How to Describe Vulnerability Information?
Today, I would like to introduce an activity at the Vulnerability Coordination Group of JPCERT/CC.
It is a method to describe a vulnerability using Vulnerability Description Ontology (VDO).
JPCERT/CC receives software vulnerability information from domestic and overseas reporters, then coordinates them in between the vendor/developer and the reporter. While there is a vulnerability reporting template, vulnerability itself is described in a free format. Reporter can describe about a vulnerability in a way they like. From a vulnerability coordinator's perspective, the following are a few obstacles that we are facing:
1. It is necessary to "understand" the technical aspects
For example, the description in CVE for the vulnerability CVE-2014-8606 is as follows:
Directory traversal vulnerability in the XCloner plugin 3.1.1 for WordPress and 3.5.1 for Joomla! allows remote administrators to read arbitrary files via a .. (dot dot) in the file parameter in a json_return action in the xcloner_show page to wp-admin/admin-ajax.php.
When reading this information, the following technical details can be extracted:
- (Affected) Products and Versions
- Xcloner plugin 3.1.1 (for WordPress)
- Xcloner plugin 3.5.1 (for Joomla!)
- Vulnerability type: Directory traversal
- Root cause: the parameter "file" is not validated
- Attacker: Remote authenticated attacker
- Impact: Arbitrary file read
There is no unique way to articulate the technical aspects of a vulnerability. A free format allows various reporters to describe a vulnerability using their own way. In some cases, there may be redundant information, or in other cases, not enough information.
2. When the vulnerability description is written in your non-native language, it can be extremely difficult to comprehend
A lot of vulnerability information is published in English, so organizations who do not have any English speaker may have a difficulty in comprehending a vulnerability due to the language barrier. In addition, various sources are now publishing vulnerability information, and lots of non-English vulnerability information are publicly available.
For example, CNNVD in China provides vulnerability information only in Chinese.
To overcome these issues, the National Institute of Standards and Technology (NIST) in US has proposed the creation of Vulnerability Description Ontology (VDO).
- NISTIR 8138 (DRAFT) Vulnerability Description Ontology (VDO): a Framework for Characterizing Vulnerabilities
https://csrc.nist.gov/publications/detail/nistir/8138/draft
VDO provides basic building blocks to describe a vulnerability so that a vulnerability can be described without using a free format.
Below is an example of the vulnerability (CVE-2014-8606 from above) described using the VDO (taken from NIST IR 8138 - Appendix A)
Vulnerability: cve.mitre.org CVE-2014-8606
Provenance: http://www.vapid.dhs.org/advisories/wordpress/plugins/Xcloner-v3.1.1/
Scenario: 1
Type: cve.mitre.org CWE-22
Products:
cpe.nist.gov
cpe:2.3:a:xcloner:xcloner:3.1.1:*:*:*:*:wordpress:*:*
cpe:2.3:a:xcloner:xcloner:3.5.1:*:*:*:*:joomla\!:*:*
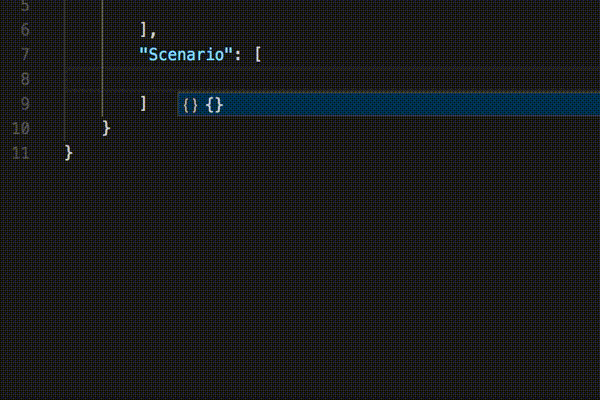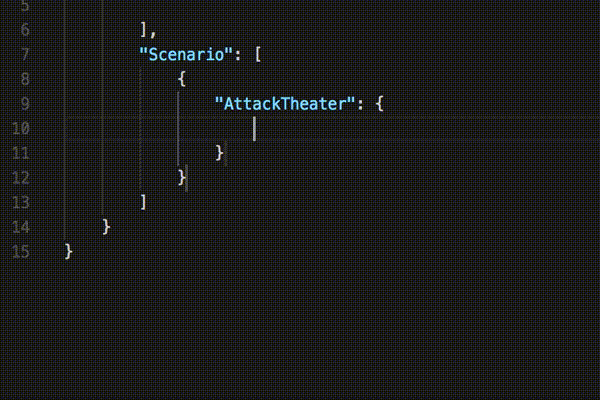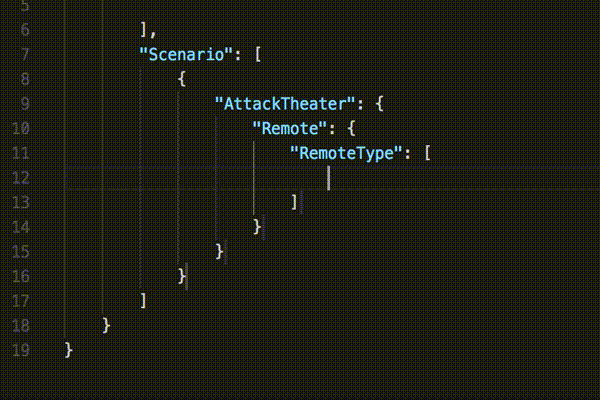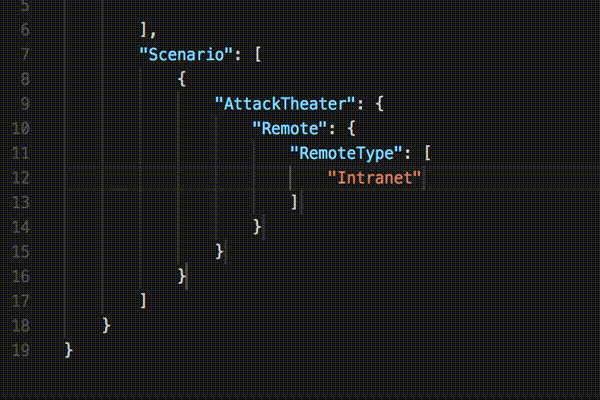
Attack Theater: Remote
Remote Type: Internet
Barriers: Privilege Required
Privilege Level: Administrator
Relating to Context: Application
Context: Application
Entity Roles: Primary Authorization
Entity Roles: Vulnerable
Impact Method: Trust Failure
Trust Failure Type: Failure to Verify Content
Logical Impact: Read(Direct)
Scope: Limited
Criticality: Low
Context: HostOS
Entity Roles: Secondary Authorization
Impact Method: Code Execution
Logical Impact: Read(Direct)
Scope: Limited
Criticality: HighWhile VDO is still in a draft phase. I believe that it has a huge potential to
- Provide a common language for understanding and exchanging information on vulnerabilities
- Provide a format to automatically manage vulnerability information
JPCERT/CC is currently attempting to see if describing vulnerabilities using VDO can make the vulnerability coordination operations more efficient.
The following shows how vulnerability information can be entered into the VDO format using an editor.
Currently, we have implemented a JSON Schema to enter the Noun Groups defined in NISTIR 8138 in a simple manner to test whether this can be used in a practical manner.
More details on this attempt to make vulnerability coordination more efficient through the VDO will be presented at the 30th Annual FIRST Conference.
- 30th Annual FIRST CONFERENCE
"Removing the Pain From the Repetitive Processing of Vulnerability Reports Using a Vulnerability Ontology", Masanobu Katagi (JPCERT/CC, JP), Takayuki Uchiyama (JPCERT/CC, JP), Masaki Kubo (NICT, JP)
If you are interested in VDO and its application, please contact us at vultures [at] jpcert.or.jp.
- Masanobu Katagi

