Greetings. This is Aki Hitotsuyanagi from ICS Security Response Group. Today, I would like to introduce to you our new document, “Cyber Security First Step for Introducing IIoT to the Factory -Security Guide for Businesses Implementing IIoT-“.The original Japanese version of this document was released August 2018 and has been receiving favorable reviews. IIoT, or Industrial Internet of Things refers to use of IoT in industrial sectors. For example, using...
List of “JPCERT/CC”
-
-
xin chào! (“Hello” in Vietnamese) This is Katsuhiro Mori from Cyber Me...
-
Following the JSAC2019 Part 1, this article will provide overview of the latter half of the conference. We also uploaded the photos from the conference on Flickr. “Sextortion Spam Demanding Cryptocurrency” by Chiaki Onuma (Kaspersky) Presentation material (Japanese) Sextortion spam is a campaign distributing spam emails in which adversaries aim to extort money (e.g. bitcoin) by threatening recipients by means of sexual contents. Ms. Onuma shared the outcome of her...
-
JPCERT/CC organised Japan Security Analyst Conference 2019 (JSAC2019) on 18 January 2019 in Ochanomizu, Tokyo. This conference targets front-line security analysts who deal with cyber incidents on a daily basis, with an aim to create a venue for sharing technical information which helps them better handle ever-evolving cyber attacks. This is the second run of the event following the first one in 2018, and 291 participants attended. In this event,...
-
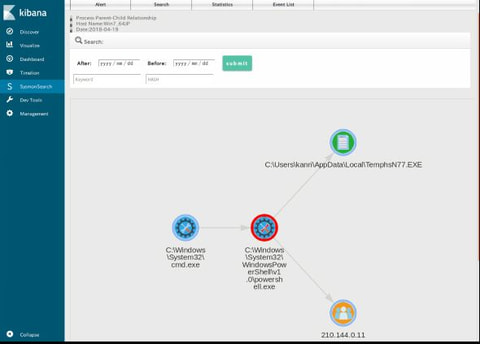
In a past article in September 2018, we introduced a Sysmon log analysis tool "SysmonSearch" and its functions. Today, we will demonstrate how this tool can be used for incident investigation by showing some examples. To install SysmonSearch, please see the following page: JPCERTCC GitHub · SysmonSearch Wiki https://github.com/JPCERTCC/SysmonSearch/wiki The case study was conducted in the following environment: Sysmon 7.0.1 ElasticSearch 6.2.2 Kibana 6.2.2 Winlogbeat 6.2.2 Browser: Firefox Example of...
-
Hello, I am Katsuhiro Mori from Cyber Metrics Line, Global Coordination Division. JPCERT/CC released ”Mejiro” (Internet risk visualisation service) English website in August 2018. This web service collects publicly available risk data on risk factors existing on the Internet and provides index for each economy. To promote the use of this tool service and cyber space clean-up activities, I went to Mongolia and Indonesia recently. What is Mongolia like? When...
-
In recent sophisticated cyber attacks, it is common to observe lateral movement, where a malware- infected device is used as a stepping stone and further compromise other devices in the network. In order to investigate the compromised devices, it is necessary to retain detailed logs of the applications that run on the device on a daily basis. One of the well-known tools for this purpose is Sysmon [1] from Microsoft,...
-
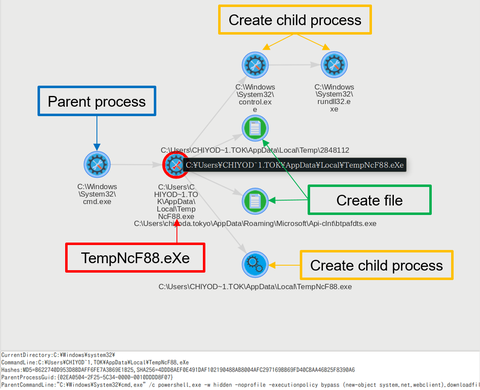
JPCERT/CC has observed some Japanese organisations being affected by cyber attacks leveraging “Cobalt Strike” since around July 2017. It is a commercial product that simulates targeted attacks [1], often used for incident handling exercises, and likewise it is an easy-to-use tool for attackers. Reports from LAC [2] and FireEye [3] describe details on Cobalt Strike and actors who conduct attacks using this tool. Cobalt Strike is delivered via a decoy...
-
Today, I would like to introduce an activity at the Vulnerability Coordination Group of JPCERT/CC.It is a method to describe a vulnerability using Vulnerability Description Ontology (VDO). JPCERT/CC receives software vulnerability information from domestic and overseas reporters, then coordinates them in between the vendor/developer and the reporter. While there is a vulnerability reporting template, vulnerability itself is described in a free format. Reporter can describe about a vulnerability in a...
-
JPCERT/CC has been coordinating and disclosing software vulnerabilities under the "Information Security Early Warning Partnership" since 2004. We have coordinated and disclosed over 1,500 vulnerabilities with developers as of the end of 2017. The "Information Security Early Warning Partnership" has a guideline that serves as a framework for how vulnerabilities are coordinated within Japan. An overview of the framework including how reported vulnerabilities are coordinated and disclosed is provided at...