attack is related to the activities by BlackTech attack group. This blog article describes the attack activities that exploit this BIG-IP vulnerability. Attack code that exploits the BIG-IP vulnerability Below is a part of the attack code...
List of “Incident”
-
-
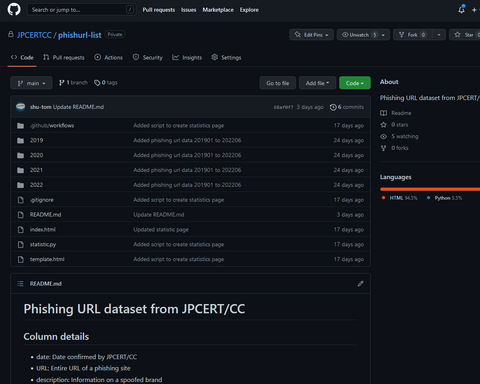
JPCERT/CC releases a URL dataset of phishing sites confirmed from January 2019 to June 2022, as we received many requests for more specific information after publishing a blog article on trends of phishing sites and compromised domains in 2021. The list is available in the following GitHub repository. Phishing URL dataset from JPCERT/CC https://github.com/JPCERTCC/phishurl-list/ Each column contains the following: date: Date confirmed by JPCERT/CC URL: Entire URL of a phishing...
-
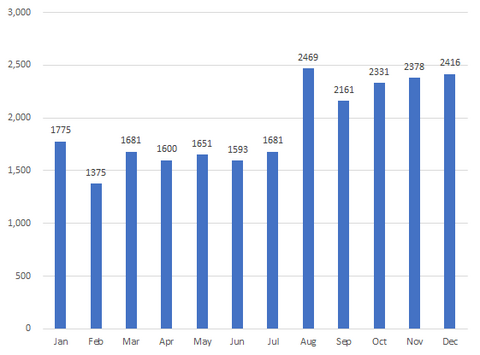
JPCERT/CC received 44,242 incident reports in 2021 and of that 23,104 ...
-
On 28 April 2021, Trend Micro reported the details of attacks exploiti...
-
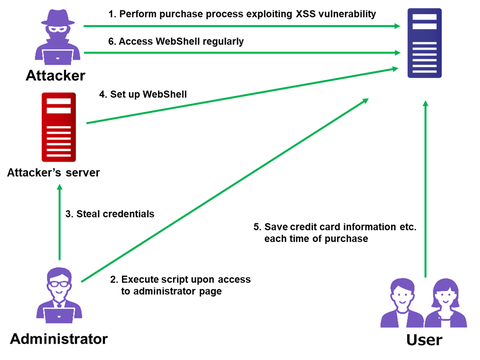
JPCERT/CC continues to observe cases of website being compromised and embedded with a malicious page. Visitors are redirected to a scam site or suspicious shopping site by malicious PHP script (hereafter, “PHP malware”). This article explains the details of PHP malware which is often found in websites in Japan. Cases observed On PHP malware-embedded websites, there are many malicious webpages that redirect visitors to a scam site or suspicious shopping...
-
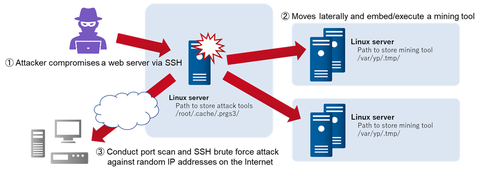
Publicly-accessible servers have been often targeted for attacks. In recent years, there are cases where these servers are compromised and embedded with a cryptocurrency mining tool. JPCERT/CC confirmed cases with XMRig [1] in February 2021. This article introduces the details of the cases and the tools used.Initial access/Lateral movementIn one of the recent cases, the attacker made several attempts to access the server with SSH protocol, and eventually logged in...
-
The attack group Lazarus (also known as Hidden Cobra) conducts various attack operations. This article introduces malware (VSingle and ValeforBeta) and tools used in attacks against Japanese organisations. VSingle overview VSingle is a HTTP bot which executes arbitrary code from a remote network. It also downloads and executes plugins. Once launched, this malware runs Explorer and executes its main code through DLL injection. (Some samples do not perform DLL injection.)...
-
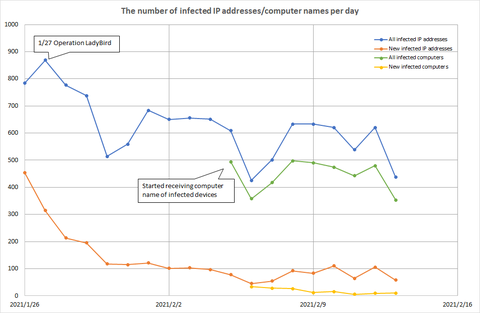
Since October 2019, many cases of Emotet infection were reported. JPCERT/CC has published a security alert and a blog article detailing the detection and security measures, as well as providing notification and support for affected users. Europol announced that Emotet infrastructure was disrupted thanks to the joint operation together with some foreign authorities in January 2021 and information regarding affected users is to be distributed via the CERT network. In...
-
It is widely known that attackers use Windows commands and tools that are commonly known and used after intruding their target network. Lazarus attack group, a.k.a. Hidden Cobra, also uses such tools to collect information and spread the infection. This blog post describes the tools they use. Lateral movement These three tools are used for lateral movement. AdFind collects the information of clients and users from Active Directory. It has...
-
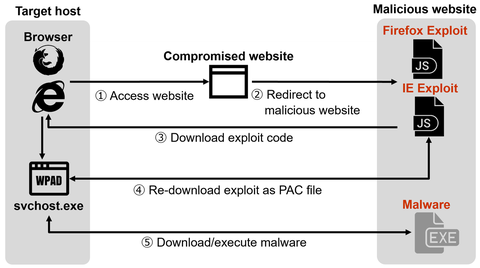
On 8 January 2020, Mozilla released an advisory regarding a vulnerability in Firefox. On 17 January, Microsoft reported that 0-day attacks exploiting a vulnerability in Internet Explorer (IE) had been seen in the wild. JPCERT/CC confirmed attacks exploiting both vulnerabilities at once and issued a security alert. This article explains the details of these attacks. Attack overview In this attack, victims are redirected to an attack site through a compromised...


.png)