Trends of Phishing Sites Reported to JPCERT/CC
JPCERT/CC receives approximately 19,000 incident reports every year. In 2019, about 56 % of all the reported incidents were categorised as phishing. This time, based on the reported phishing cases, we would like to share the changes in the number of reported cases and trends.
For the purpose of this article, the term “phishing site” refers to a website that is disguised as that of an existing brand in an attempt to steal information including credentials.
Number of phishing sites reported
Figure 1 shows the number of phishing sites that have been reported to JPCERT/CC from 2014 to 2019.
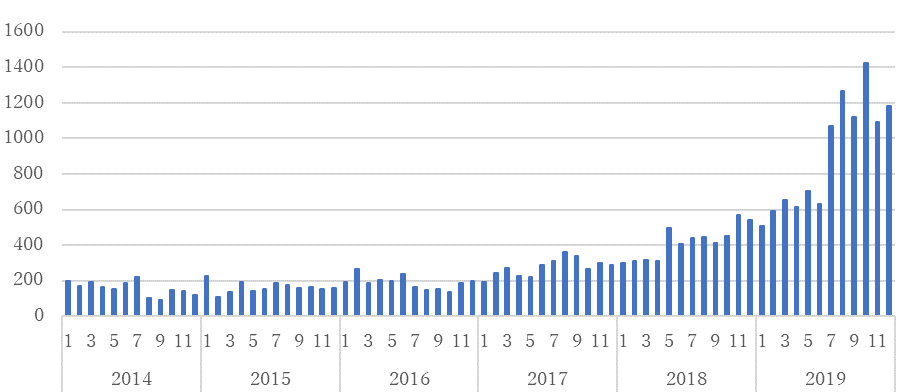
The number had been stable until 2016 with around 200 reported cases every month. However, it slowly grew up over to 1,000 cases per month in July 2019 and continues to sum up until now.
Changes in businesses that are targeted
Let’s take a look at the businesses that are targeted in the phishing sites. Figure 2 describes the ratio of foreign brands that were impersonated in the phishing sites.
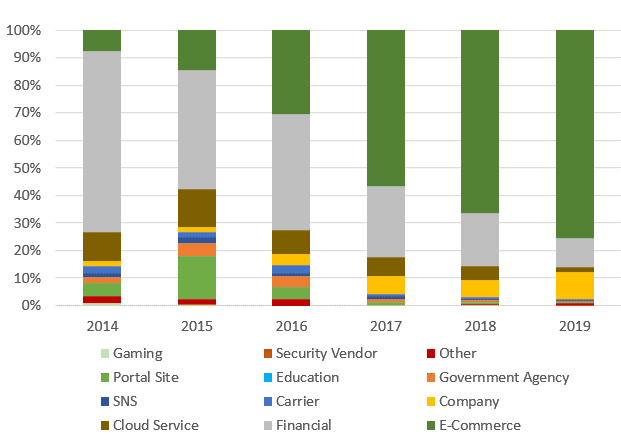
The reason behind the growth in e-commerce is the increase of phishing sites impersonating Amazon and Apple. This also seems to have pushed down the ratio of financial sector overall. However, the number of these phishing sites actually stays stable. In addition, cloud service providers have been one of the usual targets.
Figure 3 shows the breakdown of target businesses in Japanese brands.
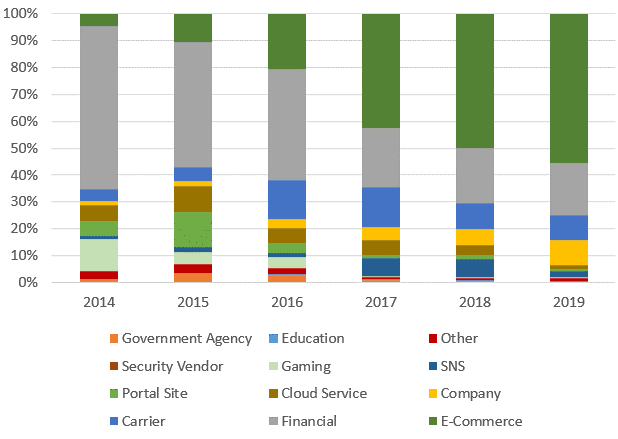
In recent years, major telecom carriers, financial sector and SNS (mainly “LINE”) have been targeted. While there had been many phishing sites of online games (namely “SQUARE ENIX”) between 2014 and 2016, it is rarely active in the last couple of years. The phishing sites on financial sector once scaled down in 2017 but started to increase again in the following year. As of 2019, it was the most targeted sector due to the spread of smishing.
Domains Used in Phishing Sites
Tables 1 shows some examples of domains that were used in actual phishing sites in the past.
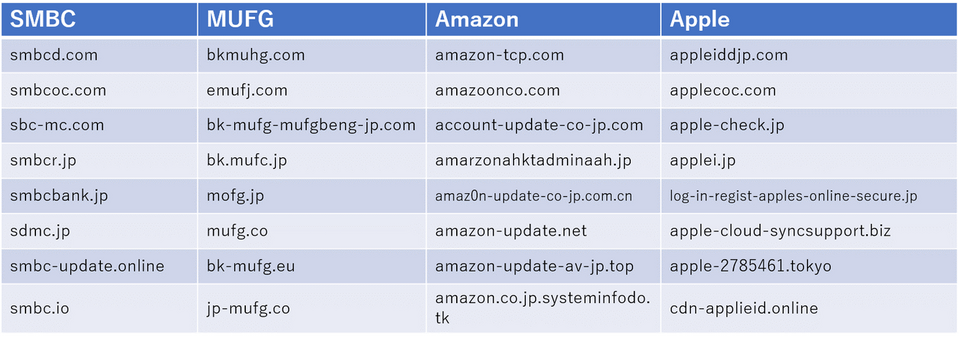
In many cases, it is difficult to spot the difference from the legitimate domain: just a few letters are altered, or a dot is replaced by a hyphen. This makes it difficult for users to determine whether the site is legitimate or not. Some malicious URLs are purposely made long so that the entire domains do not fit within the URL box of smartphone browser. These domains begin with a string that is similar to the legitimate site, followed by some random letters.
More Phishing Sites Using HTTPS
The number of phishing sites using HTTPS is on the rise. Figure 4 represents the ratio of HTTPS sites out of all reported phishing sites from 2014 to 2019. It includes cases where a legitimate site using HTTPS was compromised and running a phishing site within the same infrastructure.
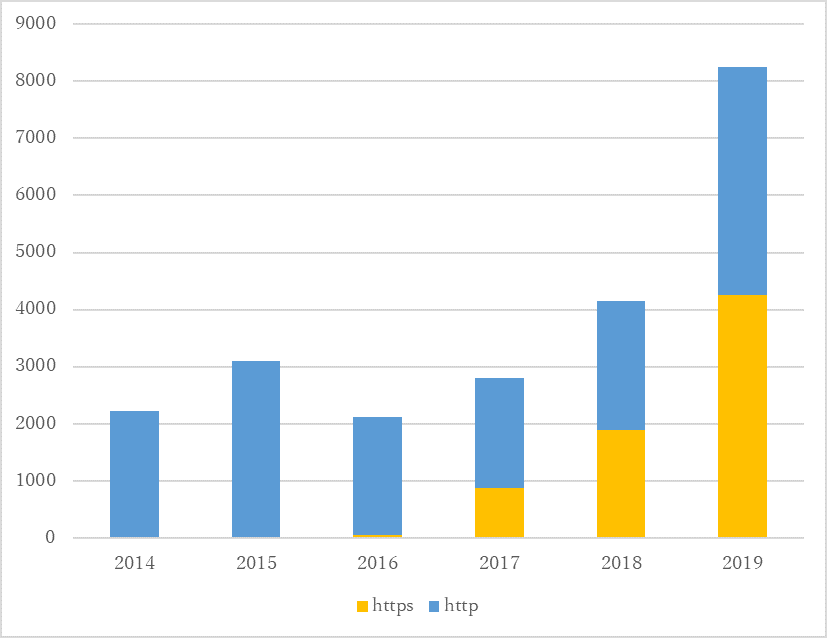
From 2014 through to 2016, most of the reported phishing sites used HTTP. On the other hand, phishing sites using HTTPS started to increase in 2017, and went up to 45% of the entire phishing sites in 2017 and 51% in 2018. Checking for the padlock icon in the address bar or “HTTPS” in the URL is no longer effective to determine whether a it is phishing site or not.
Days until a Phishing Site is Suspended
JPCERT/CC notifies admins of IP addresses and/or domains so that the phishing sites are suspended in a timely manner. Basically JPCERT/CC sends a notification to abuse contacts that are listed on the WHOIS database. If the operator is based in a foreign country/region, we also notify the National CSIRT.
The ratio of active phishing site after the date of notification is described in Figure 5.
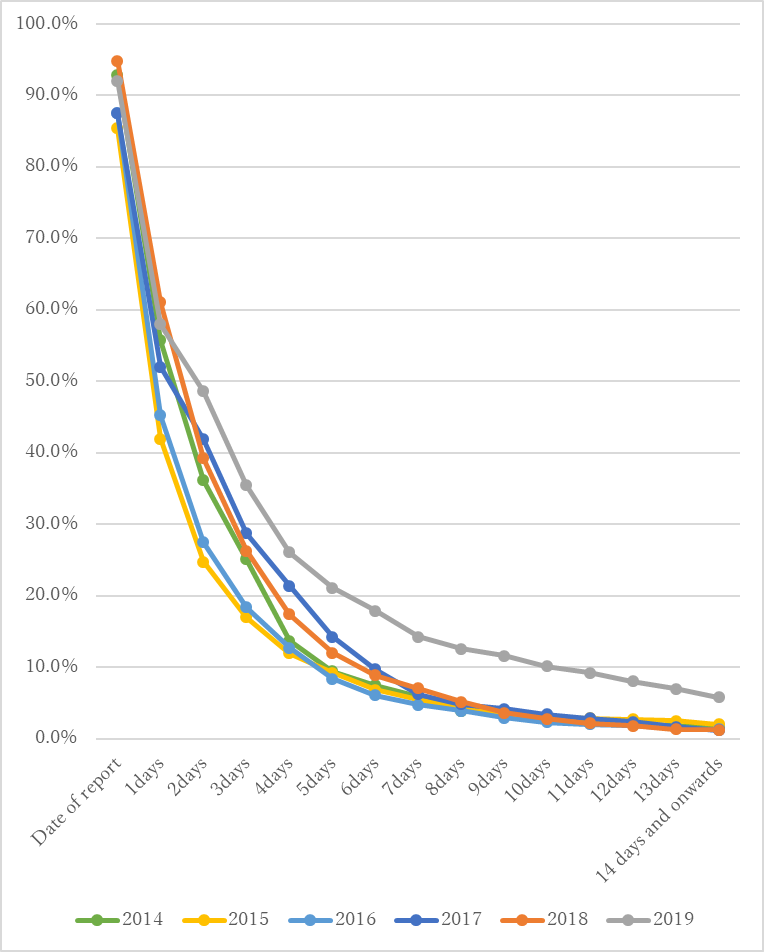
More than a half of phishing sites go inactive within 3 days after the notification. However, the admins of some of the phishing sites do not respond, or the abuse contact is no longer active. Now it takes longer than before until a phishing site is suspended. In 2019, 35% of the phishing sites were still active even 3 days after the notification.
Phishing Site’s Technique to Avoid Detection
One of the reasons behind the slowness is that recent phishing sites have ways to prevent itself from being detected as a malicious site. They have tricks to work as a phishing site to targeted users only, while disguising it as a non-malicious site to other users. Here are some of the techniques being used:
- Redirect to other legitimate sites if the access is made from an IP address outside of Japan
- Redirect to other legitimate site if the user environment is set to a language other than Japanese
- (For smartphone users) Display harmless camouflage contents if the User-Agent is not recognised as smartphone
- Activate the site only during 9am-6pm at Japan Standard Time
When these features are observed, JPCERT/CC notifies admins/National CSIRTs as well.
In closing
We appreciate kind support from ISP/Cloud operators/National CSIRTs etc. in suspending phishing sites. Now, the time we spend to suspend a phishing site is getting longer than before. We hope to continue the cooperation so that we can handle the issue in a timely manner.
As we rely on the WHOIS database when identifying an abuse contact, we would also request operators to maintain the contact information up to date.
If you have any information about malicious contents (e.g. phishing sites, defaced sites), please let us know.
Incident Report https://www.jpcert.or.jp/english/ir/form.html
- Akihiro Sekiguchi, Kazuyuki Watanabe (Translated by Yukako Uchida)

