This blog post focuses on the Day 2 of JSAC2022, following the previous report on the Day 1.An Introduction to macOS Forensics with Open Source SoftwareSpeaker: Minoru Kobayashi (Internet Initiative Japan Inc.)SlidesVideoMinoru provided the basic knowledge of macOS forensics, and its analysis methods using mac_apt, followed by hands-on training on macOS forensics.He mentioned that when it comes to forensics, information is acquired and analysed at the same priority as macOS...
List of “JPCERT/CC”
-
-
JPCERT/CC participated in the cyber exercise “Locked Shields” organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) during 13 – 16 April 2021. We joined as a member of Japan's Blue Team. This article describes how JPCERT/CC and other members participated in Locked Shields, its objectives, the value of the exercise, and challenges. What is “Locked Shields”? Locked Shields is the largest and most complex international live-fire cyber...
-
This blog post focuses on the 1st track of JSAC2021, following the previous reports on the 2nd and 3rd track.Opening Talk: Looking Back on the Incidents in 2020Speaker: Takayoshi Shiigi (JPCERT/CC)Slides (English)VideoTakayoshi opened the JSAC2021 with an overview of incidents that JPCERT/CC confirmed in 2020, focusing on targeted attack and widespread attack.Targeted attack in 2020 is characterised by leveraging cloud services for malware operation in multiple stages of attacks from...
-
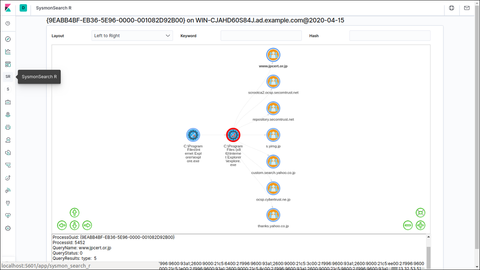
SysmonSearch is a tool developed by JPCERT/CC to analyse event logs generated on Sysmon (a Microsoft tool). https://github.com/JPCERTCC/SysmonSearch SysmonSearch is now compatible with Elastic Stack 7.x. Please note that the new version no longer supports Elastic Stack 6.x versions. This article introduces the new version of SysmonSearch, changes from the previous versions and new functions. Elastic Stack updates Kibana There was a change in Kibana plug-in due to the updates...
-
Following the previous article, we continue with the summary of the second half of the ICS Security Conference 2020 program. The Trend in Standardization of ICS Security System -The Introduction and Updates of IEC 62443- By Junya Fujita (Center for Technology Innovation, Control Platform Research Development, Hitachi, Ltd) Slides (Japanese only) In this presentation, the overview of and the updates on IEC 62443, which is the standard in ICS security,...
-
On February 14, 2020, JPCERT/CC held ICS Security Conference 2020 at Asakusabashi Hulic Hall. This conference aims at improving security measures and best practices of ICS through sharing threat trend against ICS in Japan and the world as well as the latest security activities conducted in related industries and enterprises. 307 people participated in the event this year. This blog entry and the next one introduce the summary of the...
-
Following the JSAC Part 1, we continue with the summary of the second ...
-
In the past articles, we have introduced TSCookie and PLEAD, the malware used by an attack group BlackTech. We have confirmed that this group also uses another type of malware called “IconDown”. According to ESET’s blog[1], it has been confirmed that the malware is distributed through the update function of ASUS WebStorage. This article describes the details of IconDown found in Japanese organisations. IconDown’s behaviour The malware downloads a file...
-
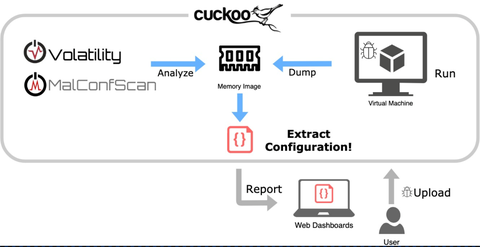
In malware analysis, extracting the configuration is an important step. Malware configuration contains various types of information which provides a lot of clues in incident handling, for example communication details with other hosts and techniques to perpetuates itself. This time, we will introduce a plugin “MalConfScan with Cuckoo” that automatically extracts malware configuration using MalConfScan (See the previous article) and Cuckoo Sandbox (hereafter “Cuckoo”). This plugin is available on GitHub....
-
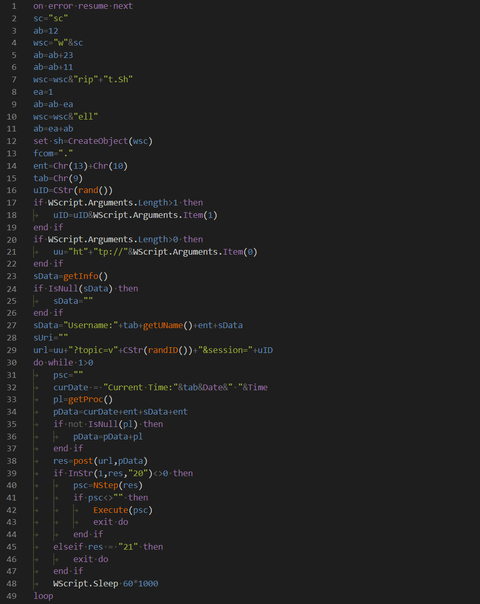
As of June 2019, JPCERT/CC has observed targeted emails to some Japanese organisations. These emails contain a URL to a cloud service and convince recipients to download a zip file which contains a malicious shortcut file. This article will describe the details of the attack method. How the VBScript downloader is launched The zip file downloaded from the URL in the email contains a password-protected decoy document and a shortcut...