Attacks Exploiting Vulnerabilities in Pulse Connect Secure
In September 2019, JPCERT/CC published a security alert regarding vulnerabilities in multiple SSL-VPN products.
Among the vulnerabilities pointed out in the alert, JPCERT/CC has been notified of cases leveraging CVE-2019-11510 and CVE-2019-11539 in Pulse Connect Secure in attacks against Japanese organisations. This activity seems to continue up until now according to some media reports.
As many companies encourage employees to “work from home” in the current situation, use of VPN products has been increasing. However, there are a large number of unpatched VPN devices running in Japan, and JPCERT/CC has been notifying the admins so that they can address the issue.
This article is to introduce the overview of the vulnerabilities in Pulse Connect Secure once again together with the ways to investigate the traces of the attack based on the logs and the number of vulnerable hosts in Japan.
Two vulnerabilities in Pulse Connect Secure VPN
Please see the security alert for details including the Pulse Connect Secure product versions that are affected by the vulnerabilities.
CVE-2019-11510
This vulnerability could allow attackers to read arbitrary files without authentication. Attackers could gain access to arbitrary files before the authentication process by sending a request made of a specially-crafted URI and strings to cause directory traversal.
Attackers will then be able to view files including plain text cache of credentials for past users and information of the sessions that was used for authentication. With the information, attackers can pretend to be a legitimate user and connect to SSL-VPN.
CVE-2019-11539
This vulnerability could allow an unauthorised third party to execute arbitrary code on Pulse Connect Secure through its Web GUI.
Pulse Connect Secure has several security mechanisms against command injection. In the affected product versions, however, attackers can bypass these mechanisms and execute arbitrary code.
Investigate Pulse Connect Secure user logs
Traces of an attack on Pulse Connect Secure can be identified by investigating user logs. Please see the following site to learn how to obtain them.
Displaying Events Logs - Pulse Connect Secure Techpubs's WebHelp
https://docs.pulsesecure.net/WebHelp/PCS/9.1R4/AG/Home.htm#PCS/PCS_AdminGuide/Displaying_Events_Logs.htm
If the abovementioned vulnerabilities are exploited, there is a possibility that the following attempts have been made:
- Authentication using stolen plain text credentials
- VPN connection using stolen credentials
The following sections will explain the logs that are recorded upon these attempts and how to analyse these logs. Please also look at the IoC related to these attack activities listed in Appendix A.
Investigate authentication attempts using stolen plain text credentials
If stolen plain text credentials are used for authentication by a third party, the logs recorded are the same as the legitimate authentication. It is necessary to check for behaviour which is different from usual authentication. The following information can be useful in determining the legitimacy:
- Hostname which performed the authentication
- Remote IP address
- User-Agent of the client
Figure 1 shows examples of unusual behaviour from logs. The contents are normalised based on the log output. Suspicious authentication attempts with the following features were made:
- Successful authentication from an unusual host
- Successful authentication from a foreign IP address in a short interval
- Unusual VPN client User-Agent
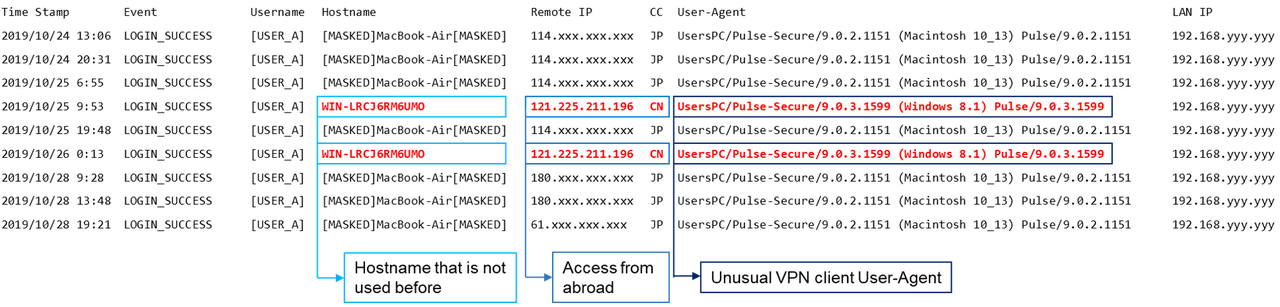
It is also suspicious if an authentication attempts from a single pair of an IP address and a hostname into multiple users succeeded as in Figure 2.

Investigate VPN connection using stolen credentials
If stolen credentials are used for authentication attempts, the following information may be recorded in the logs:
- Change of a remote IP address used for VPN connection
- Communication result of the VPN session
In this attempt, attackers cannot recognise if the stolen session information has expired and therefore tend to use sessions one after another. It is possible that expired sessions are also used. In this case, changes of a remote IP address from a single IP address is recorded multiple times as in Figure 3.
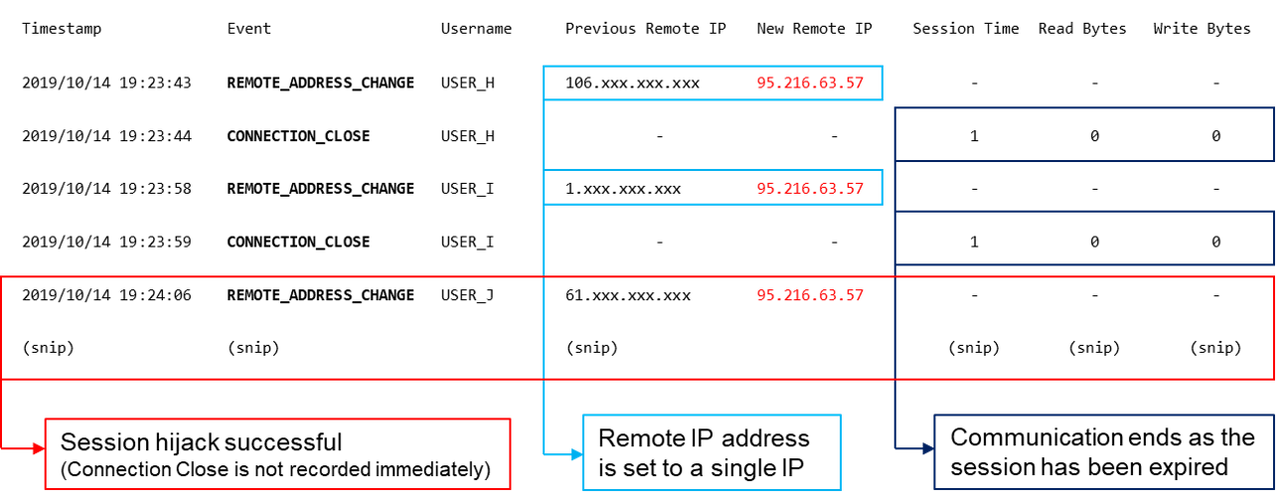
In case these attempts are recorded from a single remote IP address as in Figure 3, it is assumed that a suspicious connection has been made. It is also effective to check for any irregularity such as accesses from an unusual IP address range as in the example in Figure 1.
It is important to note that there are differences in log format and some errors in log entries in Pulse Connect Secure user logs depending on the firmware version. Please make sure to check the firmware version at the time of output.
Attackers’ behaviour after network intrusion
In the actual attack cases leveraging CVE-2019-11510, there was evidence that attackers have used tools such as PsExec and Mimikatz as well as stole Active Directory database file (ntds.dit) after intruding into a network using stolen credentials.
There are some other cases where endpoint security tools are deactivated and ransomware (Sodin/REvil) was installed according to some reports.
Number of vulnerable devices in Japan
JPCERT/CC has been notifying the admins of vulnerable Pulse Connect Secure hosts based on the investigation results from external sources. Figure 4 shows the number of hosts that are running with CVE-2019-11510 vulnerability in Japan.
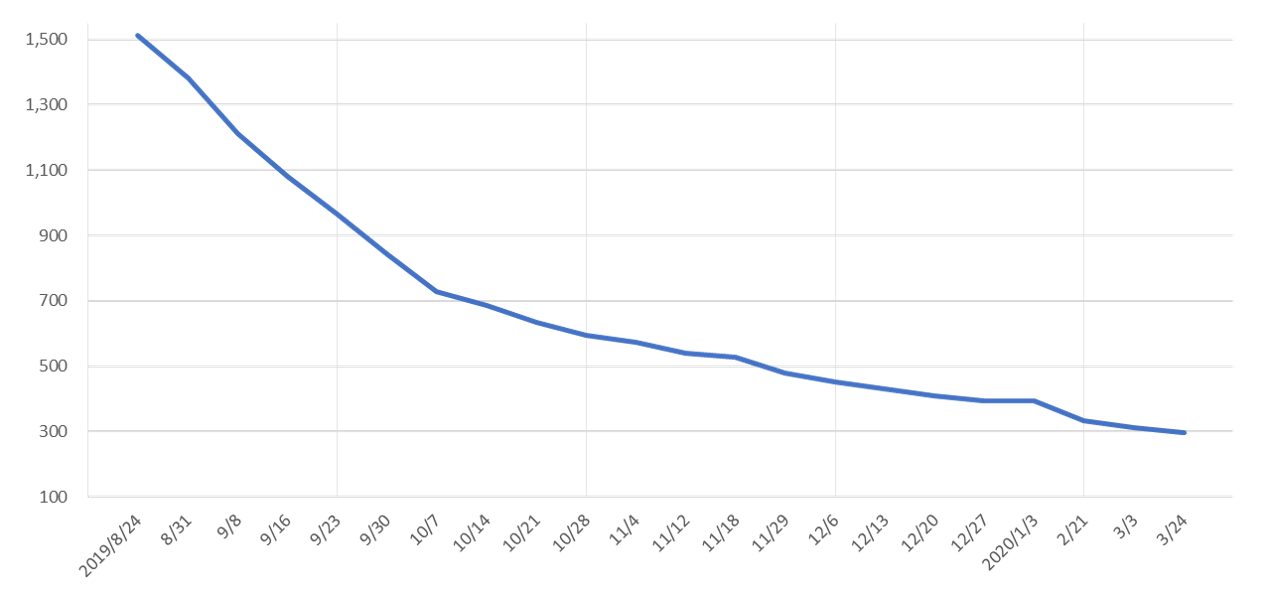
At the beginning, there were 1,511 vulnerable hosts nationwide, but the issue has been addressed in about 80% of the hosts so far, with just 298 remaining as of 24 March 2020. The remaining hosts need to be addressed as soon as possible in order to prevent potential attacks.
In closing
The attacks leveraging the vulnerabilities in Pulse Connect Secure are still ongoing and even combined with ransomware, which may impact the business continuity of organisations.
Especially, CVE-2019-11510 has a potential to develop into a serious threat such as information leakage and compromise as it allows attackers to steal credentials and access to internal network via VPN.
It has the highest CVSS score (10.0) and requires immediate attention.
Use of SSL-VPN products including Pulse Connect Secure has been rapidly increasing for its user-friendliness, and the trend is likely to continue. In order to use the products securely, needless to say, users are expected to apply patches in a timely manner. It is also desired that security level of the product itself increases with features such as multi-factor authentication.
Acknowledgement
JPCERT/CC would like to express sincere gratitude to Bad Packets LLC who have provided useful information regarding the vulnerable hosts running Pulse Connect Secure in Japan.
- Ryosuke Etou, Tomoaki Tani
(Translated by Yukako Uchida)
Appendix A: Appendix A: Suspicious Source IP Address and Hostname
- 151.80.241.108
- 95.216.63.57
- DESKTOP-A41UVJV

