TSUBAME Report Overflow (Jul-Sep 2021)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports do not cover. This article covers the monitoring results for the period of July to September 2021. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here.
Scan packets from Russia increased
From Russia, there were accesses to a variety of ports, including port numbers not normally used by public servers. Nothing was unique about these destination port numbers, and we have observed such accesses with a wide range of sensors. There were multiple source IP addresses, not only multiple ports. TSUBAME is following about 60 source IP addresses that appear to be related to this scan, and most of them are in the following IP address ranges.
- 45.146.164/24
- 45.155.205/24
If you search for public information about the above IP address ranges, you will find that various port scans and vulnerability scans have been reported in the past[1][2]. The relationship between them is unknown at this point, but these scans should also be noted. Since scans have a variety of purposes and backgrounds, not all scans should be regarded as fraudulent. In Japan, some scans are conducted for research purposes or security alerts for the public. You should be aware of the existence of such various kinds of scans when using the Internet.
Packets that exploit Redis (6379/TCP)
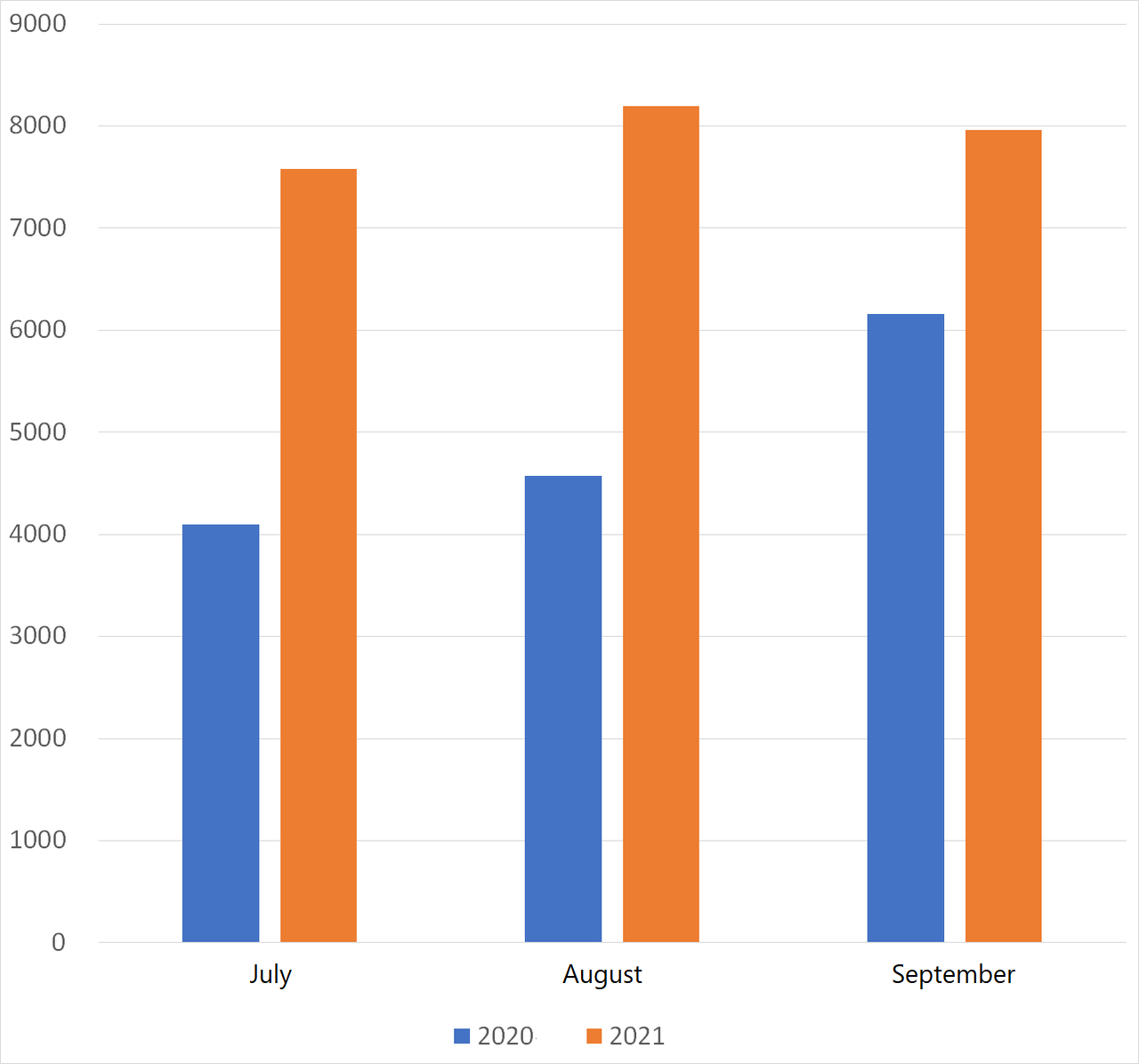
In the analysis of packets to port 6379/TCP in the report, not only TSUBAME but also honeypots under demonstration testing were used in combination. These packets are not a new discovery in particular, and it has the same characteristics as those already reported by Palo Alto Networks and others [3][4]. JPCERT/CC's observations also shows that the characteristics of the source IP addresses and packet that communicated with the honeypots match with those in the said report, and we found several patterns. However, in any cases, the method that leads to exploit is similar. Using methods such as registering a cron task via Redis, a malicious script on a download site that the attacker prepared is downloaded and executed. Considering the changing number of scans observed by TSUBAME (JPCERT/CC Internet Threat Monitoring Report [July 1, 2021 - September 30, 2021], see Figure 3), if Redis is installed and left without any particular caution, it is expected that the host would be exposed to attack packets within a short period of time after installation, even less than a day. Therefore, you must be careful of the initial configuration when installing and using Redis. It is recommended to properly configure and test the access restrictions to Redis before using it. Administrators who are already using Redis should check once again whether any unrecognized cron task, malicious file, or process is running. Comparison of domestic and overseas monitoring trends Figures 1 and 2 show a monthly comparison of the average number of packets received per day by a single sensor in Japan and overseas. More packets were observed by the overseas sensors than domestic sensors. Both domestic and overseas sensors received more packets in each month this year than in the same month last year.
 |
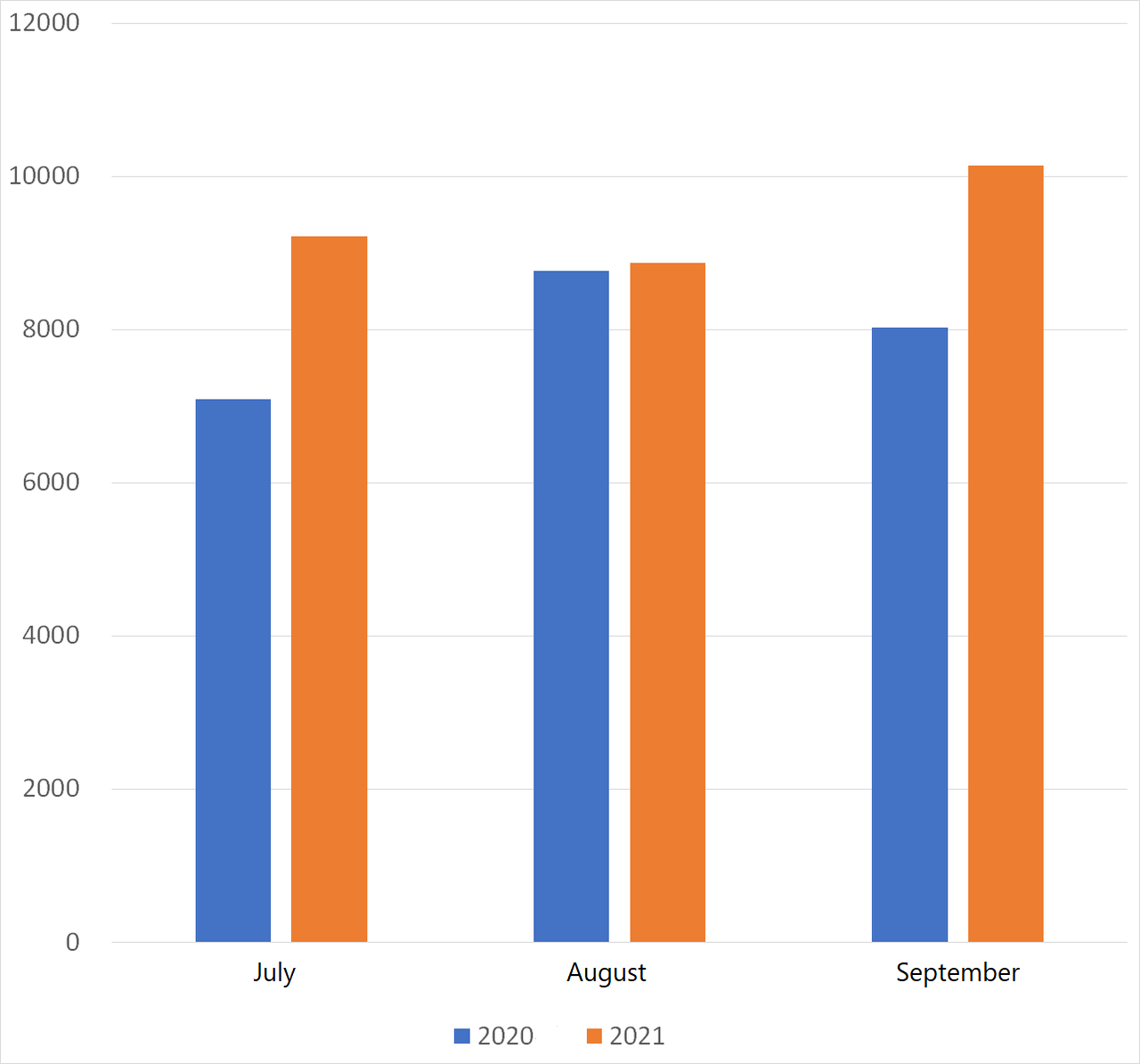 |
| Figure 1: Average number of packets to domestic sensors | Figure 2: Average number of packets to overseas sensors |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Now we check if there is any difference in the observation results between sensors. Table 1 shows the top 10 packets received by each sensor in Japan and overseas. Packets to port 2375/TCP and 2376/TCP, which is for Docker, were observed in a wide range of sensors although they did not rank in the top 5. Packets to port 5060/UDP, which is for SIP, were also observed in overseas sensors, and this leads the difference in trends between Japan and overseas.
Table 1: Comparison of top 10 packets by domestic and overseas sensors
| #1 | #2 | #3 | #4 | #5 | #6 | #7 | #8 | #9 | #10 | |
| Domestic sensor1 | 23/TCP | 6379/TCP | 22/TCP | 445/Tcp | 80/TCP | ICMP | 123/UDP | 443/TCP | 2375/TCP | 2376/TCP |
| Domestic sensor2 | 23/TCP | 6379/TCP | 22/TCP | 445/TCP | 80/TCP | 443/TCP | 2375/TCP | 1433/TCP | 81/TCP | 2376/TCP |
| Domestic sensor3 | 6379/TCP | 23/TCP | 22/TCP | 80/TCP | 445/TCP | 443/TCP | 2375/TCP | 5060/UDP | 81/TCP | 1433/TCP |
| Overseas sensor1 | 6379/TCP | 80/TCP | 443/TCP | ICMP | 2375/TCP | 2376/TCP | 81/TCP | 8080/TCP | 5555/TCP | 5060/UDP |
| Overseas sensor2 | 6379/TCP | 23/TCP | 22/TCP | 80/TCP | 443/TCP | 81/TCP | 1433/TCP | 2375/TCP | 3389/TCP | 8080/TCP |
| Overseas sensor3 | 23/TCP | 445/TCP | 6379/TCP | 22/TCP | 80/TCP | 1433/TCP | 443/TCP | 139/TCP | 5060/UDP | 5555/TCP |
In closing
Internet threat monitoring is one of the activities that are difficult for individuals to continuously conduct because it requires maintenance of nodes and regular log analysis. JPCERT/CC does not focus only on TSUBAME but also exchange information with various members both in Japan and overseas who are engaged in similar efforts. Through these activities, we detect incidents at an early stage and help related entities to solve the issue. As for vulnerable devices observed by TSUBAME and other methods, we share a part of the information with the relevant product vendors. Although we did not issue any special security alert during this quarter, please note the above issue regarding Redis when using the Internet. We will continue to publish blog articles on a regular basis as Internet Threat Monitoring Reports are released. In case of any unusual changes, we may publish an extra issue. Your feedback on this series is much appreciated. Please use the below comment form to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano (Translated by Takumi Nakano)
References
[1] Twitter
BadPackets (@bad_packets)
https://twitter.com/bad_packets/status/1371159404041564161
[2] Twitter
! 1 IoTa (@1IoTa3)
https://twitter.com/1IoTa3/status/1371370763668758530
[3] Palo Alto Networks
Updated: New Evidence Emerges to Suggest WatchDog Was Behind Crypto Campaign
https://unit42.paloaltonetworks.jp/teamtnt-cryptojacking-watchdog-operations/
[4] Trend Micro
Exposed Redis Instances Abused for Remote Code Execution, Cryptocurrency Mining
https://www.trendmicro.com/en_us/research/20/d/exposed-redis-instances-abused-for-remote-code-execution-cryptocurrency-mining.html

