Japan Security Analyst Conference 2021 -1st Track-
This blog post focuses on the 1st track of JSAC2021, following the previous reports on the 2nd and 3rd track.
Opening Talk: Looking Back on the Incidents in 2020
Speaker: Takayoshi Shiigi (JPCERT/CC)
Takayoshi opened the JSAC2021 with an overview of incidents that JPCERT/CC confirmed in 2020, focusing on targeted attack and widespread attack.
Targeted attack in 2020 is characterised by leveraging cloud services for malware operation in multiple stages of attacks from intrusion to lateral movement. The speaker explained attacks using malware LODEINFO and the activity of Lazarus group. LODEINFO is frequently updated, and its functions and commands have been modified. On the other hand, the malware used by Lazarus loads its configuration from a registry and communicates with C&C servers using device-specific information. For this reason, the speaker suggested that analysis combined with forensics is required in investigating the devices in this particular case.
Widespread attack in 2020 includes the activity of Emotet and attacks exploiting vulnerabilities in SSL VPN products. JPCERT/CC continues sharing and updating information related to these malicious activities.
GhostDNSbusters: Tracking and Responding to a Large Scale DNS Hijacking Campaign
Speaker: Josh Hopkins (Team Cymru), Manabu Niseki
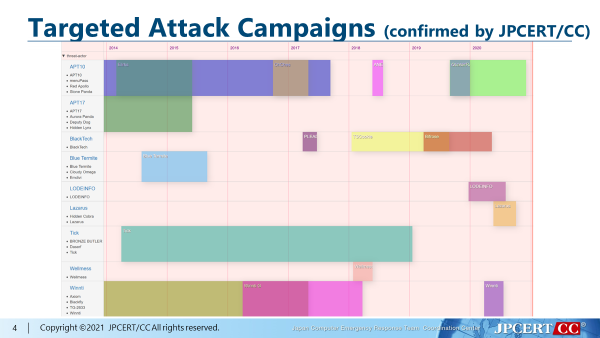
Manabu and Josh presented tracking techniques for a large-scale attack campaign using a DNS hijacking tool kit called GhostDNS and other measures that they took to mitigate the malicious activity. They introduced two methods for hunting GhostDNS infrastructures: passive approach and active approach.
In the passive approach, the speakers used search engines and found DNS changers located in open directories. This method worked GhostDNS because its files and directories have unique names. They collected the IP addresses used by GhostDNS and revealed that these belonged to well-known cloud or hosting service providers.
In the active approach, the speakers used scanners to identify rogue servers and find phishing websites in a specific IP range.
After these approaches, the speakers conducted the traffic analysis of the DNS changers to find further infrastructures and victims. They discovered the IP addresses of the attackers’ rogue DNS servers from the victims’ IP addresses. After repeating this process, they eventually found 50 changer IP addresses, 4 rogue DNS servers, and thousands of victims.
The tools introduced in the presentation are available at GitHub.
rogue_one
https://github.com/ninoseki/rogue_one
dnsx
https://github.com/projectdiscovery/dnsx
httpx
https://github.com/projectdiscovery/httpx
rangescan
https://github.com/ninoseki/rangescan
Accelerating the Analysis of Offensive Security Techniques Using DetectionLab
Speaker: Chris Long (Netflix)
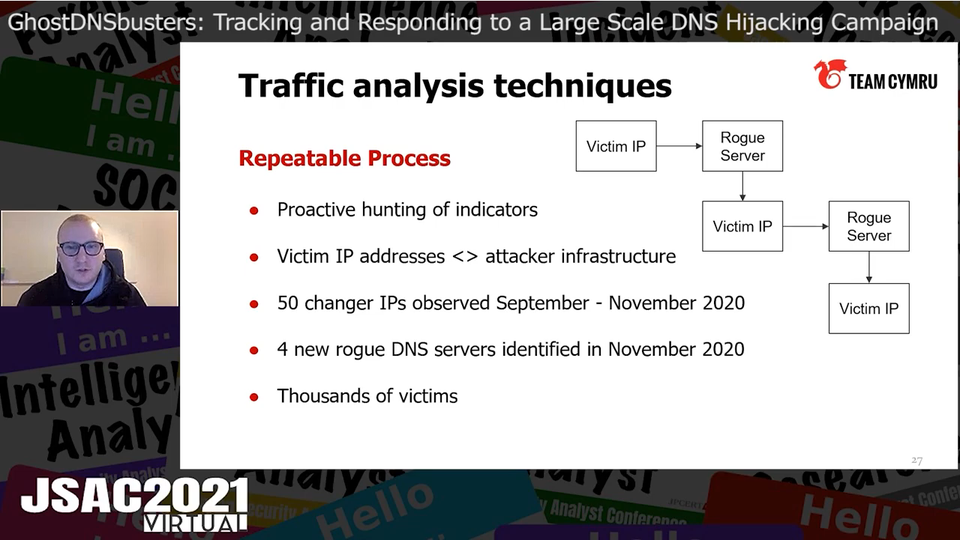
Chris presented DetectionLab, a repository that automates the setup process of an Active Directory environment for malware analysis based on free tools. DetectionLab creates the following environments:
- Logger
- Domain Controller (DC)
- Windows Event Forwarding (WEF)
- Windows10
Logger environment manages logs such as osquery logs for DC, WEF and Windows10, and Windows Event Logs. It also contains preinstalled tools for log analysis such as Splunk. Among them, Velociraptor performs code execution and forensics of MFT, memory images and browser history.
In addition, the speaker illustrated possible use scenarios, in which DetectionLab is used to detect Mimikatz execution and process injection. The tools preinstalled in DetectionLab enables such detection.
When you gaze into the Bottle,...
Speaker: Rintaro Koike, Hajime Takai (NTT Security Japan)
Rintaro and Hajime discussed Bottle Exploit Kit and malware Cinobi, both targeting users in Japan.
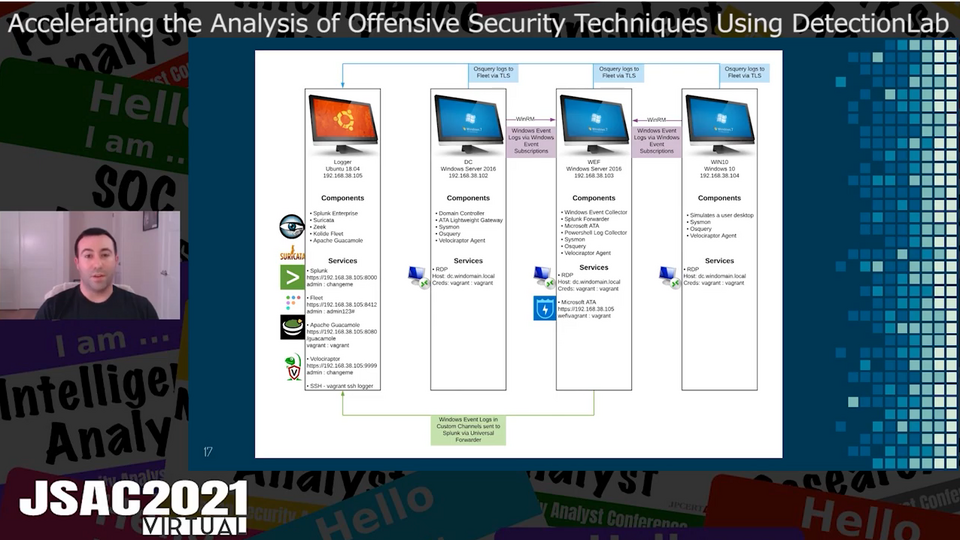
They mentioned that the activity to infect users with Cinobi using Bottle Exploit Kit was first observed in September 2019 and that it was still active in 2020. This exploit kit has functions, such as checking browser’s language settings and time zone, to specifically target users in Japan. This exploit kit has been updated to version 2, which downloads the encoded malware.
Cinobi is a banking trojan with four components. The speakers revealed that it decodes and executes shellcode and uses TOR to communicate with the C&C server. The difference between Version 1 and 2 was detailed in the presentation.
Based on the analysis results of Bottle Exploit Kit and Cinobi, they introduced the following techniques to prevent infection:
- Detection on the network
- Detection by behaviours on the device
- Detection based on Yara Rule
Lastly, the speakers mentioned that this attack activity could be related to another phishing campaign and an attack group “Magecart.” This is because Cinobi Version 1 was distributed via phishing sites, and some of the IP addresses and C&C server information matched those used by this attack group.
IoC information is listed in the Appendix of the presentation material.
A Certain Emotet Campaign - Impact in Japan-
Speaker: Ken Sajo (JPCERT/CC), Shuhei Sasada (Cyber Defense Institute Inc.)
Ken and Shuhei presented the observation results of malware Emotet conducted by their special interest group for tracking spam.
The speakers mentioned that emails leading to Emotet infection have been distributed in Japan since September 2019. They introduced a flow of Emotet infection to show that email-related information of victims is stolen and exploited for further spread. They categorised attackers’ emails as follows:
- Widely distributed email
- Reply email
- Fake reply email
The observation results also showed that two different groups are involved in the attacks. The first group spreads Emotet infection and infects the victims with another type of malware. The second group conducts attacks with the latter malware and pays royalties to the first group. The following types of malware are used for secondary infections:
- Ursnif
- Trickbot
- Qakbot
- Zloader
- IcedID
Grasping a Big Picture of Shathak Attack Campaign
Speaker: Takuma Matsumoto (LAC Co., Ltd.), Shotaro Hamamoto (NEC Solution Innovators, Ltd.), Yusuke Niwa (Itochu Corporation), Ryo Tamura (Secure Brain Corporation), Shuhei Sasada (Cyber Defense Institute, Inc.)
Takuma and Shotaro presented an overview of an attack group called Shathak, which targets multiple countries including Japan.
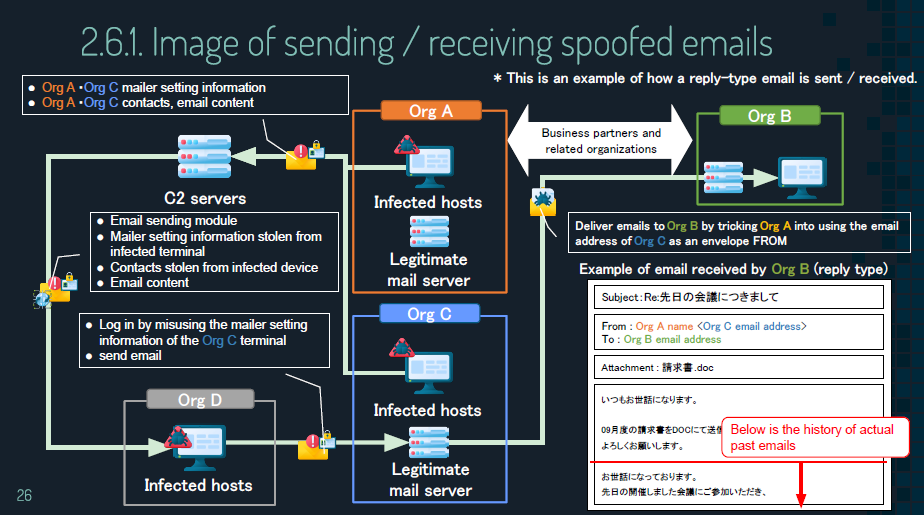
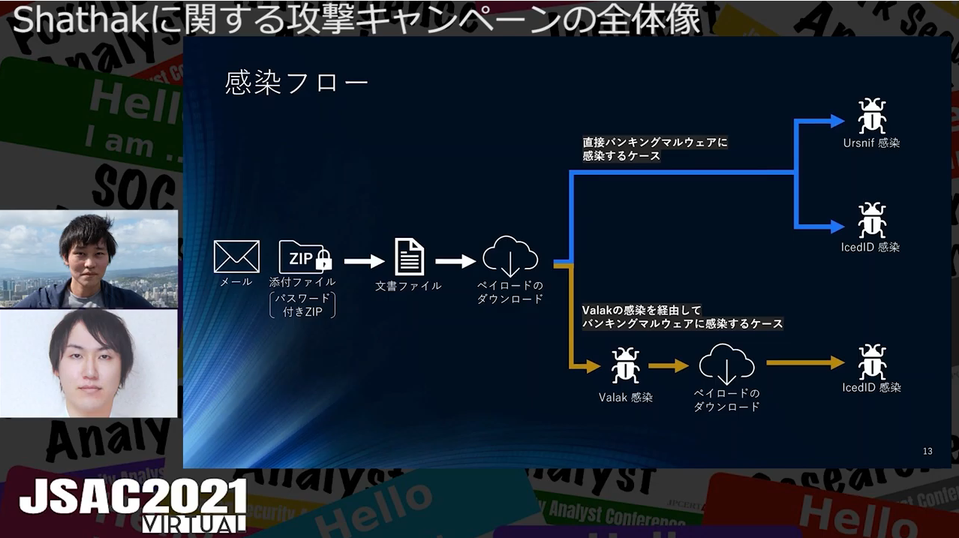
The speakers first described the basic features and strategies of Shathak. The attackers leverage the email account information they obtained, disguise themselves as a non-malicious entity, send emails to the target as if it is a reply from the entity. The emails contain a malicious document in a ZIP file protected with a password, which is written in the email body. Downloading payload embedded in the document file leads to infection of the following types of malware, which were respectively detailed in the presentation:
- Valak
- Ursnif
- IcedID
According to the analysis result, the features of the document file have been changing since 2018, and LOLBAS (Living Off The Land Binaries and Scripts) is heavily used recently. The communication pattern is becoming more complicated from October 2020. The IP address of the device, which tries to access the payload, is checked by the attacker. If it is located in the targeted country, malicious payload is delivered. The IP address of the device, which tried to access the payload, is checked whether it matches the targeted country, and the payload may be delivered depending on the result.
Finally, the speakers explained the connection between Shathak and other attack groups in terms of the following:
- Features of C&C server domain names
- Similarities with other document files
- Other attack cases using IcedID
- Similarities in the websites that are subject to Web injection
A Picture of Business Email Compromise Triggered by A Security Breach at Business Partners
Speaker: Takeshi Teshigawara, Kenzo Masamoto (Macnica Networks Corp.)
Takeshi and Kenzo presented on actual Business Email Compromise (BEC) cases triggered by security breach of a business partner including countermeasures against BEC based on the experience and some tips for incident response.
The speakers compared the techniques used in BEC cases arising from email exchanges between a buyer and a compromised seller. Misuse of free email services and Man-in-the-email attack were described.
First, misuse of free email service was addressed by the speakers. Attackers first obtain a buyer’s information by compromising a seller’s email account. Then, they pretend to be the seller and send a notification to the buyer, saying that seller’s bank account information has changed. The speakers found that attackers created fake accounts on two different email services: one is for sending disguised emails as the seller, and the other is for receiving replies from with the buyer.
Next, Man-in-the-email technique was discussed. The attackers first obtain a buyer’s information by compromising a seller’s email account and then send a notification to the seller from the attackers’ email infrastructure, saying that their bank account information has changed. The speakers found that attackers used two different email infrastructures: one is to communicate with the seller, and the other with the buyer.
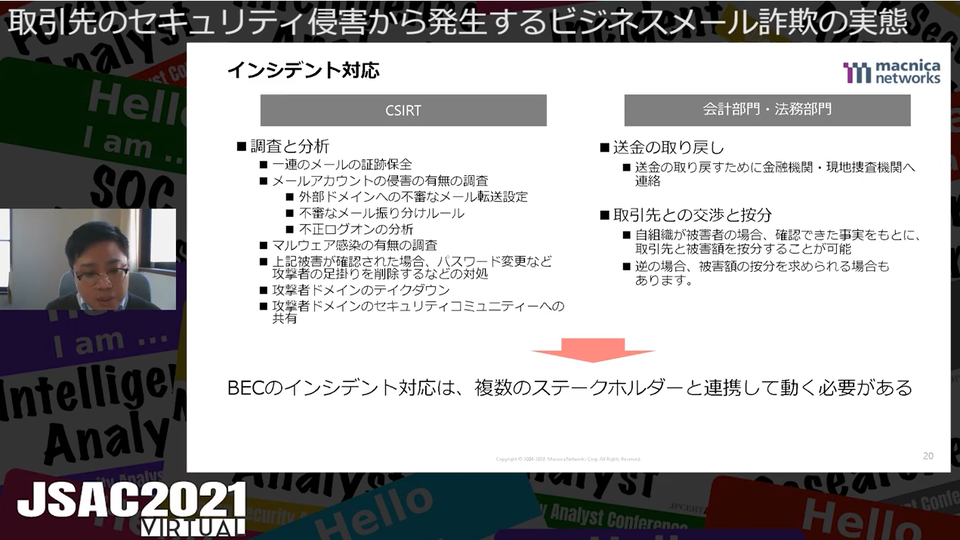
Lastly, the speakers pointed out that even if a company applies robust security measures, it may be subject to BEC due to the low level of security measures taken by business partners. Furthermore, they added that emails from attackers often pass the SPF (Sender Policy Framework) authentication and that this makes them difficult to be detected by Security Email Gateway. The presentation concluded that countermeasures against BEC must be developed not only by IT department but also with accounting and legal department.
NanoCoreHunter: Track NanoCore C&C Server and Monitor RAT Operator for 180 Days
Speaker: Takashi Matsumoto (National Institute of Information and Communications Technology)
Takashi presented the tracking activities of NanoCore C&C servers and the results of an experiment to attract its operators. NanoCore is one of the Remote Access Trojans (RAT), which first appeared in 2013 and is still widely used. It has some functions such as:
- Screen sharing
- Data exfiltration (files, passwords, etc.)
- Keylogger
- Access to microphones, web cameras, etc.
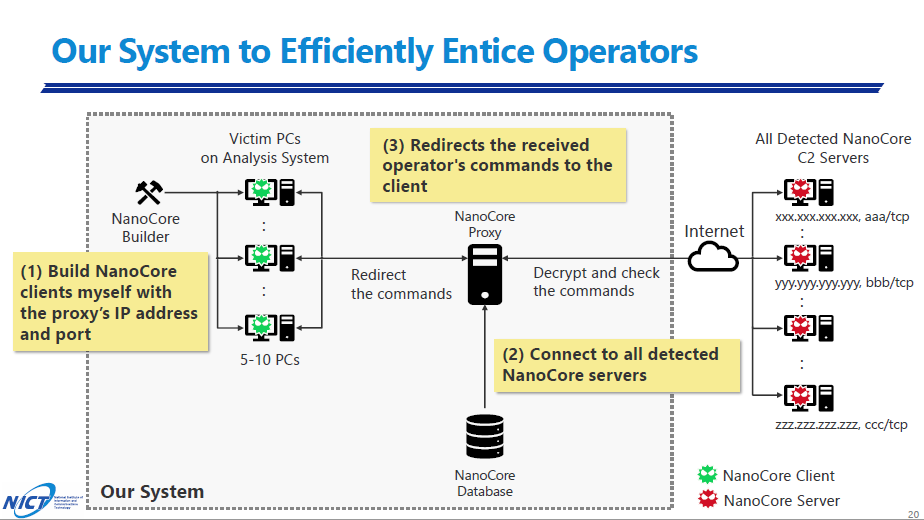
The results of the long-term observation showed that most C&C servers were located in the United States and Europe. The speaker next explained about his experiment of attracting its operators to the test environment in order to reveal their purpose of the operation. He confirmed 88 cases of successful intrusion by the operators. He also described the operators’ malicious behaviour such as stealing email account credentials by means of screen share and executing another type of malware. Moreover, the following operator actions were detailed in the presentation.
- Share the screen and steal passwords
- Carefully check the browser and mailer
- Attempt to infect multiple RATs
In Closing
On 19 February, we held “After JSAC2021” to honour the best speakers. Based on the feedback from participants, the CFP review board members selected Ken Sajo (JPCERT/CC) and Shuhei Sasada (Cyber Defense Institute Inc.). Their presentation “A Certain Emotet Campaign - Impact in Japan-” was highly valued by the audience for its comprehensive explanation of Emotet with some useful information for researchers.

We would like to take this opportunity to thank everyone who joined JSAC2021 and who read this series of reports.
Kengo Teramoto
(Translated by Masa Toyama)

